The Continuous Monitoring Ultimate Guide: Tools, Implementation & Challenges
Key takeaways
- Continuous monitoring is the ongoing, real-time process of collecting, analyzing, and acting on data across all IT environments to detect and address threats, vulnerabilities, and performance issues before they impact users.
- It enhances security, supports regulatory compliance, optimizes performance, and improves operational efficiency by enabling rapid identification of anomalies and facilitating swift response and remediation.
- By leveraging automated tools, risk-based prioritization, and AI-assisted triage, continuous monitoring eliminates blind spots, supports Zero Trust principles, and strengthens your organization's overall security posture.
Continuous monitoring is a relatively new buzzword in cybersecurity. It's a practice where we create a system to continuously observe security threats and alert the relevant team to address the issue.
How is continuous monitoring different from normal monitoring?
- Normally, we conduct periodic monitoring, where we collect data periodically and then analyze it.
- In continuous monitoring, we analyze data as it is collected and respond to threats as we detect them.
If your SOC goals include real-time detection and response (as it should), then it is continuous monitoring that can prevent vulnerabilities from sprawling and getting out of hand, ultimately reducing damage from potential threats.
Splunk ITSI is an Industry Leader in AIOps
Splunk IT Service Intelligence (ITSI) is an AIOps, analytics and IT management solution that helps teams predict incidents before they impact customers.

Using AI and machine learning, ITSI correlates data collected from monitoring sources and delivers a single live view of relevant IT and business services, reducing alert noise and proactively preventing outages.
What are continuous monitoring systems?
A continuous monitoring system is the implementation of the concept of continuous monitoring. This system is a collection of hardware and software components used to:
- Collect data.
- Analyze that data to identify security issues.
- Alert the relevant parties.
The best way to understand a continuous monitoring system is to understand its components.
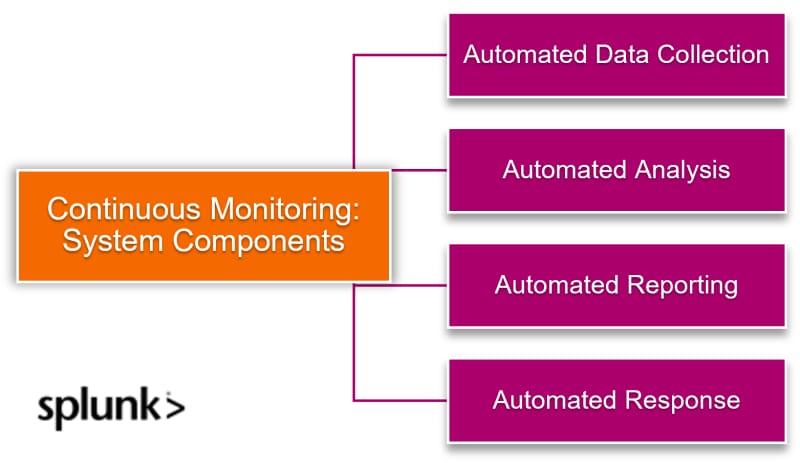
Components
Automated data collection. A continuous monitoring system uses various devices and agent plugins to collect data — such as system logs, network traffic, and application activity — providing a steady stream of information.
Automated analysis. The collected data is fed into analysis tools. These tools sift through the data, identifying patterns, anomalies, and potential security threats.
Automated reporting. Insights gained from the analysis are presented in reports and dashboards. These reports give IT staff and management a clear picture of:
- System health and performance
- Security posture
Automated response. Once the system detects an issue, it should be able to quickly alert the IT admins, and/ or take precautions such as blocking suspicious activity or even isolating infected systems.
(Related reading: incident response.)
Scope of continuous monitoring
The scope of continuous monitoring is very large as it anticipates and prevents issues from ever occurring. Fortunately, we can categorize its scope into two areas:
- Network monitoring
- Application monitoring
Network monitoring involves monitoring the traffic of your immediate network. This is to detect any potentially suspicious activity that might be indicative of unauthorized access, malware, intrusions, etc. Network monitoring also keeps an eye on performance metrics — like bandwidth usage, latency, packet loss, and network device health — to find areas for improvement.
Application monitoring also involves monitoring performance metrics but is more specific to the performance of your applications. This means it includes response times, resource utility, and error rates, allowing you to make sure that yours apps:
- Meet Service Level Agreements (SLAs).
- Deliver a good user experience.
Application monitoring also includes availability monitoring to make sure that applications are accessible to users when necessary.
(Sometimes the term “continuous monitoring” is used in the context of development and DevOps, not security. Learn more about DevOps monitoring.)
Technologies & tools
Given the large scope of continuous monitoring systems, their success highly depends on the diversity of tools you use.
Log management tools
Continuous monitoring systems should use good log management tools, such as Splunk, to collect log data from various sources about user activities. Log data is vital to have — that’s because logs are the primary sources of information about cybersecurity threats that your application and system may face.
(Related reading: log management & log monitoring.)
IT infrastructure monitoring
Monitoring IT infrastructure composed of servers, storage devices, and network devices is very important. Modern infrastructure monitoring tools can:
- Help detect potential threats such as unauthorized access, hardware failures, and unusual network traffic.
- Identify performance issues like high CPU or memory usage and network bottlenecks.
(Splunk Infrastructure Monitoring does precisely this. See how Splunk Infrastructure Monitoring works.)
Metrics dashboards & visualizations
Metrics also play a key role in continuous monitoring. Tools like Splunk or open-source solutions collect, store, and visualize performance metrics including:
- CPU usage
- Memory consumption
- Response times
Passive monitoring
Finally, NIDS (network intrusion detection systems) tools like Snort and NIPS (network intrusion prevention systems) tools like Cisco Firepower can be used to passively monitor network traffic for suspicious patterns and behaviors.
How to implement continuous monitoring
Implementing continuous monitoring can be broken down into several steps.
- Identify the objectives of your continuous monitoring system. Decide whether you want to detect security threats, performance bottlenecks, or both.
- Decide exactly which data you want to monitor, and then choose the technologies that can be used to analyze them. For instance, SIEM can be used to aggregate logs and events from various sources to identify security incidents.
- Set details and thresholds. Once you’ve selected the tools you need to monitor the specific aspects. This includes setting thresholds that would trigger an alert if it was crossed.
- Establish Response Procedures on how to react when a threat is detected. You should ensure that the relevant alerts reach the right people as the right time (often ASAP) to mitigate the threat efficiently. Particularly egregious or serious incidents may already be covered under your organizational Incident Response Plan (IRP) — if not, they should be.
- Review your continuous monitoring system often to make sure that it stays effective by evaluating whether your objectives are being met and whether your alerts are actionable.
Challenges in continuous monitoring
While continuous monitoring as a process can offer a wide range of benefits to the security and well-being of your infrastructure, it also comes with a few compromises. The following are some of the most common challenges in continuous monitoring.
- Continuous monitoring generates a massive amount of data. This can quickly overwhelm your storage and analysts. Therefore, the data should be filtered and prioritized by considering its relevancy.
- Significant resources required. To house a system that keeps an eye on your infrastructure 24/7 can demand a lot of resources. This can cost you a lot of money, require you to find skilled personnel with specific experience, and could take a lot of time.
- Orchestration across complex landscape. A continuous system needs to integrate diverse systems, applications, data sources, and tools. This can be quite complex and you could face possible compatibility issues. (This is one reason why Splunk’s platform — that unifies security and observability— is so valuable.)
- Alert fatigue. When you set up continuous monitoring, you need to generate a constant stream of alerts. The challenge here is to differentiate between genuine threats and just regular harmless alerts. This can be overwhelming to your security personnel because of the sheer volume of alerts causing alert fatigue and missing critical threats.
With the general concept and landscape of continuous monitoring laid out, let’s take a look at what happens when you pair continuous monitoring with other operational best practices.
Threat intelligence and CM
Cyberthreat intelligence includes information about the latest:
- Hacking techniques
- Malware variants
- Vulnerabilities being exploited
This information is continuously updated and curated by cybersecurity experts who analyze and aggregate data from multiple sources.
Now take that information and pair it with the capabilities of continuous monitoring: threat intelligence and continuous monitoring perfectly complement each other.
Enhancing detection capabilities
Integrating threat intelligence with monitoring tools like SIEM systems enhances their detection capabilities. For example, being aware of a new strain of ransomware allow monitoring systems to focus on identifying signs of that specific attack.
(Related reading: detection engineering & detection as code.)
Validating threats
Moreover, threat intelligence benefits from continuous monitoring by helping validate potential threats. While threat intelligence provides valuable insights, it may sometimes be based on hypothetical scenarios. Continuous monitoring helps validate these threats — by providing real-time data and observations.
Thus you can contribute to the cybersecurity community and increase your company's reputation.
(Explore CTEM: continuous threat exposure management.)
Continuous monitoring & risk management
Risk management is the process of identifying, assessing, and mitigating risks that could potentially impact an organization's objectives.
Today, many organizations rollout risk management strategies that cover their entire operations. (Others may focus on types of risk: cyber risk management, financial risk, etc.)
One of the main sources of risk? Cybersecurity threats and security vulnerabilities, of course. Therefore, having a good continuous monitoring system is an essential part of risk management.
Let’s look at some of the benefits of continuous monitoring adds to risk management.
- Proactive threat response. Continuous monitoring makes it possible to respond to threats proactively. This means taking mitigative measures before the threat escalates into a major issue.
- Comply with regulations. Continuous monitoring helps organizations maintain compliance with regulatory requirements. This reduces the risk of non-compliance penalties and legal consequences.
- Prioritization. The constant surveillance gives security teams a better idea of how to prioritize these risks based on likelihood and impact. This allows for a better allocation of resources to address the most critical risks first.
Monitoring for incidents is non-stop
Continuous Monitoring has proven to be a highly effective process in the context of risk management and threat handling. The 24/7 monitoring allows your technologies and tools to identify any anomalies in your data or user activity, allowing you to take action immediately, making it highly effective against time-sensitive threats.
Continuous monitoring can come with a fair share of hurdles, as outlined here — luckily, by choosing modern solutions from leading vendors, and following best practices, you will be in a much better state of security.
FAQs
Continuous monitoring is important because it helps organizations quickly identify and respond to security threats, operational issues, and compliance violations, reducing risk and improving overall system reliability.
The benefits of continuous monitoring include improved security, faster incident response, enhanced compliance, better operational efficiency, and increased visibility into IT environments.
Continuous monitoring works by automatically collecting and analyzing data from IT systems, networks, and applications in real time, using tools and dashboards to alert teams to potential issues or anomalies.
Use cases for continuous monitoring include security monitoring, compliance monitoring, performance monitoring, and monitoring for operational health.
Tools used for continuous monitoring include security information and event management (SIEM) systems, application performance monitoring (APM) tools, network monitoring solutions, and compliance monitoring platforms.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.


