Data Protection: Best Ways To Protect Your Data Today

Towards the end of 2023, National Public data discovered a breach where a hacker accessed names, email addresses, phone numbers, social security numbers, and mailing addresses of some 1.3 million U.S. citizens. Only later did the company, whose main service is the provision of background checks, realize that some of this data was leaked, in April and August of 2024.
As they work with law enforcement agencies to trace the hacker and to reinforce their security systems, National Public Data also must deal with the reputational fallout — including a class action lawsuit for its failure to properly secure and safeguard the PII it collected and maintained.
This is just one of the many cybersecurity cases afflicting people organizations today.
Data is the currency of the digital age. And as currency, many want to get their hands on this. That’s why protecting data has become a strategic imperative for every government, corporation, or NGO.
So how does an enterprise put in place mechanisms to protect the data it holds on behalf of consumers and other stakeholders? Data protection is how, of course, but protecting data is not an easy task for any organization.
What is data protection?
Data protection is an encompassing term for all the ways and processes used to protect and safeguard your data. There’s no “one way” to protect your data. Indeed, many ways and approaches are better than a singular path.
Data protection is important because of the risks involved for unprotected data. Failure to properly secure your data doesn’t only threaten the very existence of an organization — it also may expose your org to hefty regulatory fines and penalties, lawsuits, and other reputational issues.
With that understanding of data protection, throughout this article, we will look at risk assessment and treatment, the two main pillars of a robust cybersecurity posture that can aid organizations secure information be it at-rest, in-transit or in-use:
- Data risk assessments
- Data risk treatment
What is a data risk assessment?
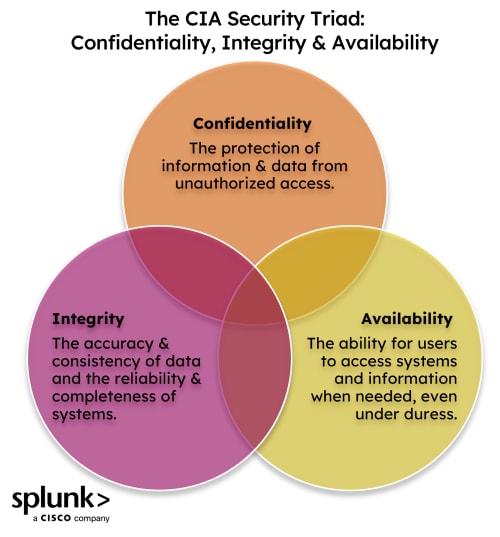
At the heart of data protection is the management of risks to its confidentiality, availability, and integrity — what’s known as the CIA triad of cybersecurity.
So, to protect your data, you must first assess the risk to your data, according to the ISO/IEC 27005:2022 guidance on managing information security risks. Perform a risk assessment. That is, identify, analyze, and evaluate threats to your data.
This assessment should be conducted systematically, iteratively, and collaboratively, drawing on the knowledge and views of stakeholders within and outside the organization. In addition, it should use the best available information, supplemented by further enquiry as necessary.
Your risk assessment is informed by the environmental context that the organization operates in and where data is created, used, and managed. The context may include:
- The social, cultural, political, legal, regulatory, financial, technological, economic and environmental factors that the organization faces.
- The requirements and needs of interested parties, such as customers and regulators.
For example, the threat landscape of a social media company is probably significantly different from a learning institution or a government agency. That context matters in determining how you’ll assess risks to the data from these varied organizations.
How to assess data risk
The activities involved in risk assessment are as follows:

Step 1. Risk identification
Identifying the risk involves finding, recognizing, and describing risks to data. How? By considering events and sources by which such threats materialize from. Organizations will consider strategic and operational scenarios, including:
- The assets they use for acquiring and managing data
- How they are exposed to risks through vulnerabilities or other events such as human error or planned attacks
Log the risks you identify in a risk register and assign an accountable owner who has the authority to address the risk.
Step 2. Risk analysis
In this step, you’ll analyze the identified risks. The goal here is to understand the characteristics of each risk including, where appropriate, the level of risk.
Analysis techniques can be qualitative (e.g. high, medium, low), quantitative (using a scale with numerical values e.g. monetary cost, users impacted, frequency of occurrence) or a combination of the two.
The two must common analysis factors used are:
a) Impact. This considers the potential consequences resulting from the failure to adequately preserve confidentiality, integrity, or availability of data. For example, an incident where a hacker has breached the network but failed to access encrypted data might be considered low impact, while a denial-of-service (DoS) attack that brings down the e-commerce website for an entire Black Friday will be deemed critical.
b) Probability. This considers the likelihood of occurrence of possible or actual scenarios that affect data security. There is high probability for a phishing attack being successful if an organization has not trained its staff or invested in anti-phishing solutions. Conversely, there may be low probability of data loss when an organization has implemented a 3-2-1 backup strategy.
The risk level is usually computed as a function of impact and probability, then mapped using a risk matrix:

Example of a risk matrix. (Image source)
Other factors you can incorporate to determine the risk level include:
- Asset value
- Complexity and interrelatedness of scenarios
- Effectiveness of existing controls
(Related reading: analyze risk using Splunk Enterprise Security.)
Step 3. Risk evaluation
Here, you evaluate the analyzed risks based on pre-determined criteria, with the goal of making informed decisions on the way forward for protecting data. Prioritize, or score, the risks to data by considering:
- The objectives of the organization
- Contractual, legal, and regulatory requirements
- The views of relevant interested parties
Should the risk levels be low compared to acceptance criteria (the risk appetite your organization has), then no further action is required. Otherwise, the risk levels will determine the approach to treatment or further analysis.
Responding to data risk: What is data risk treatment?
Risk treatment involves using the output of the risk assessment phase, above, to select and implement options for protecting data to address the prioritized risks.
The selection decision involves balancing the potential benefits derived in relation to the achieving those objectives against the costs, effort, or disadvantages of implementation.
For example, an option that involves processing and storing data in platforms hosted by different cloud service providers (CSPs) may reduce the risk of data loss, but result in increased architectural complexity and cost overruns. These options are not necessarily mutually exclusive or appropriate in all circumstances.
Strategic options for managing data risk
The ISO 31000 risk management guidelines suggest the following options:
- Avoiding the risk. The organization can decide not to start or continue with the activity that gives rise to the risk. For instance, you may decide not to not provide API access to third parties, to protect your data from the vulnerabilities that arise from poor design or configuration in third-party apps.
- Removing the risk source. You can eliminate the source of the risk when it is within your control. For example, you may decide to migrate from legacy infrastructure due to your inability to maintain them with modern security technologies and features.
- Modifying the risk likelihood or consequences. Your organization can put in place controls that limit the exposure to the risks by enhancing data protection. Controls can include encryption, anti-malware, backups, training and awareness programs, etc.
- Sharing the risk. You can enter into agreements with third parties who can bear some of the risks to data — this often happens through contracts or buying insurance cover that kicks in whenever liabilities from lawsuits or regulatory penalties arise.
- Retaining the risk by informed decision. Here, you may accept the risks by considering that existing options have been applied, and further action is not cost-effective.
(Related reading: risk management frameworks to use and TPRM third-party risk management.)
Data security controls for data protection
Finally, you can and should deploy information security controls — to decrease risk likelihood or risk consequence — and thereby protect the data you manage

Resources such as ISO 27002 guidance and cybersecurity frameworks, like NIST, are useful references for choosing data security controls. These controls can be:
- Preventive: a control that is intended to prevent the occurrence of an information security event that can lead to the occurrence of one or more consequences, such as a firewall or security awareness.
- Detective: a control that is intended to detect the occurrence of an information security event such as a guard or intrusion detection system.
- Corrective: a control that is intended to limit the consequences of an information security event, such as anti-malware or backups.
A long-time best practice for all organizations is to implement a mix of such controls to ensure they can compensate for each other — especially where an intrusion is successful on one level, i.e. defense-in-depth.
As data privacy regulations become stricter, and cyberattacks more potent, data protection has to be an ever-evolving practice that involves the input of all stakeholders to ensure that the enterprise remains vigilant and prepared to face all sorts of risks.
Maximize the value of your data with Splunk
Splunk is an industry leader in observability, cybersecurity, and data management solutions for enterprise organizations. With Splunk solutions, you can safeguard your data and maximize its full value. That means enhancing visibility, uncovering insights, and finding and fixing issues faster — all while reducing costs. Learn more about data management with Splunk.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




