Automate repetitive tasks, take care of security incidents in seconds and increase analyst productivity.
solution
Fast and flexible incident management
Investigate quickly and efficiently
Perform rapid searches across data, focus on the most relevant issues, and quickly close investigations.
Analyze and visualize data
Gain deeper insight into security posture using pre-built, fully customizable dashboards and visualizations.
Automate decisions and actions
Automate investigations for quick insights and responses in seconds.
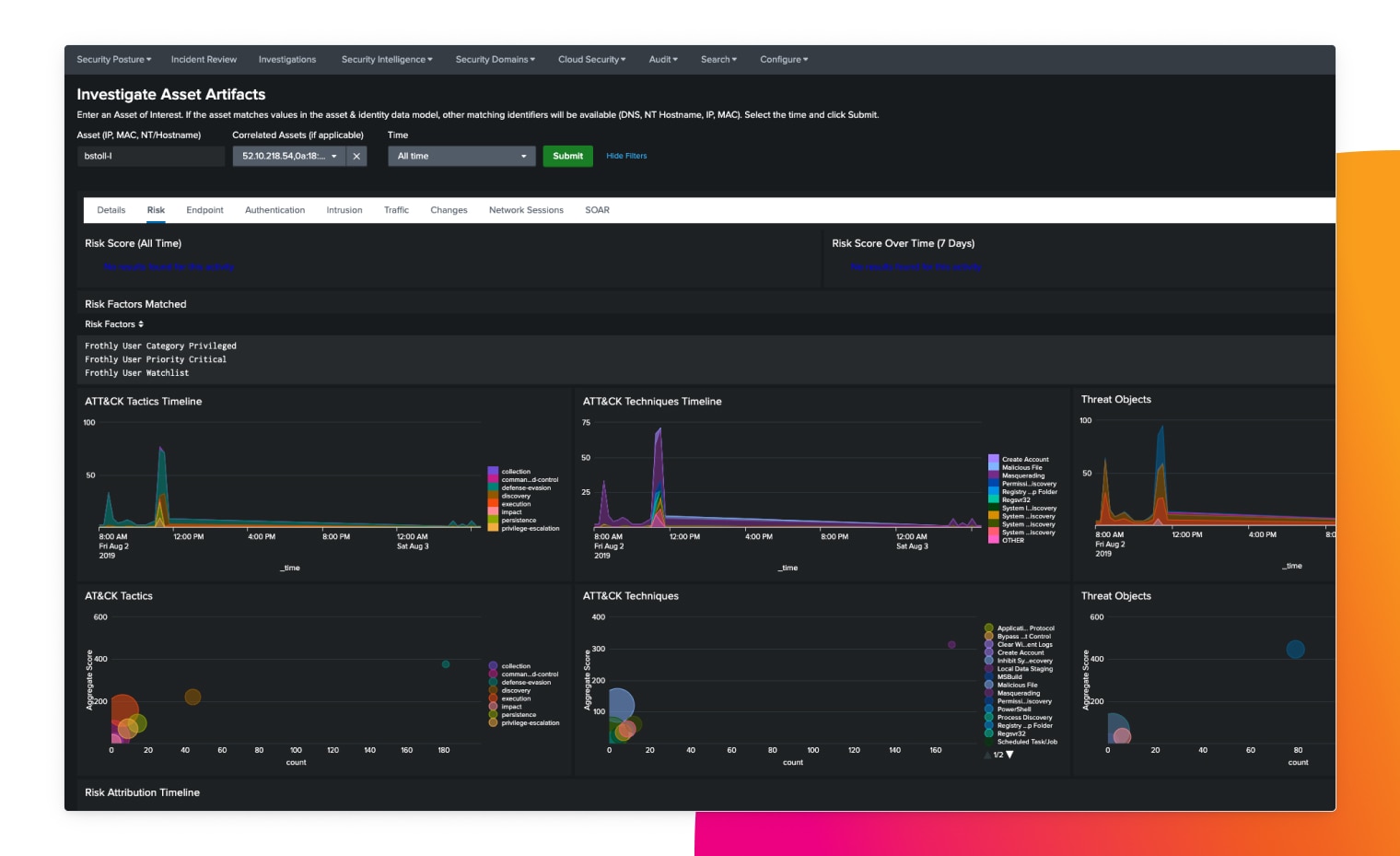
Understand the full context in seconds
Quickly determine root cause and easily search for evidence of an incident through fast and flexible search and reporting.
Check Point experienced 5x faster security investigations with Splunk.
We now know what to investigate and whether we’ve solved the problem. And not just because someone has a gut feeling about it. The data shows us for certain.
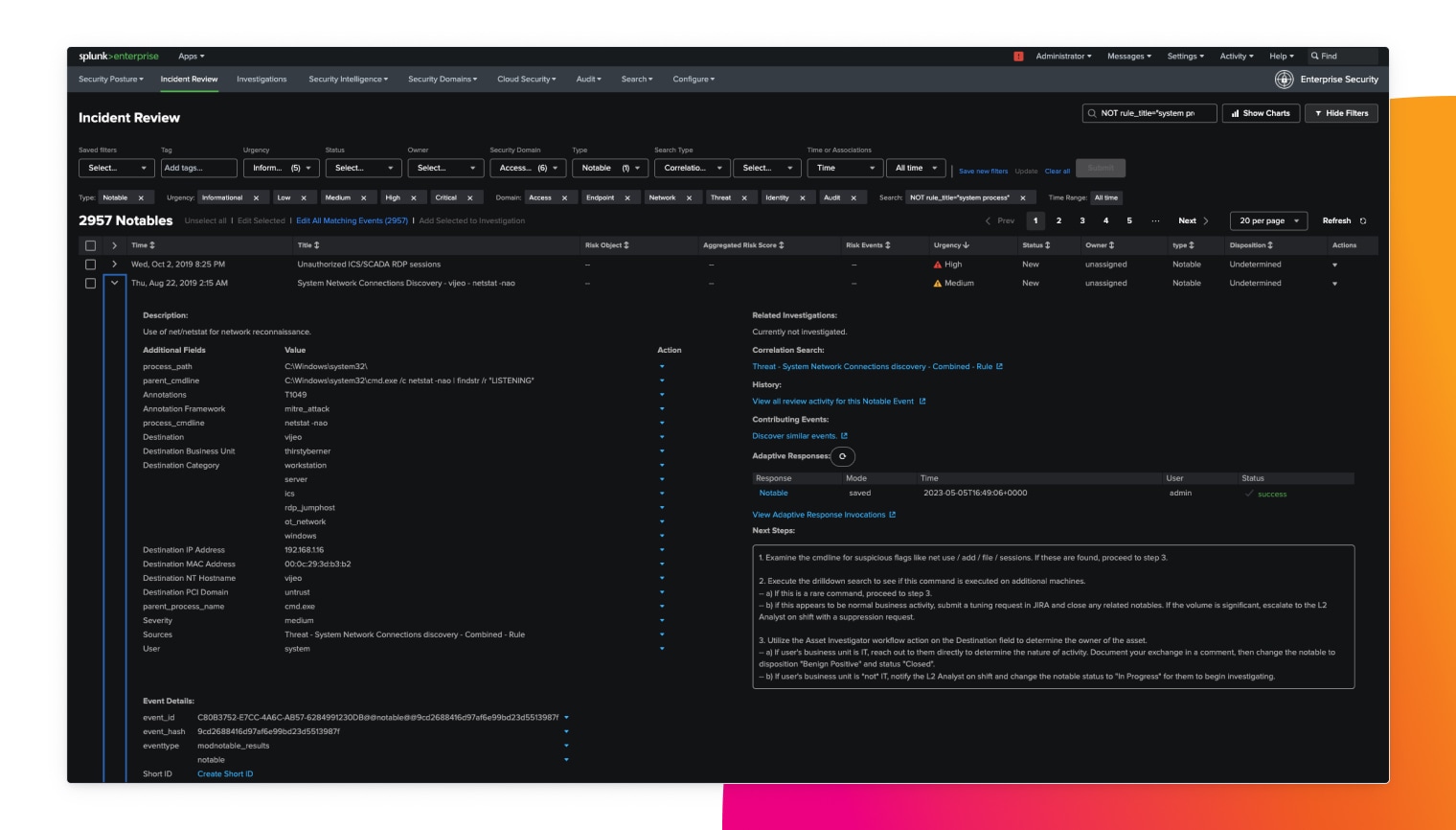
Rapid and accurate threat detection
Minimize false positives by automatically analyzing, enriching and validating alerts. Also, make investigations faster and more efficient by prioritizing them based on organizational risk.
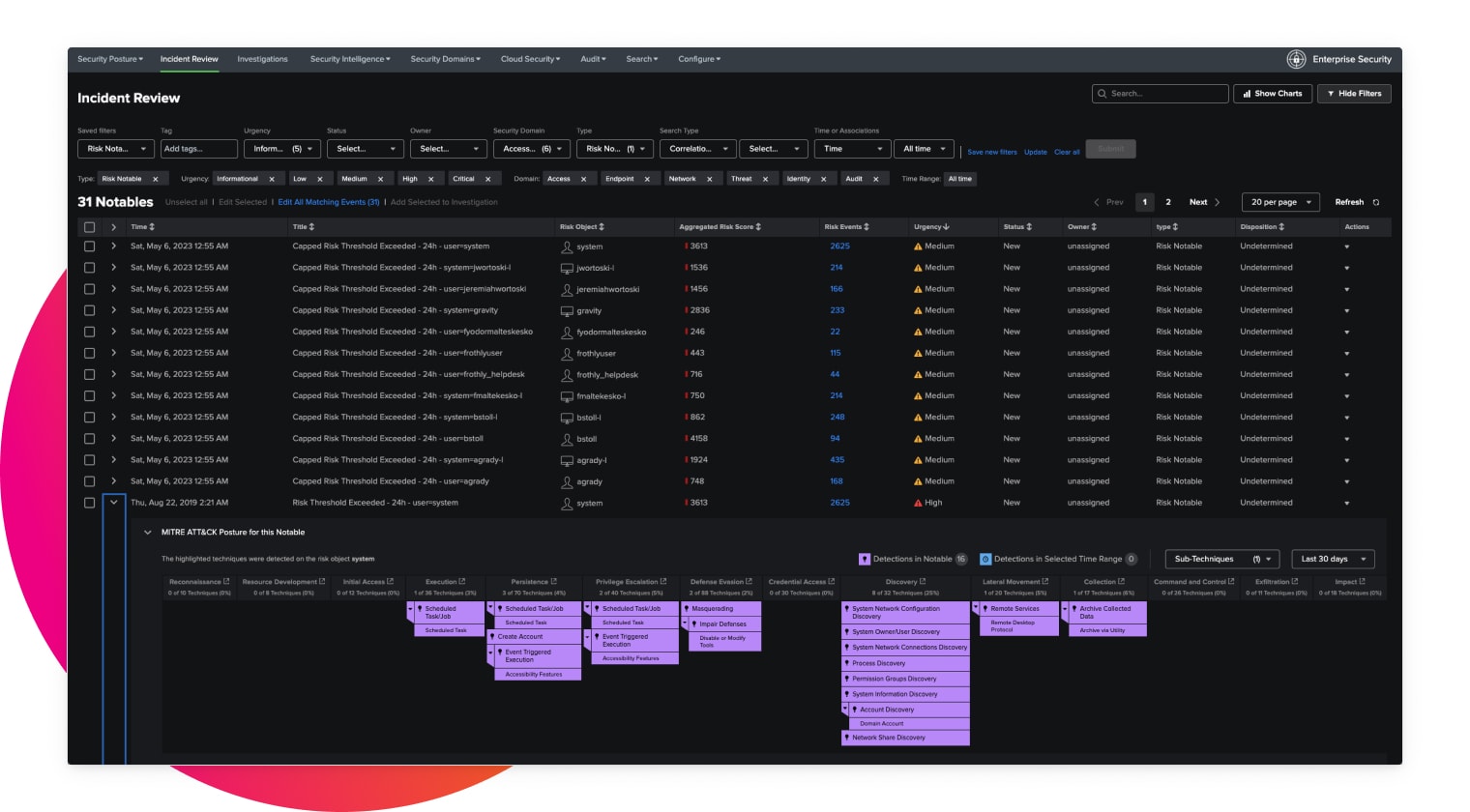
Stay ahead of threats
Detect advanced threats with out-of-the-box detections built by industry-recognized experts that are aligned to industry frameworks such as MITRE ATT&CK, NIST, CIS 20 and the Cyber Kill Chain.
We get so much value from Splunk. It maximizes the insights we gain from analyzing detection use cases, rather than wasting time creating rules or struggling with a tool that’s too complicated.