Get cloud-powered insights for petabyte-scale data analytics across the hybrid cloud.
solution
A proactive and analytics-driven approach to compliance.
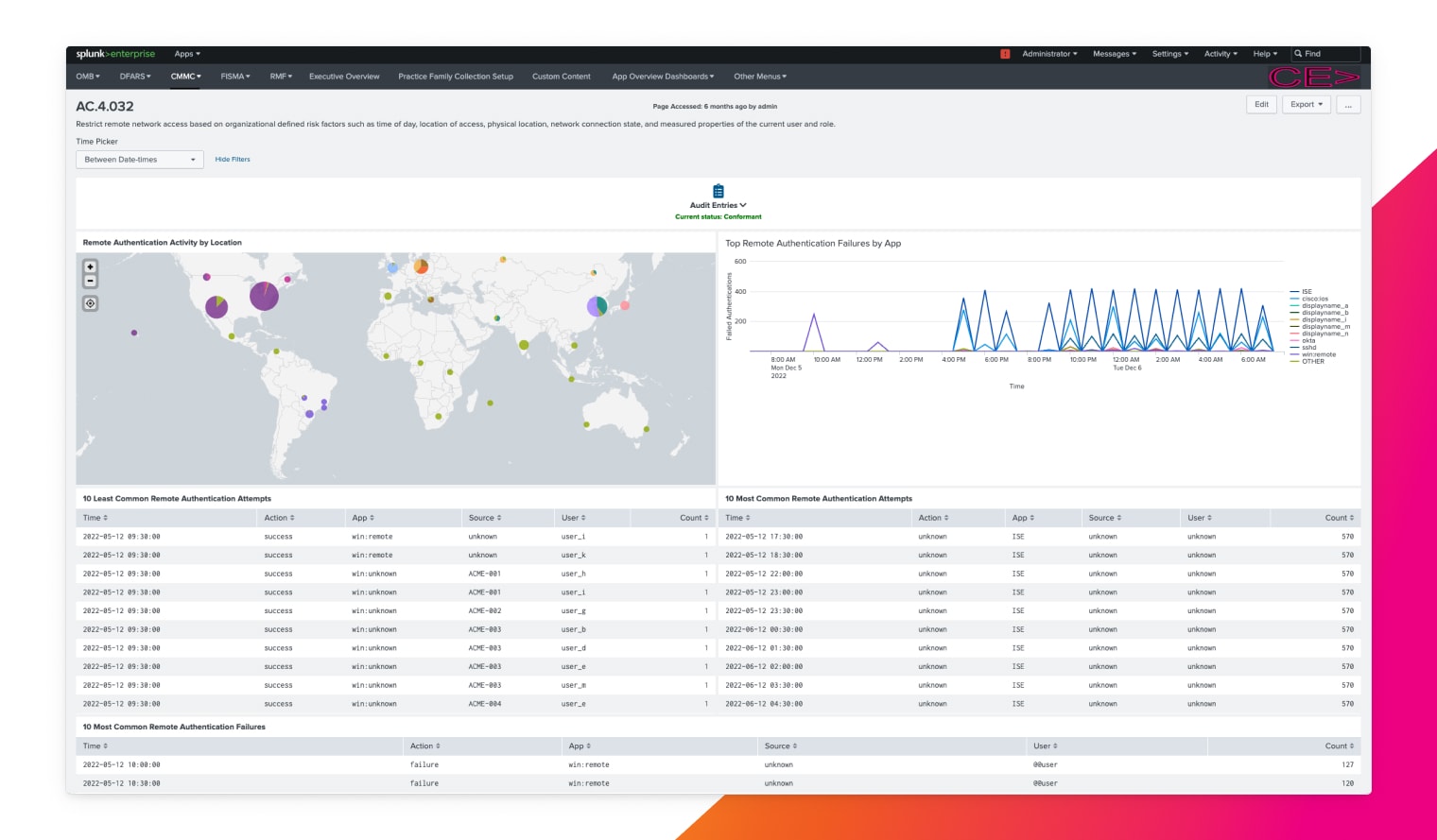
Automated data collection
Collect, search, monitor and analyze data using a centralized solution to meet compliance requirement.
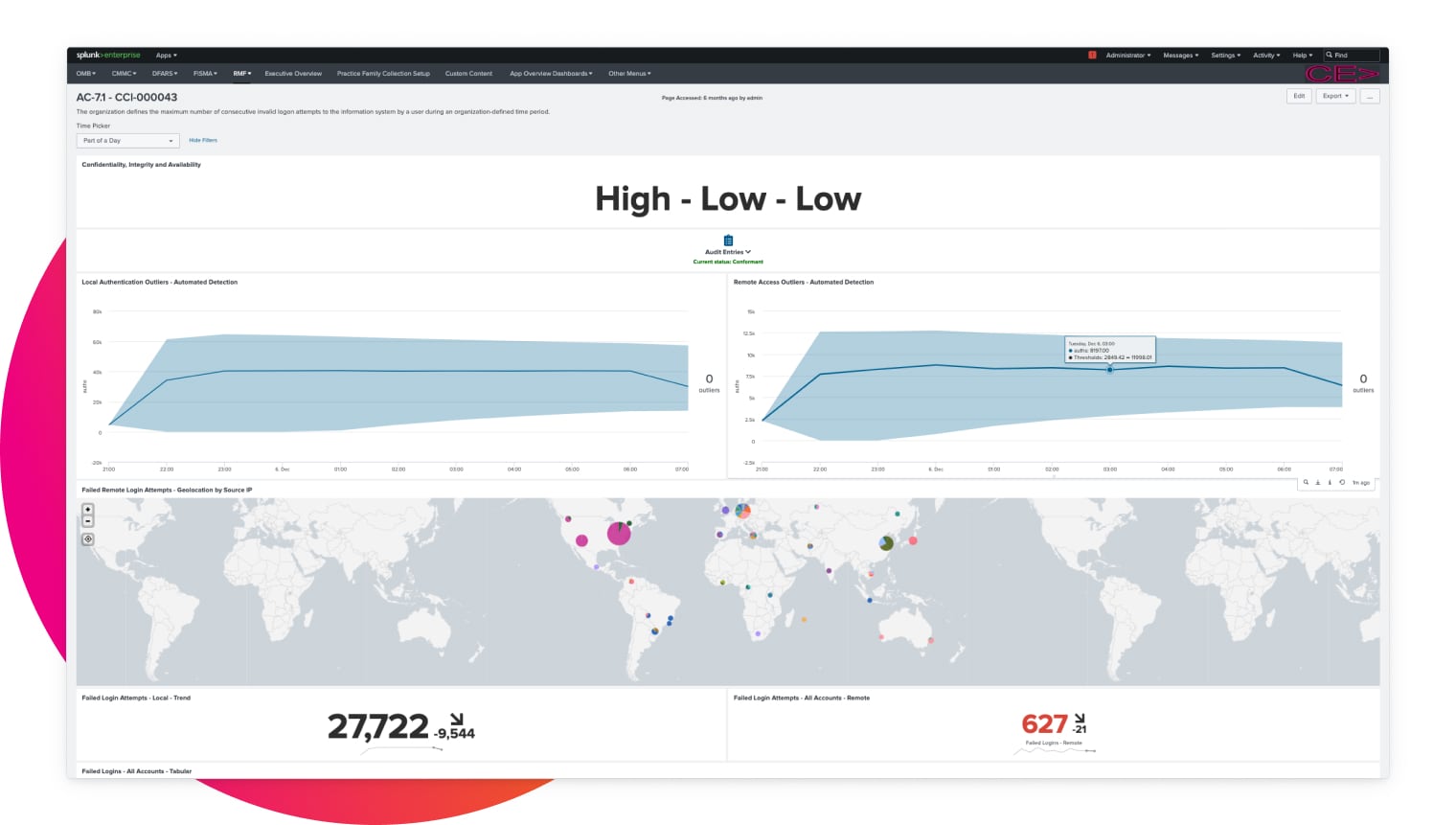
Continuous risk assessment
Get real-time insights into your environment's risk posture and compliance.
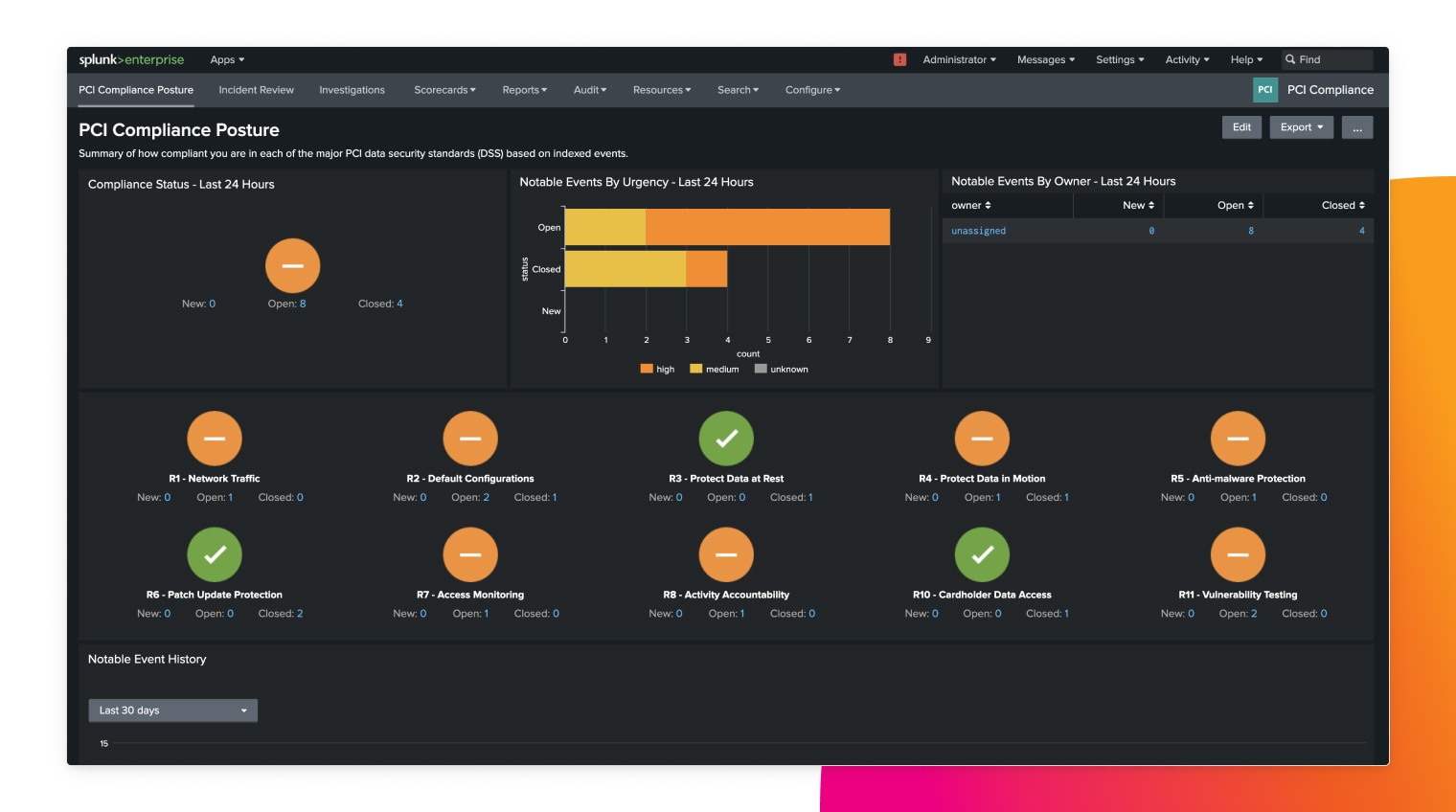
Easy auditing and reporting
Identify your organizational gaps against regulations with automated compliance tasks and customized reports to ease the burden of audits.
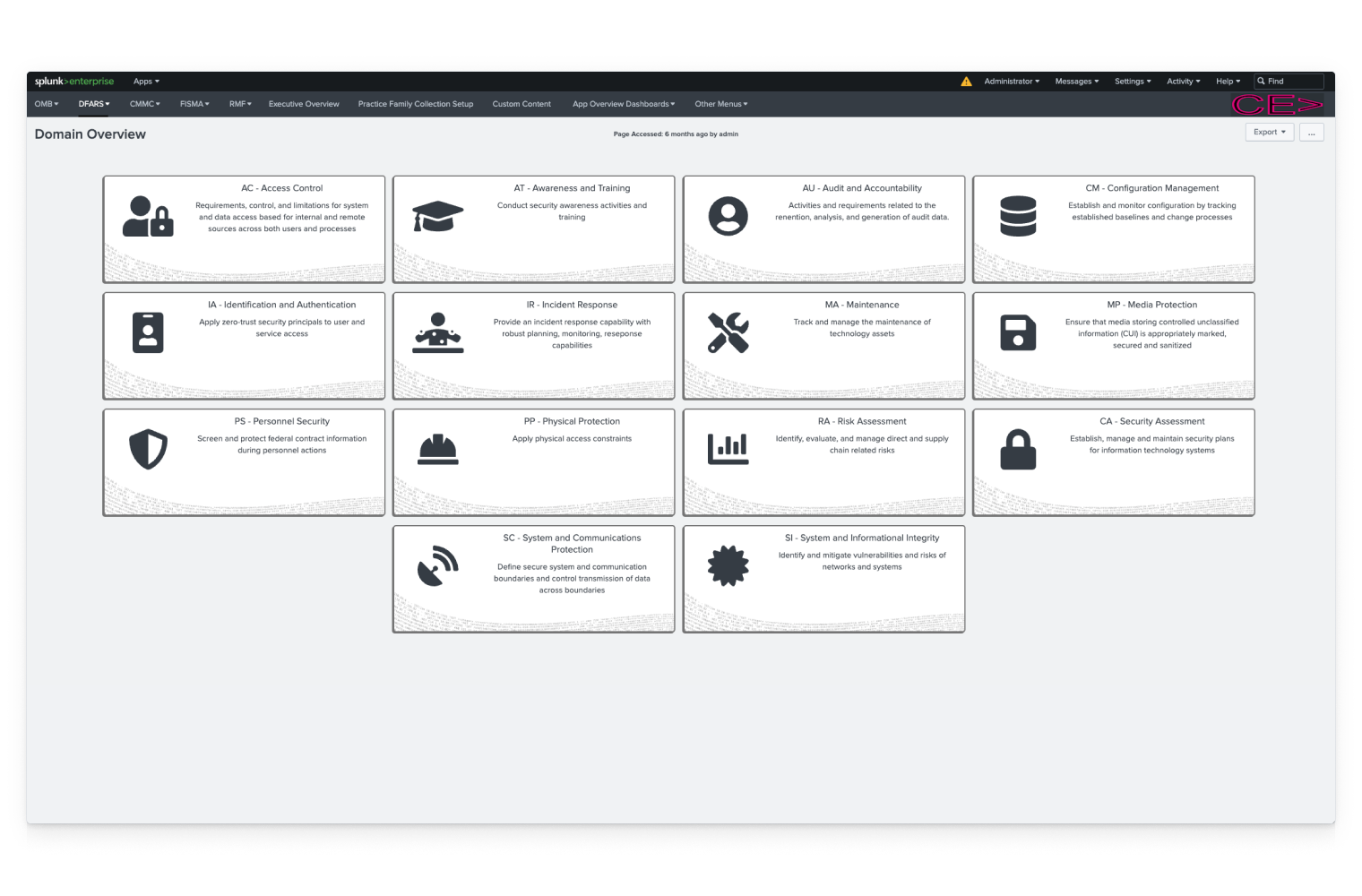
A single platform to operationalize compliance
Quickly gain real-time posture and insights across all IT resources and security controls to clear compliance and pass audits with minimal effort, regardless of mandate or regulatory framework.