Get data-driven insights for end-to-end visibility into your security posture to protect your business and mitigate risk — at scale.
solution
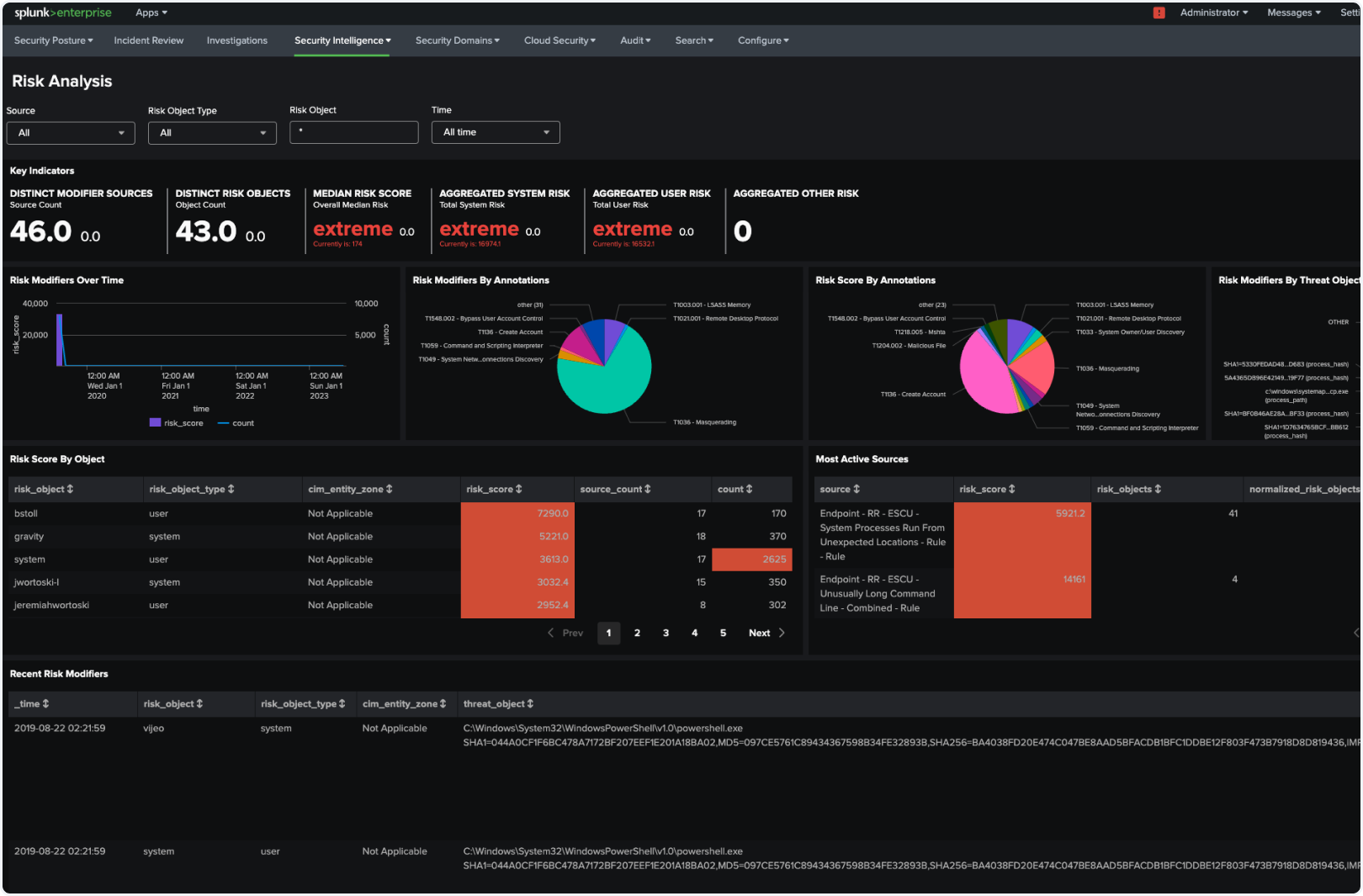
Detect faster, analyze better
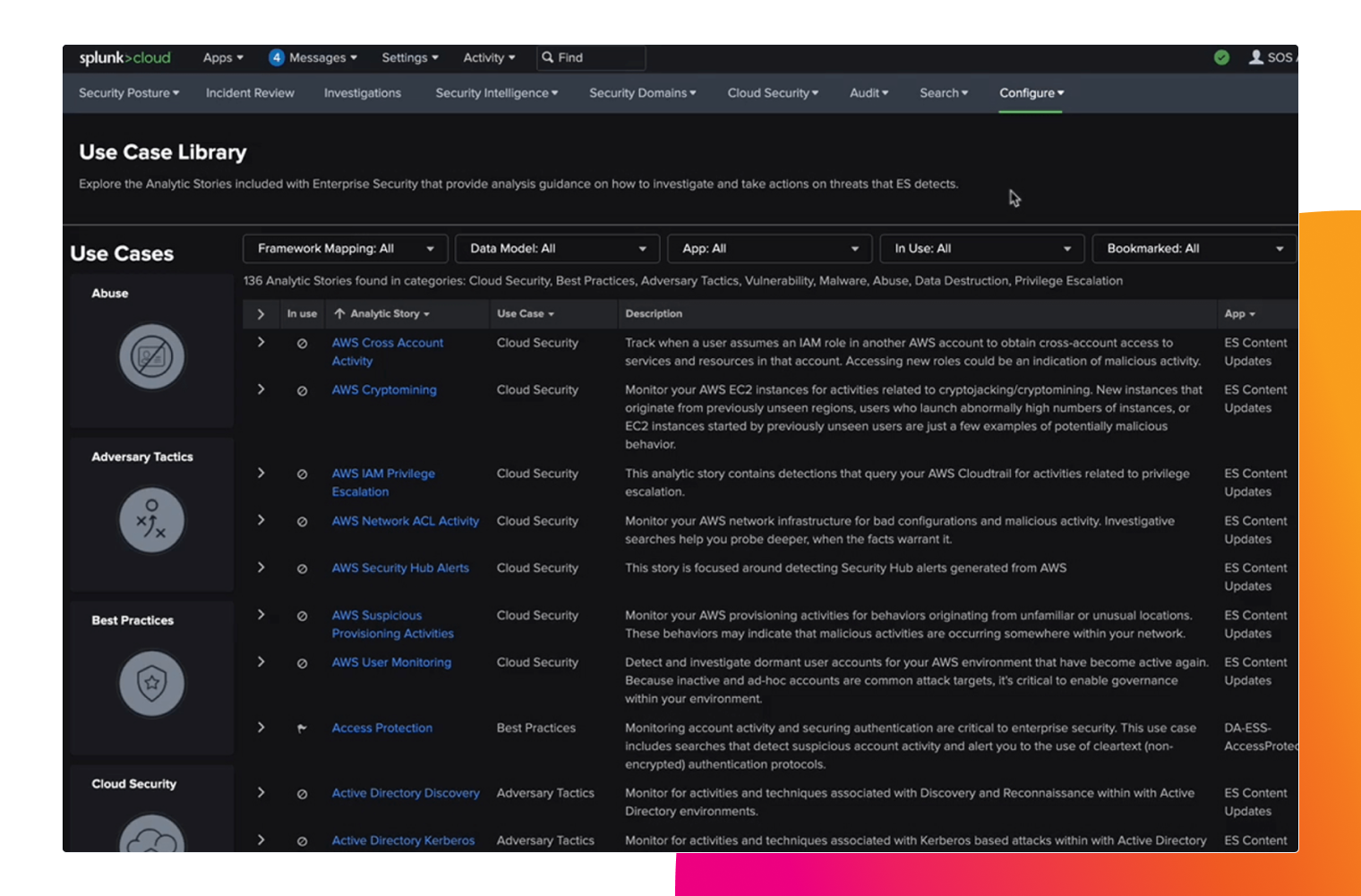
Proactively uncover new threats
Become aware of hidden threats and, using flexible searches, proactively identify adversaries that may have found ways to establish a foothold in your organization's network.
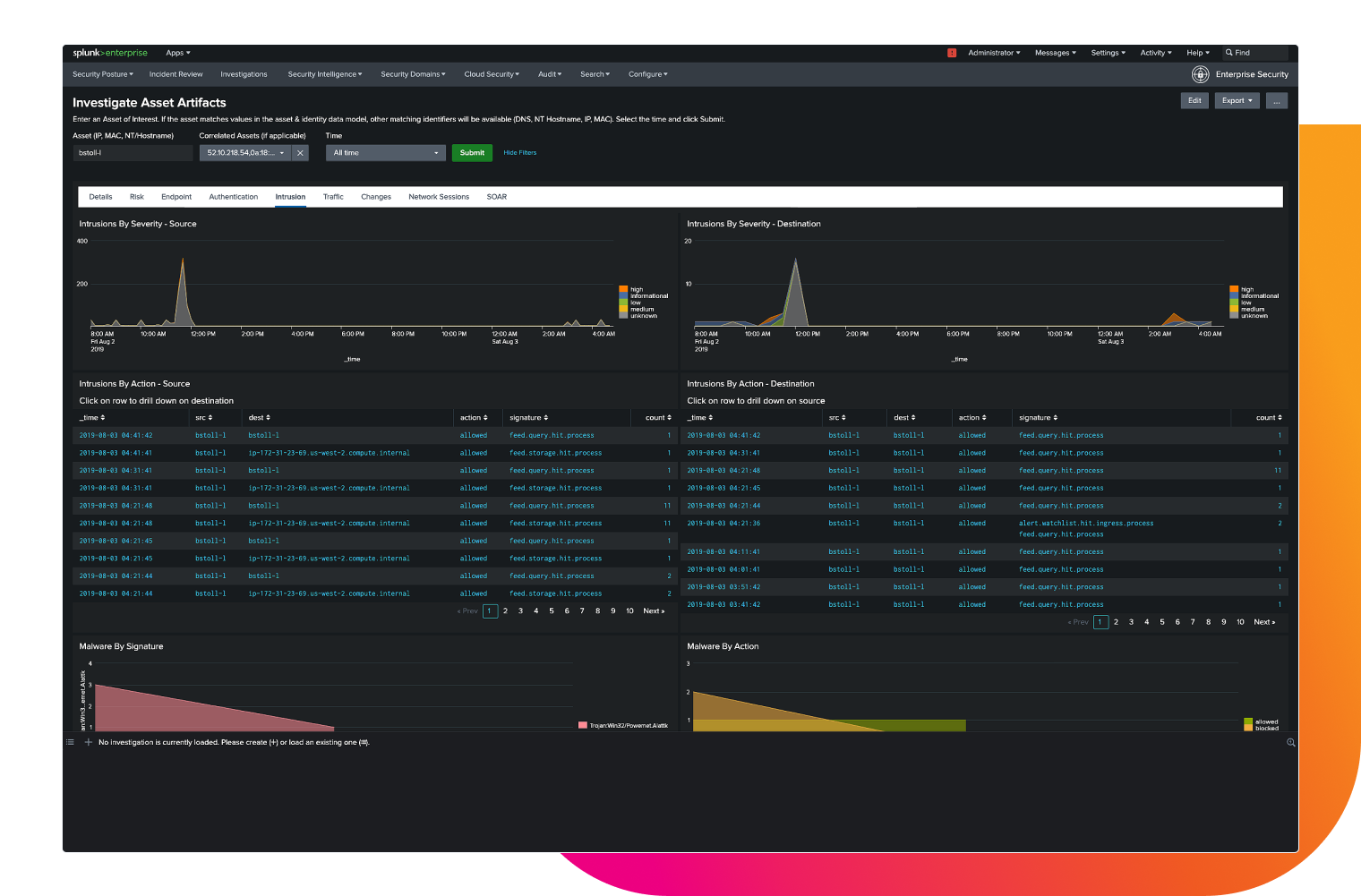
Accelerate threat hunting
Use deep investigative capabilities and powerful behavior baselines on any entity, anomaly or threat.
Improved security posture
Identify and mitigate weaknesses in detection rules, tools and data collection.
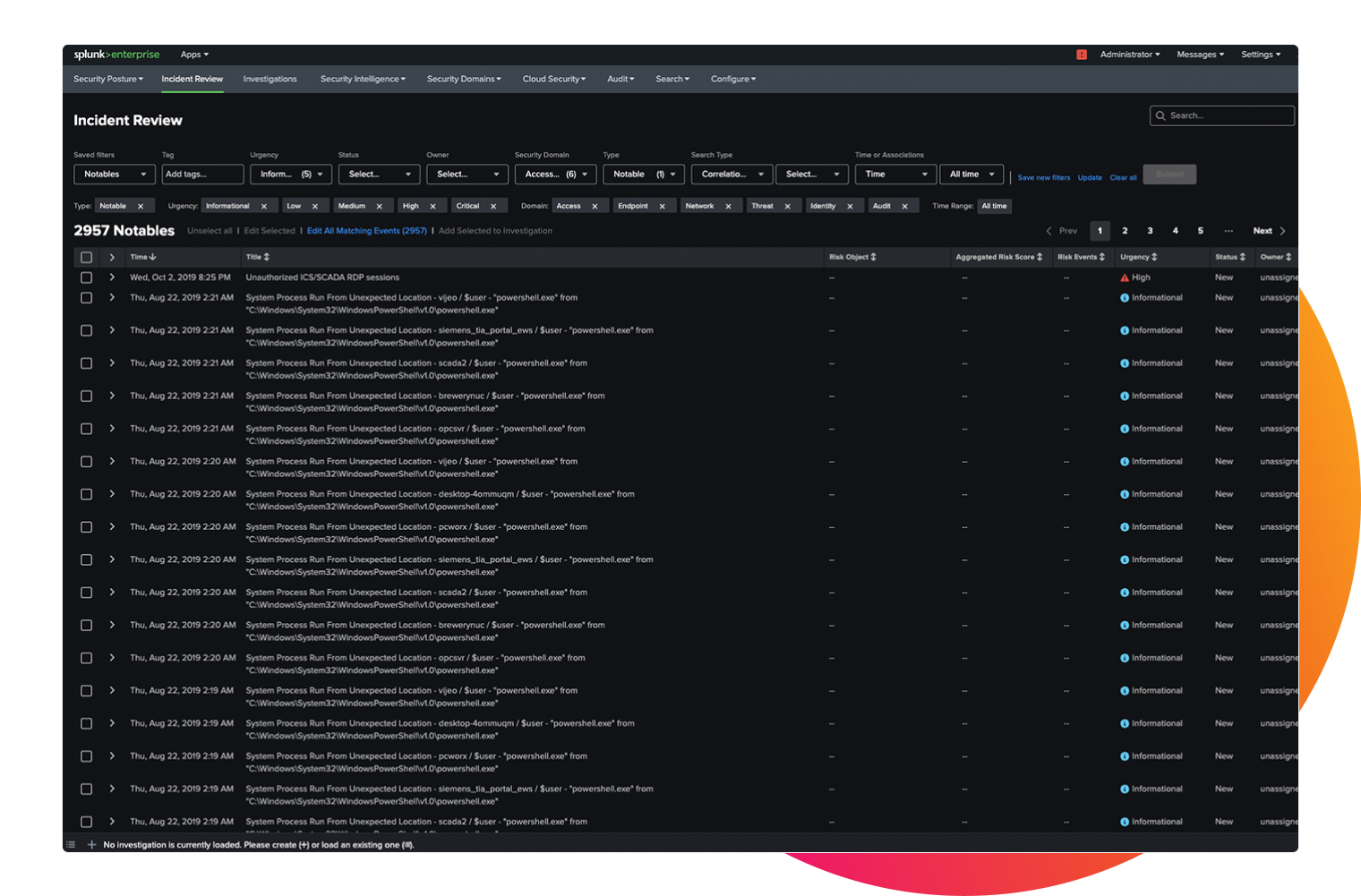
Early stage threat detection
Cyber threat hunting can identify threats earlier than traditional detection-based security methods.
Splunk delivers strong data query functionality paired with IT observability data to deliver robust results and provide options for conducting advanced security operation functions, such as threat hunting in large data environments.