What Is Threat Hunting?

Threat hunting has become an increasingly important aspect of cybersecurity, as organizations strive to identify and mitigate security incidents that automated systems may have missed. Yes, the definition of threat hunting can vary, and it generally involves a combination of manual and machine-assisted processes driven by human curiosity and pattern recognition.
The ultimate goal of threat hunting is not to find more security incidents — it’s to drive continuous improvement across your entire security program.
In this article, we will delve into the intricacies of threat hunting, including its purpose and benefits, the frameworks available to help guide your efforts, and, importantly, metrics for measuring
(Already using Splunk? Check out our Complete Guide to Threat Hunting with Splunk.)
What is threat hunting?
In general, we can think of threat hunting as the name for any manual or machine-assisted process for finding security incidents that your automated detection systems missed. The machine-assisted part is critical, due to the volume and velocity of security data coming into today’s organizations, we require good automated detection to keep up with it. (That’s because, with this much data, human review isn’t just expensive, it’s impossible to do.)
With a focus on finding threats that evade traditional security measures, the threat hunting practice uses a combination of automated tools and manual techniques to identify suspicious patterns and behaviors. This then leads to improving detection capabilities, yes, and overall improvements to your security posture.
Threat hunting drives security improvement
When a hunter figures out a new way to detect malicious behavior, the goal is to also figure out how to automate that detection. That way, the next time malicious activity will be alerted and responded to quickly.
Similarly, threat hunters are always poking around in parts of your network data that other people either don't look at often or look at in different ways. Therefore, hunters are more likely to notice things like:
- Visibility gaps
- Data collection issues
- Misconfigurations
- Other issues that impact security posture
By identifying and reporting these, the hunt team is a constant source of what we often call "opportunities to improve".
So, don’t think of hunting as a way to find more security incidents using expensive humans. Instead, think about threat hunting as a way to improve your entire security program over time.
(Related reading: threat hunting vs. threat detection: what’s the difference?)
Threat hunting trends
Interest in threat hunting has been steadily climbing in the last few years. This is no surprise, of course, as security breaches, attacks, and privacy regulations are regular features in national news. More and more people are aware of everyday threats.
Luckily, we can track some trends, directly from threat hunters and security leaders. SANS has been reporting on threat hunting for nearly a decade!
The SANS 2024 Threat Hunting Survey, which Splunk proudly sponsored, engaged security and business professionals from an array of companies and organizations on six continents. Small businesses (we see you!) all the way to governments and large corporations participated.
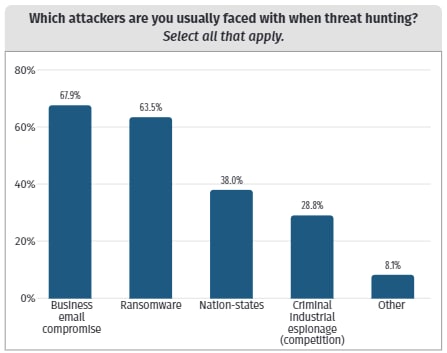
Here are some important stories that surfaced from these surveys:
- Formal threat hunting programs are truly on the rise. In 2023, 35% of participating organizations had threat hunting programs. This year, threat hunting has reached a majority: 51% of organizations reported they have established true hunting programs.
- Measuring the effectiveness of hunting efforts is now almost commonplace. In 2024, nearly two-thirds (65%) of organizations reported measuring their efforts, compared with only 35% last year. (More on hunting metrics later in this article.)
- Organizations are outsourcing this critical practice, with some concern from professionals. This year, 37% leverage external sources for threat hunting. This has some pros and more cons. Certainly, the ability to establish and scale a program is easier: just hire an external team. Still, this third-party approach introduces potential risks and can disrupt the organization’s existing security systems. Not to mention challenges that may arise around data control and data governance.
With more people talking about this important practice, our threat hunting team here at Splunk is thrilled to share what we’ve learned — more on that below. But the statistics don’t lie: threat hunting offers many benefits to your organization.
Types of threat hunting
First of all, threat hunting isn't a one-size-fits-all approach. Security teams should plan their threat hunting process based on available resources, threat landscape, and specific areas of concern. Then there comes the type of hunt you may embark on.
You may hear people talk about different types of hunting: structured or unstructured hunting, situational hunting, intel-based hunting, etc. In my experience, however, I don't think those are the best ways to describe it.
Instead, I recommend hunters think of hunting as we’ve built the PEAK Threat Hunting Framework. An acronym for "Prepare, Execute, and Act with Knowledge," the PEAK framework is vendor- and tool-agnostic and it incorporates three distinct types of hunts:
- Hypothesis-driven hunts. In this classic approach, hunters form a hunch or hypothesis about potential threats and their activities that may be present on the organization’s network. Hunters then use data and analysis to confirm or deny their suspicions.
- Baseline hunts. In this type of hunt, hunters establish a baseline of “normal” behavior and then search for deviations that could signal malicious activity. This hunt type is sometimes also known as exploratory data analysis (EDA).
- Model-Assisted Threat Hunts (M-ATH). You could describe M-ATH hunts as "Sherlock Holmes meets artificial intelligence" and you wouldn’t be wrong! Here, hunters use machine learning (ML) techniques to create models of known good or known malicious behavior, then they look for activity that deviates from or aligns with these models. This is almost a hybrid of the hypothesis-driven and baseline types, but with substantial automation from the ML.
(Learn more about each of these hunt types: hypothesis-driven hunting, baseline hunting, and M-ATH hunting.)
Three stages of threat hunting
According to PEAK, each hunt should follow a three-stage process: Prepare, Execute, and Act:
- In the Prepare phase, hunters select topics, conduct research, and generally plan out their hunt.
- The Execute phase involves diving deep into data and analysis.
- The Act phase focuses on documentation, automation, and communication.
Crucially, each phase integrates Knowledge. This knowledge can come in many forms: organizational or business expertise, threat intelligence and OSINT, prior experience of the hunters, and (of course) any findings from the current hunt.
Must I hunt? Reasons for threat hunting
For most organizations, threat hunting is highly recommended. That’s for a few reasons.
Intrusion prevention doesn’t work every time. The stealthy techniques attackers use can often escape detection. More importantly, attackers are innovating at an alarming rate, resulting in a constant stream of new and updated attack techniques.
Hunting is an effective way of helping your defenses keep up. Here’s why most organizations do threat hunting — and why you should too:
Improved security posture
Strengthening your security posture, threat hunting can help organizations identify and mitigate weaknesses in their detection rules, platforms, and data collection. By actively searching for threats, security teams gain valuable insights that can be used to improve security controls and prevent future attacks. Threat hunting also helps in detecting sophisticated attacks that traditional security tools might miss.
Harnesses human intuition and creativity
Unlike automated detection products, which can only alert on what they’ve been programmed to find, threat hunting is a human-driven process. Humans are very good at identifying patterns, even in the face of incomplete or ambiguous data.
(Related reading: detection engineering.)
Reduced dwell and response time
Attackers can linger within your network undetected for extended periods, maximizing the damage they can inflict. In fact, threats can break into any network and avoid detection for up to 280 days on average!
Threat hunting helps identify threats sooner and minimizes the time a threat remains undetected within the network. It also enhances the ability to respond to and mitigate security incidents quickly. All this minimizes potential losses.
Puts security on the offense
Unlike traditional incident detection programs, which are purely reactive, threat hunting is a proactive approach to identifying threat actors on your network that you might not already be detecting well. Threat hunting helps you address threats before they cause significant damage.
Compliance and reporting
Threat hunting allows you to provide concrete evidence of proactive threat detection and mitigation efforts. Organizations can document their activities and findings, creating detailed reports that highlight their commitment to security.
This transparency ensures compliance and also builds trust — with stakeholders, customers, partners, and regulators — demonstrating your organization's dedication to maintaining a secure and compliant environment.
(Related reading: continuous compliance.)
Continuous improvement
When organizations engage in threat hunting, they uncover valuable data. By systematically analyzing this information, security teams can identify areas that need strengthening. Additionally, threat hunting helps in continuously improving your detection capabilities.
Staying up-to-date
Cybercriminals are constantly innovating their tactics. Threat hunting empowers your security team to stay ahead of the curve by employing the latest threat intelligence and adapting their hunting strategies to proactively address emerging threats.
Threat hunting frameworks
OK so you’re ready to hunt…so, where do you begin? A threat hunting framework is a system of adaptable, repeatable processes designed to make your hunting expeditions both more reliable and more efficient.
There are a number of frameworks out there, the most notable are the following.
The Sqrrl Threat Hunting Reference Model (2015)
Published in three parts (part 1, part 2, part 3), Sqrrl’s framework was not only the first, but remains one of the most influential threat hunting frameworks. It defines the hypothesis-driven hunting process as a loop with four stages:
- Create hypothesis
- Investigate via tools & techniques
- Uncover new patterns & TTPs
- Inform & enrich automated analytics
TaHiTI: Targeted Hunting Integrating Threat Intelligence (2018)
The TaHiTI framework, created by a consortium of financial institutions known as the Dutch Payments Association, is another popular threat hunting framework. We can summarize TaHiTI as:
- Building on pieces of the Sqrrl framework, including the Hunting Maturity Model.
- Adding a new type of hunt, known as the unstructured or data-driven hunt.
- Providing more detailed guidance on the hunting process and on potential metrics for hunt program success.
PEAK: Prepare, Execute, & Act with Knowledge (2023)
The PEAK Threat Hunting Framework incorporates experience gained and lessons learned during the last several years of threat hunting. This framework is both vendor- and tool-agnostic, and it was co-created with an original creator of the Sqrrl framework.
The PEAK Framework adds a third type of hunt, Machine-Assisted Threat Hunting (M-ATH), shown below. Importantly, the framework provides even more detailed implementation guidance for each hunt type.

The PEAK Framework incorporates three distinct hunt types. This diagram illustrates the Model-Assisted Threat Hunt (M-ATH).
Threat hunting metrics
A very important part of any threat hunting program is the ability to measure it.
Today, 1.5 years since its original publication, teams and organizations who have adopted the PEAK framework repeatedly tell me and my team of hunters that the framework's focus on metrics is much-needed and much-appreciated. After all, CISOs and security leaders love metrics — because these measurements tell us we really need to know.
PEAK offers a full set of hunting metrics to use as a baseline for measuring the impact that your threat hunting program has on your overall security program. Our philosophy is that hunters must measure what you’ve done and measure the effects of what you’ve done. Some areas to measure include:
- Number of detections created or updated
- Number of incidents opened during/as a result of a hunt
- Numbers of gaps identified and gaps closed
- Number of vulnerabilities & misconfigurations identified and the number closed
Maturing your hunting program
Another important aspect of the PEAK Framework is building hunt maturity. The framework includes a hunting maturity model, first developed back in 2015, to help leaders assess the current state of their hunting program and capabilities — and determine where they would ultimately like to be. Think of it as the roadmap for improving threat hunting over time.
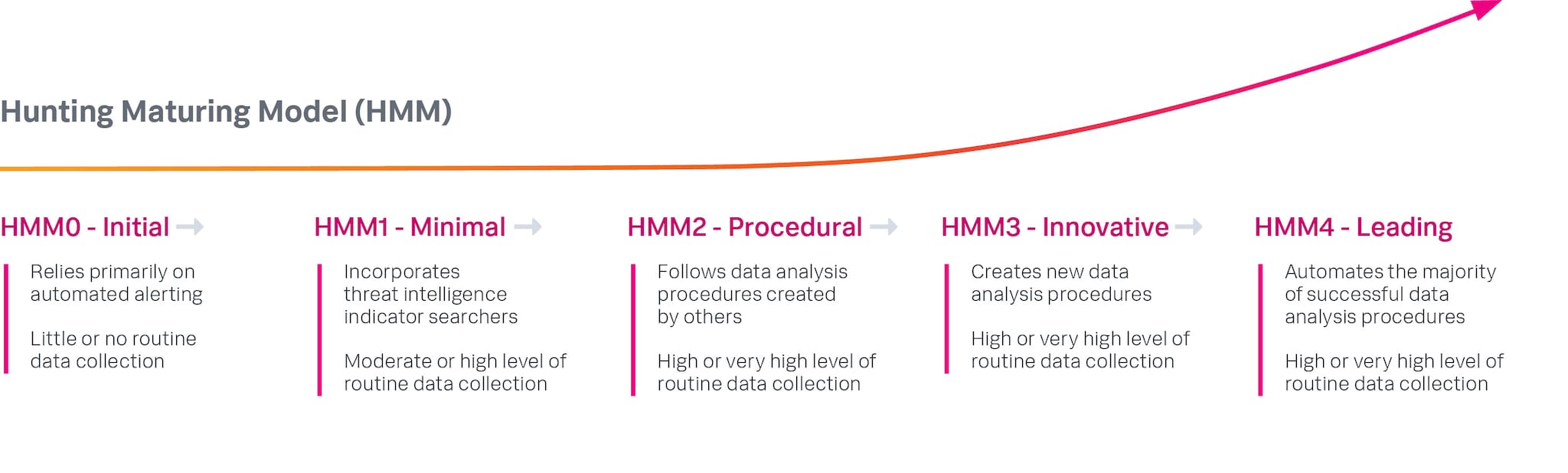
The Hunting Maturity Model, by David J. Bianco (2015)
Fear not the threat, start hunting
Threat hunting is a proactive approach to cybersecurity that leverages human intuition and creativity to identify and counter security incidents that may otherwise go undetected. By incorporating threat hunting into your organization's security practices, you can improve your overall security posture.
- Harness the power of human-driven pattern recognition.
- Ultimately bolster your automated detection capabilities.
While threat hunting can be resource-intensive, the benefits of staying ahead of potential attacks make it a highly recommended practice for most organizations. To get started, consider adopting a threat hunting framework, which can provide a structured and efficient approach to your threat hunting endeavors.
Video: I Screwed Up Threat Hunting a Decade Ago and Now We're Fixing it With PEAK
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.


