Data Encryption Methods & Types: A Beginner's Guide

Key takeaways
- Data encryption transforms readable data into an unreadable format to protect it from unauthorized access, ensuring that only authorized parties can decrypt and access the original information.
- There are various encryption methods — including symmetric (e.g., AES, 3DES), asymmetric (e.g., RSA, ECC), and advanced techniques like homomorphic and format-preserving encryption — each suited to different security, performance, and compliance needs.
- Choosing and implementing robust encryption strategies is essential for organizations to safeguard sensitive data, comply with regulations, and protect against cyber threats across data at rest and in transit.
Data encryption is one of the many ways organizations can protect their data. Encryption turns plaintext (readable data) into ciphertext (randomized data), which requires the use of a unique cryptographic key for interpretation.
In simple terms, we can say: encryption is a security measure that scrambles data so that it can be read only by authorized personnel.
The first and simplest encryption technique we know of is the Caesar cipher, from 58 BCE. Today, many types of encryptions are available. It’s important to choose the right encryption algorithms and techniques for your business’s security requirements. In this article, we'll:
- Examine symmetric and asymmetric encryption methods.
- Detail common encryption algorithms and when to use them.
- Cover tips and best practices for data encryption.
Let’s get started!
Splunk is an Industry Leader in Security
Splunk is proud to be recognized as a Leader in SIEM by Forrester, Gartner® and IDC. Download the latest Magic Quadrant to see why.
Learn more about Splunk's Security Products & Solutions:
How data encryption works
The goal of data encryption is to protect information from being seen by unauthorized personnel. Practically, encryption is one way to conceal information by making it appear as random data, not useful information. Encryption can be applied to data in three primary ways:
- In transit: data in movement/being sent
- At rest: stored data
- End-to-end: across the entire data life cycle

Organizations may choose to encrypt confidential information in databases, files, documents, messages, and other communication channels over their network.
Importantly, let’s not forget that encryption can be used both for good purposes — protecting your assets — as well as for bad actions. In fact, proliferated ransomware attacks rely on speedy encryption methods to capture more files than ever before. According to research from SURGe, an in-house cybersecurity research team here at Splunk:
“…the median ransomware variant can encrypt nearly 100,000 files totaling 53.93GB in 42 minutes and 52 seconds. A successful ransomware infection can leave organizations without access to critical IP, employee information, and customer data.” – Ryan Kovar, March 2022
Types of encryption
Due to multiple types of data and various security use cases, many different methods of encryption exist. We can broadly group data encryption methods into two categories: symmetric and asymmetric data encryption.
Symmetric encryption
When using symmetrical encryption methods, a single secret key is used to encrypt plaintext and decrypt ciphertext. Both the sender and receiver have private access to the key, which can only be used by authorized recipients. Symmetric encryption is also known as private key cryptography.
Some common symmetric encryption algorithms include:
- Advanced Encryption Standard (AES)
- Data Encryption Standard (DES)
- Triple DES (TDES)
- Twofish
We’ll look at each of these shortly.
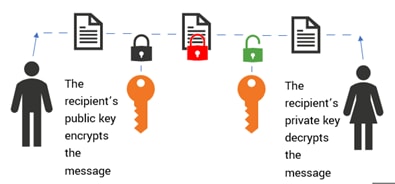
Asymmetric encryption
This method of encryption is known as public key cryptography. In asymmetric encryption, two keys are used: a public key and a private key. Separate keys are used for both the encryption and decryption processes:
- The public key, as the name suggests, is either publicly available or shared with authorized recipients.
- The corresponding private key is required to access data encrypted by the public key. The same public key will not work to decrypt the data in this technique.
Asymmetric encryption offers another level of security to the data which makes online transfers safer. Common asymmetric encryption methods include Rivest Shamir Adleman (RSA) and Elliptic Curve Cryptography (ECC).
(Related reading: public key infrastructure for cryptography.)
Comparing symmetric vs. asymmetric encryption
Aside from the fact both techniques use different key combinations, there are other differences between symmetric and asymmetric encryption.
- Asymmetric encryption is a newer method that eliminates the need to share a private key with the receiver. Importantly, however, this approach takes longer in practice than symmetric encryption.
- Symmetric encryption techniques are best suited to larger data sets but use smaller ciphertexts in comparison to the original plaintext file. (The opposite is true of asymmetric encryption.)
Within the categories of asymmetric and symmetric encryption methods are unique algorithms that all use different tactics to conceal sensitive data. We’ll explore these below.
Quick note: How hashing works
Hashing is a technique that uses a mathematical function to convert inputs of any size (files, messages, etc.) into a fixed length value.
Many people mistake hashing for being an encryption technique, but this is an important distinction to make. In hashing, there is no key, which means you cannot ensure complete privacy. Additionally, a hash can be recreated.
Hashing is typically used alongside cryptography as a method of storing and retrieving data. It's most commonly used for:
- Document verification
- Digital signatures
- Integrity controls
Common data encryption methods, algorithms, techniques
Encryption methods vary based on a number of factors, including:
- The type of keys used
- Encryption key length
- The size of the encrypted data blocks
Now let’s look at seven common methods of encryption that you can use to safeguard sensitive data for your business.
Advanced Encryption Standard (AES)
The Advanced Encryption Standard is a more secure version of the Data Encryption Standard (DES), which used a 56-bit encryption key but was vulnerable to brute-force attacks. Like DES, AES is also a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold standard for data encryption, AES is used by many government bodies worldwide, including in the US.
AES encrypts 128-bit data blocks at a time with 128-bit, 192-bit, or 256-bit keys and can be used for:
- File and application encryption
- Wi-Fi security
- VPNs
- SSL/TLS protocols
Triple Data Encryption Standard (TDES)
The Triple Data Encryption Standard, sometimes shortened to Triple DES or 3DES, is also an enhanced version of the DES algorithm. It's a symmetric encryption method that uses a 56-bit key to encrypt data blocks. As its name indicates, TDES applies DES to each block of data three times with three different keys.

Utilized by applications like Firefox and Microsoft Office, TDES encrypts things like:
- ATM pins
- UNIX passwords
- Other payment systems
Today, some industry leaders indicate that TDES is being transitioned out of certain tools and products. The overall security of AES remains superior to TDES, per NIST.
Rivest Shamir Adleman (RSA)
The Rivest Shamir Adleman algorithm is an asymmetric form of encryption. Used to encrypt data from one point of communication to another (across the internet), it depends on the prime factorization of two large randomized prime numbers. This results in the creation of another large prime number — and the message can be only decoded by someone with knowledge of these numbers.
It's extremely difficult for a hacker to work out the original prime numbers, so this encryption technique is a viable way to secure confidential data within an organization. There are some limitations to this method, primarily that it slows when encrypting larger volumes of data. Typically, though, RSA is used for:
- Smaller-scale documentation
- Files
- Messaging
- Payments
Blowfish
This symmetric encryption algorithm was originally designed to replace the Data Encryption Standard (DES). The Blowfish encryption technique uses 64-bit block sizes and encrypts them individually with a variable length key of up to 448 bits.
This data encryption method is known for its flexibility, speed, and resilience. It’s also widely available as it’s in the public domain, which adds to the appeal. Blowfish is commonly used for securing:
- E-commerce platforms
- Password management systems
- Email data encryption tools
Twofish
The next generation version of Blowfish is Twofish, a symmetric encryption technique that encrypts 128-bit data blocks. Twofish utilizes a more complicated key schedule, encrypting data in 16 rounds no matter the size of the encryption key. It’s also publicly available like its predecessor Blowfish, but it’s a lot faster and can be applied to both hardware and software.
Twofish is most frequently used for file and folder encryption.
Format-Preserving Encryption (FPE)
Another symmetric encryption algorithm is FPE: Format-Preserving Encryption. As the name suggests, this algorithm keeps the format (and length) of your data during encryption. An example would be a phone number. If the original number is 012-345-6789, then the ciphertext would retain the format but use a different, randomized set of numbers e.g. 313-429-5072.
FPE can be used to secure cloud management software and tools. Trusted cloud platforms like Google Cloud and AWS use this method for cloud data encryption.
Elliptic Curve Cryptography (ECC)
The ECC encryption algorithm is a relatively new asymmetric encryption method. It uses a curve diagram to represent points that solve a mathematical equation, making it highly complex. The shorter keys make it faster and stronger than RSA encryption. ECC can be used for:
- Web communications security (SSL/TLS protocols)
- One-way email encryption
- Digital signatures in cryptocurrencies like Bitcoin or NFTs
Data encryption challenges
Despite their obvious strengths, there are some drawbacks to encryption methods. Fortunately, careful adoption of best practices, which we’ll cover below, help overcome and mitigate these concerns.
Key management
One of the major challenges to data encryption techniques within an organization is key management. Any keys required for decryption must be stored somewhere. Unfortunately, this location is often less secure than people think. Hackers have a particular knack for uncovering the whereabouts of key information, posing a huge threat to network security and overall enterprise security.

Key management also adds another layer of complexity where backup and restoration are concerned. When disaster strikes, the key retrieval and backup process can prolong your business’s recovery operation.
(Understand how vulnerabilities and threats contribute to overall risk.)
Brute force attacks
Vulnerability to brute force attacks is a less common — though serious threat to encryption. A brute force attack is the formal name of a hacker’s attempts to guess the decryption key. Modern computer systems can generate millions or billions of possible combinations, which is why the more complex any encryption key, the better.
Today’s encryption algorithms, when used in combination with strong passwords, are usually resistant to these types of attacks. However, computing technology continues to evolve, posing an existential threat to data encryption techniques in future.
Integration with existing systems
Integrating modern encryption standards with existing applications and systems can be a challenge and might require expensive system upgrades.
Older systems might also rely on vulnerable and outdated encryption algorithms like DES, and upgrading to stronger methods may require significant changes.
Best practices for a data encryption strategy
Data encryption is one of the best ways to safeguard your organization’s data. Still, like most things, successful encryption comes down to the strategy and execution. In this section, we’ll look at some best practices to ensure your data encryption algorithms and techniques are as effective as possible.
1. Define security requirements
Scoping out the general security landscape of your organization is an important first step in any encryption strategy. Encryption systems vary in strength and processing capabilities, so it’s important to assess your current security needs before buying into a solution.
To evaluate your security posture, you can:
- Conduct a threat assessment to uncover any system vulnerabilities.
- Speak to teams and stakeholders to learn of any business decisions, existing situations, and even compliance regulations that could affect your strategy.
- Review prescriptive materials, including well-established cybersecurity frameworks.
2. Classify your data
Building on the first step, you’re ready to better understand the types of data you store and send. This includes anything from customer information to financial data and company account details and even your proprietary information that your business relies on. You can then classify each type of data by:
- How sensitive it is
- Whether and how it’s regulated
- How often it’s used and called upon
(Understand data structures & compare data lakes and data warehouses.)
3. Choose the right encryption solution
Once you’ve identified your data priorities and security requirements, you can look for data encryption tools to fit your needs. You’ll likely need to install a range of encryption algorithms and techniques to protect different forms of data across your databases, files, and applications. The best data encryption solutions are able to offer:
- Encryption at multiple levels (application, database, and file) for data both on-premises and in the cloud
- A centralized management dashboard for data encryption, encryption key policies, and configurations
- An automated life cycle process for encryption keys (both on-premises and cloud-based)
- Audit logging and shared group and role-based access controls (RBAC) to help address compliance
Use data encryption tools in addition to general security solutions like email security platforms, cloud security software, and payment gateways, as they can also encrypt data and provide added levels of security.
4. Consider any deployment obstacles
Adding to and overhauling existing security strategies is a significant change for any business. It’s therefore important to plan for any problems that could arise, such as the integration of data encryption solutions with application back-ends and legacy systems.
Ensure you have plenty of time to navigate these obstacles and consider partnering with a third-party IT provider to support your IT team with deployment.
5. Enable and collaborate for a culture of security
For your data encryption strategy to be truly successful, employees need to buy into a culture of security. Education and training on encryption key management and best practices are crucial for minimizing the human error factor of improper key storage, which can put important data at risk.
(Related reading: cyber hygiene & Cybersecurity Awareness Month.)
6. Recognize the limits of data encryption
The goal of encryption is to prevent unauthorized access to sensitive information. But your organization still requires additional cybersecurity solutions to keep hackers at bay. These include firewalls, endpoint security measures, and VPNs.
An encryption strategy should fit seamlessly into an already strong cybersecurity strategy.
(See how encryption fits into your InfoSec, or information security, strategy.)
FAQs
What is about data encryption in the context of the cloud and cloud deployments?
In the context of the cloud, encryption secures both data at rest as well as during transit.
This approach helps meet compliance requirements since frameworks like GDPR require personal data protection (essentially, encryption). It also secures sensitive data from unauthorized access in multi-tenant environments and makes sure that data stays indecipherable even in the case of unauthorized access. Bonus, it helps with customer trust.
What regulations can affect an organization's encryption strategy?
Regulations and frameworks like GDPR, HIPAA, and PCI DSS often require encryption to protect sensitive data. These laws affect encryption strategy by requiring the protection of data when it's at rest and when it's in transmission, with strict rules around key management, auditability, and data residency.
How does encryption ensure data integrity?
Encryption alone does not ensure data integrity. That's why it's often paired with cryptographic techniques like hash functions that generate a hash value — you can think of this as the data's fingerprint. Any changes in the data cause the hash value to change, signaling that the data has been tampered with. These cryptographic hash functions ensure that encrypted data stays unchanged and can be trusted when decrypted.
How does encryption help in compliance requirements?
Encryption helps meet compliance requirements by protecting sensitive data, maintaining privacy, and preventing unauthorized access. Many frameworks specifically require encryption for sensitive data (like healthcare data under the HIPAA framework) along with proper key management and audit trails.
How does encryption work alongside AI or with recent AI developments?
AI can help identify patterns and spot abnormalities in order to:
- Identify risks in encrypted data
- Analyze different threat trends to understand when an encryption method is no longer safe.
- Optimize encryption processes to improve their efficiency and strength.
AI can also automate the creation and storage of encryption keys, which can streamline key management. Plus, with techniques like homomorphic encryption, AI models can process encrypted data without exposing it, which ensures data confidentiality.
The future of data encryption techniques
An effective data encryption strategy is an essential security measure for any business. However, as we’ve seen, it's not without risk. As cyberattacks become more sophisticated and computing systems further develop, encryption algorithms and techniques must also evolve. Luckily, initiatives like next-generation quantum-safe algorithms and homomorphic encryption represent exciting new developments in data encryption. Other methods will inevitably be investigated as technology progresses.
For now, implementing an effective data encryption solution that fits your unique security needs and is deployed in collaboration with your IT, operations, and management teams is one of the best ways to safeguard your data in the modern workplace.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.



