Extend the power of Splunk Cloud or Splunk Enterprise for enhanced, real-time security visibility and improved threat detection.
solution
End-to-end visibility across your environment for accurate threat detection
Real-time visibility over security posture
Monitor tens of terabytes of data per day from any source to gain end-to-end visibility
Search and analyze
Seamlessly search your data across distributed environments for faster investigation and remediation.
Prioritize alerts
Correlate data and alerts to gain insight into your security posture and understand incident context
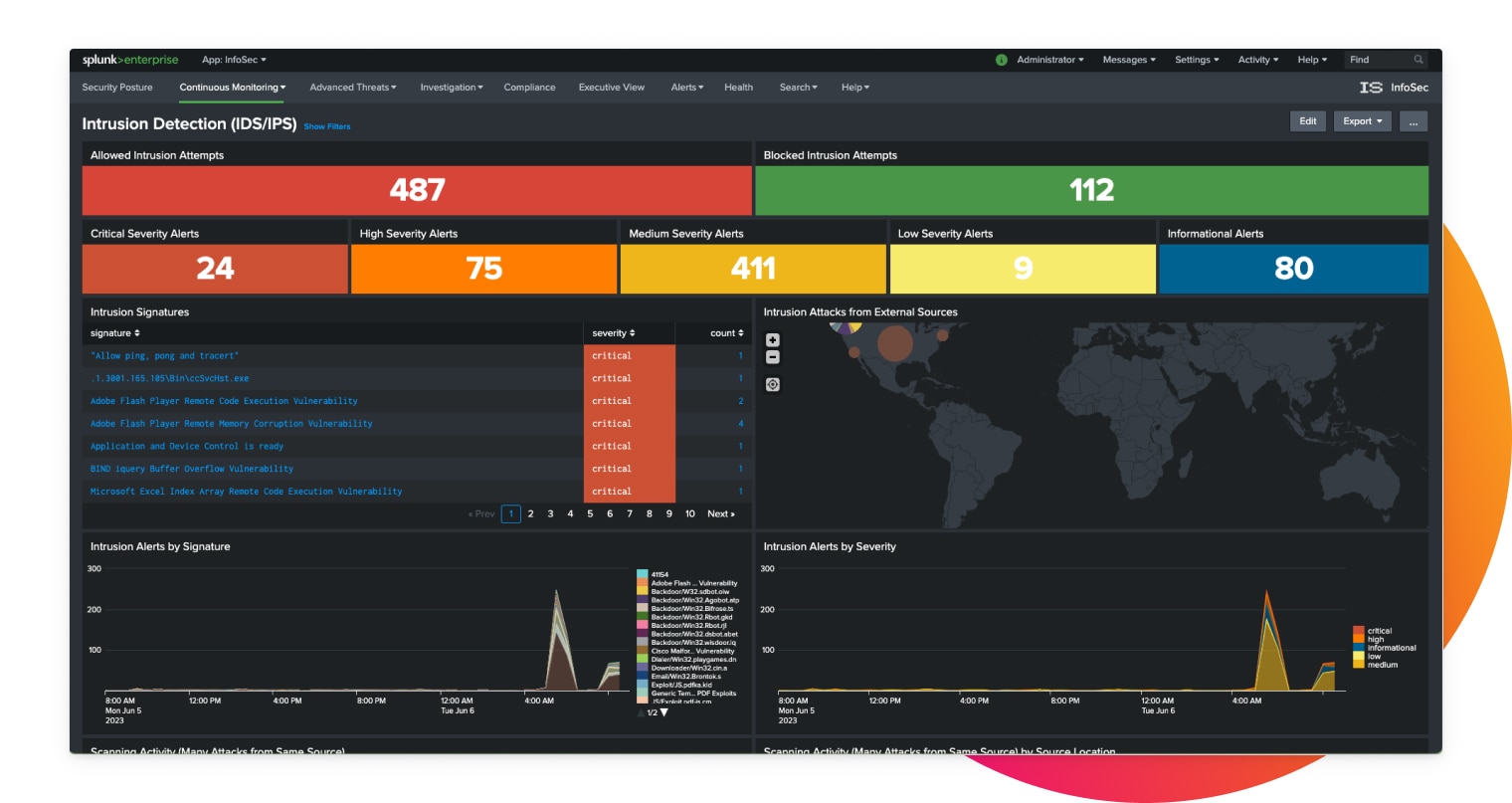
Extensive pre-built detections
Out-of-the-box detections built by industry-recognized experts align to industry frameworks such as MITRE ATT&CK, NIST, CIS 20 and Kill Chain — and help you stay ahead of threats.
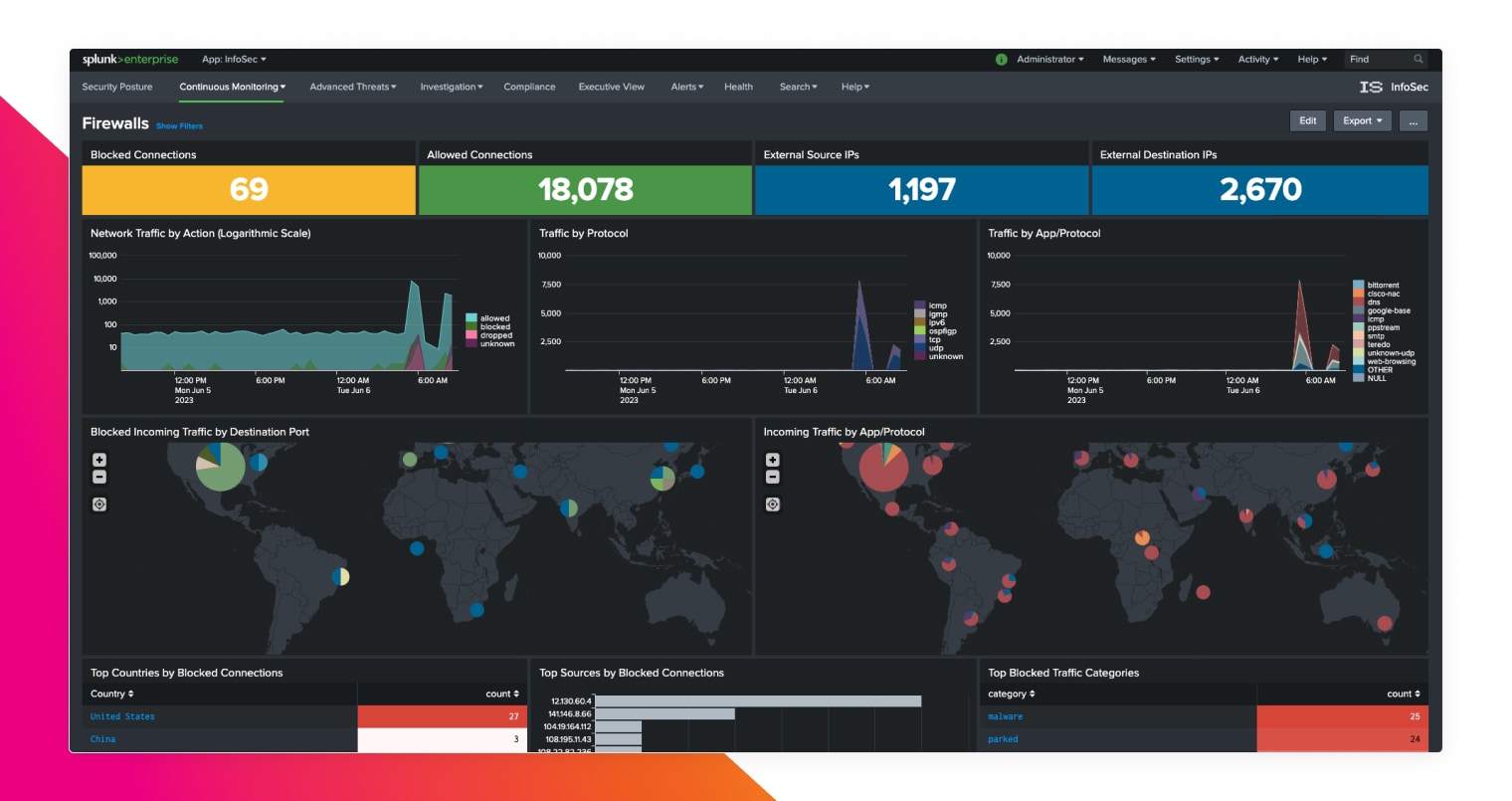
Ingest any data from any source
Monitor tens of terabytes of data per day from any source (structured or unstructured) to gain end-to-end visibility of your environment (on-premises, hybrid or multi-cloud) and make data-centric decisions to protect and reduce risk on your business.
Splunk Cloud Platform handles all of our logs, whether from our antivirus software or endpoint detection and response. Splunk raises the alert, opens a ticket and contacts the on-call SOC analyst. It’s the cornerstone of our security operations.
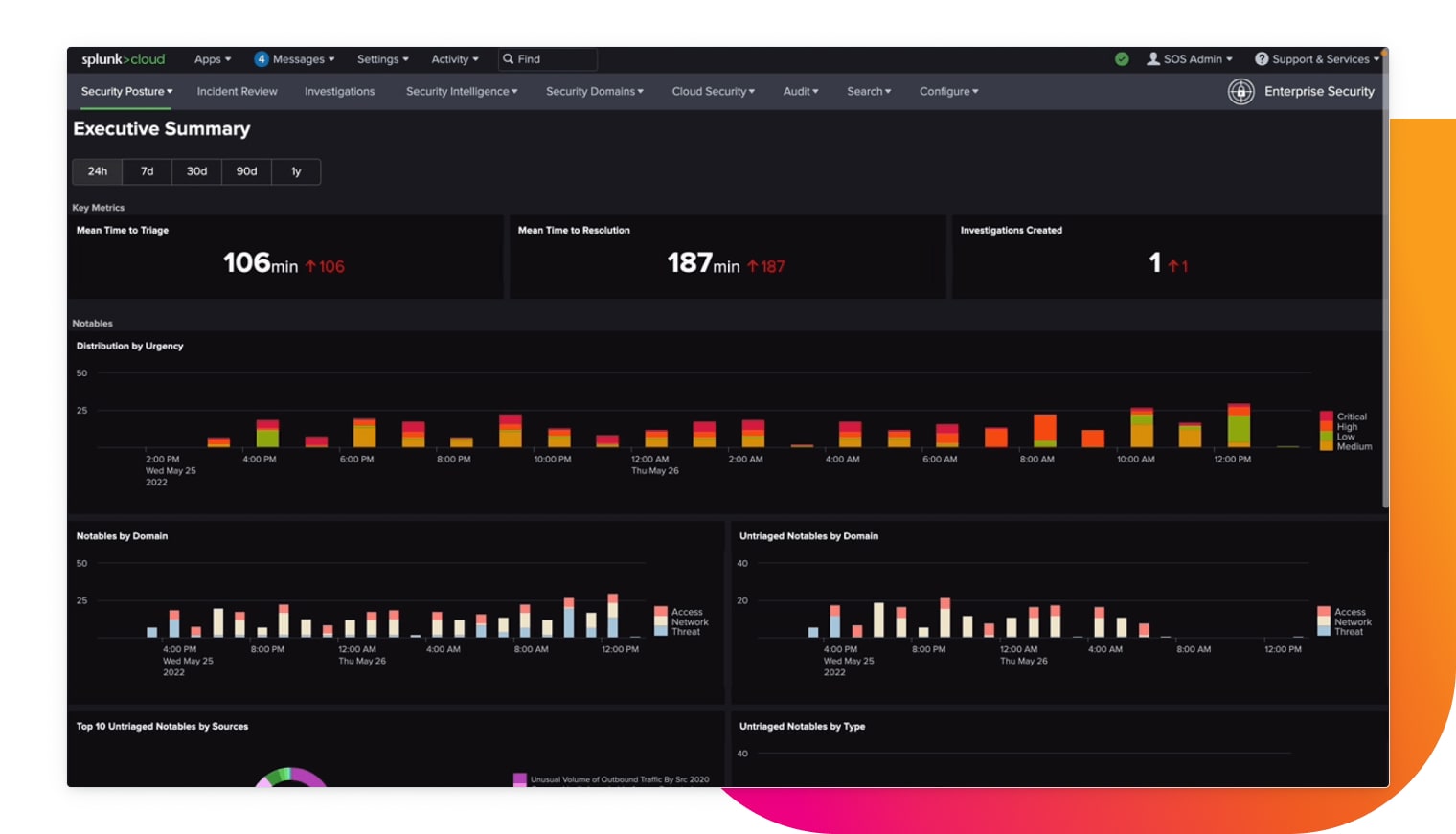
Pre-built dashboards with intuitive visualizations
Easy-to-use dashboards help security teams see and understand their data, team performance and metrics to simplify security monitoring and incident management.
Splunk enables us to get the most out of data to evolve our security initiatives and remain resilient against cybersecurity challenges.
