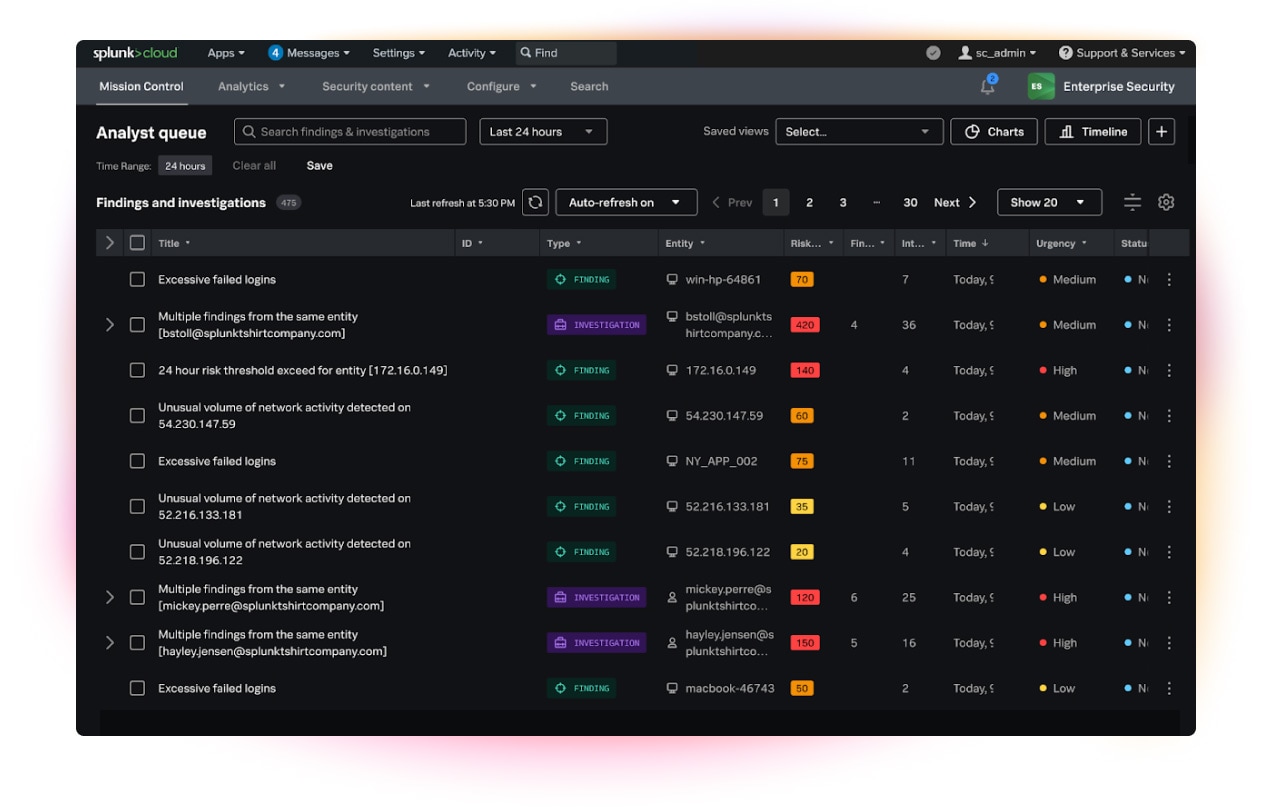
Market-leading SIEM to quickly detect, investigate, and respond to threats.
SIEM: Security Information & Event Management Explained


Splunk is an Industry Leader in SIEM
Effectively detecting, investigating and responding to security threats is not easy. SIEM can help — a lot. SIEM is cybersecurity technology that provides a single, streamlined view of your data, insight into security activities, and operational capabilities so you can stay ahead of cyber threats.
What is SIEM?
Short for “Security Information and Event Management”, a SIEM solution can strengthen your cybersecurity posture by giving full, real-time visibility across your entire distributed environment, along with historical analysis. SIEM technology can also increase organizational resilience.
To detect threats and other anomalies, SIEM ingests and combs through a high volume of data in seconds to find and alert on unusual behavior — a task that would otherwise be impossible to execute manually. A SIEM tool can provide a snapshot of your IT infrastructure at any given moment. This ability to analyze data from all sources in real time — including network applications, hardware, cloud and SaaS solutions — can be critical to helping organizations stay ahead of internal and external threats.
In this article, we’ll explore the essential features and functions of SIEM technology and how to choose the right SIEM tool.
State of SIEM: Growth trends in 2025
Introduced by Gartner® in 2005, SIEM technology has evolved into a critical tool for Threat Detection, Investigation, and Response (TDIR). Combining Security Information Management (SIM) and Security Event Management (SEM), SIEM now supports comprehensive cybersecurity management, control, and compliance.
Market growth and trends
The SIEM market is growing at a 14.5% CAGR, projected to reach $11.3 billion by 2026 from $4.8 billion in 2021. Key growth drivers include:
- Increasing cybercrime: Rising scope and scale of attacks drive demand for robust threat detection.
- IT service expansion: More organizations rely on real-time data processing.
- Complex IT ecosystems: Cloud adoption challenges make SIEM indispensable.
Challenges and solutions
The average cost of a data breach has risen to $5.2 million globally and $10.1 million for U.S. firms in 2023. Meanwhile, a global cybersecurity skills gap leaves millions of positions unfilled, emphasizing the need for intelligent automation in SIEM.
In 2025, SIEM remains vital for safeguarding digital infrastructure. All of this underscores why organizations increasingly rely on intelligent automation SIEM capabilities: you need to stay ahead of growing security threats, so you must make sense of events log data at scale.
How does SIEM work?
So, let’s talk about IT events, incidents and log data at scale: security information and event management. A SIEM solution aggregates event data across disparate sources within your network infrastructure, including servers, systems, devices and applications, from perimeter to end user.
(A note on pronunciation: Typically, SIEM is pronounced as “sim”. You may see it spelled as “SEIM” or pronounced “seam” as well: likely we’re all talking about the same thing.)
Ultimately, a SIEM solution offers a centralized view with additional insights, combining context information about your users, assets and more. It consolidates and analyzes the data for deviations against behavioral rules defined by your organization to identify potential threats. Data sources can include:
- Network devices: Routers, switches, bridges, wireless access points, modems, line drivers, hubs
- Servers: Web, proxy, mail, FTP
- Security devices: Intrusion prevention systems (IPS), firewalls, antivirus software, content filter devices, intrusion detection systems (IDS) and more
- Applications: Any software used on any of the above devices
- Cloud and SaaS solutions: Software and services not hosted on-premises
Attributes that may be analyzed include users, event types, IP addresses, memory, processes and more.
SIEM products will categorize deviations as, for example, “failed login,” “account change” or “potential malware.” A deviation causes the system to alert security analysts and/or act to suspend the unusual activity. You set the guidelines for what triggers an alert and establishes the procedures for dealing with suspected malicious activity.
A SIEM solution also picks up on patterns and anomalous behavior. That way, if a single event alone does not raise a red flag, the SIEM can eventually detect a correlation across multiple events that would otherwise go undetected, triggering an alert.
Finally, a SIEM solution will store these logs in a database, allowing you to conduct deeper forensic investigations or prove that you are complying with applicable regulations.
A SIEM solution brings together data across disparate sources within your network infrastructure
Transition to cloud-based SIEM solutions:
The shift towards cloud computing has led to the development of cloud-native SIEM solutions, offering several advantages over traditional on-premises systems:
- Scalability: Cloud SIEMs can effortlessly scale to accommodate increasing data volumes, making them suitable for organizations of all sizes.
- Flexibility and accessibility: Being cloud-based, these SIEMs provide access from anywhere, facilitating remote monitoring and management of security events.
- Cost-effectiveness: They reduce the need for significant upfront investments in hardware and maintenance, operating on a subscription-based model that can be more economical.
- Integration with cloud services: Cloud SIEMs are designed to integrate seamlessly with various cloud platforms and services, ensuring comprehensive security monitoring across diverse environments.
The transition to cloud-based SIEMs further offers scalability, flexibility, and cost benefits, making them a compelling choice for organizations aiming to strengthen their security posture in today's dynamic digital landscape.
Benefits of SIEM
SIEM technology helps your security analysts see across your enterprise IT environment and spot threats that evade other means of detection. A good SIEM solution will help security analysts do their jobs better and can help an organization solve three major security challenges:
- Visibility. A modern SIEM provides real-time status updates into your security posture — retrieving and maintaining contextual data around users, devices and applications from across on-premises, cloud, multicloud and hybrid environments. This makes it easier for security analysts to spot bad actors and zero in on threats.
- False alerts. A SIEM solution can help reduce the number of false positive alerts, so security analysts can quickly detect and investigate actual threats and not waste time on false alerts. Potential threats are identified, categorized and triggered via dashboards, then sent to an analyst for review.
- Flexibility and scalability. Many SIEM solutions offer support for and integrate with a wide array of environments and technologies, as well as across internal and external teams. A modern SIEM can meet your needs now and in the future, especially as your tech footprint expands.
In all, the benefits of SIEM help enterprises prevent costly breaches and avoid compliance violations that entail hefty financial penalties and reputation loss.
Comparing SIEM vs. other cybersecurity solutions
Yes, the cyber landscape is littered with threats—and also acronyms of various technologies, solutions and approaches. So, SIEM might remind you of other terms you’ve heard. Let’s clear that up.
The role of UBA in SIEM
Other tools have made their way into the SIEM space, particularly user behavior analytics (UBA). Also known as user and entity behavior analytics (UEBA), UBA is used to discover and remediate internal and external threats.
While UBA is often seen as a more advanced security tool, it’s increasingly folded into the SIEM category. For instance, the Gartner Magic Quadrant for SIEM includes information about UBA/UEBA offerings.
UBA works in two ways:
- Creating a baseline for any user or application’s data. Then, highlighting deviations from that norm that could be a threat.
- Monitoring malicious behavior and preventatively addressing security issues.
These functions play a critical role in any SIEM solution as they illuminate patterns of behavior within the organization’s network, offering context you didn’t have before. They also filter alerts before the security operations center (SOC) team is notified — helping reduce alert fatigue and freeing up analysts’ time for more complex or urgent threats.
A SIEM solution can help a high-functioning SOC detect and thwart threats and proactively improve security.
How SIEM & SOAR compare
SOAR is a different cyber technology, and it standard for “security orchestration, automation and response”. SIEM and SOAR both do work that would be impossible to tackle manually, as they both process and analyze data across an organization's environment. Here’s a brief summary from our SIEM vs. SOAR comparison:
- SIEMs provide valuable insight into cyber threats by aggregating and analyzing security data from various sources.
- SOARs prioritize and respond to security incidents effectively by leveraging machine learning-driven automation and orchestration capabilities.
Many enterprises deploy SIEM and SOAR solutions in tandem.
SIEM & XDR
XDR, which stands for extended detection and response, assists with endpoint threat detection, investigation and response. It provides a single platform that helps streamline triage, validation and response processes so SOC analysts can more efficiently perform these tasks.
There are two major differences between SIEM and XDR. XDR tools limit the data they take in, while SIEM ingests data from any and all sources. By limiting data ingest, XDR tools improve the scope and accuracy of their endpoint threat detections. However, XDR may not be as well-suited, for example, to use while investigating fraud, as such investigations tend to span across multiple systems and solutions.
Unlike SIEM, XDR solutions don’t have the capacity to provide long-term storage capabilities. That means you’ll likely have to store data elsewhere to fulfill compliance and auditing requirements. XDR systems, however, are typically more straightforward to assemble and run than SIEM platforms.
(Learn more about EDR, MDR & XDR.)
Practical security: SIEM tools
Your SIEM tool is essentially an analytics-driven security command center — it’s often the centerpiece of a highly functional SOC. All event data is collected in a centralized location. The SIEM tool does the parsing and categorizing for you. More importantly, it provides real context about security events across your infrastructure.
SIEM technologies vary in scope, from basic log management and alerting functionality to robust real-time dashboards, machine learning and the ability to conduct deep dives into historical data for analysis. Leading solutions may provide dozens of dashboards, including:
- An overview or detailed view of notable events
- A workbook of all open investigations
- Risk analysis with scoring systems
- Threat intelligence, user intelligence, web intelligence and protocol intelligence for added context
The end-to-end SIEM process starts from data collection and ends with a mechanism for automating issue resolution and compliance reporting. Intelligence and automation are the key components of a SIEM system that enable individual functions of the SIEM process workflow.
7 critical features in SIEM tools
There are plenty of SIEM solutions out there, some more comprehensive than others, others more modern than legacy systems. As you’re evaluating, keep in mind these critical SIEM functions that any modern SIEM should have:
Data aggregation and seamless log management
First things first: A modern SIEM must be able to collect, analyze, and monitor any data from any source, in any structure, at any time scale from across an ecosystem of teams, tools, peers and partners. This can give any SOC a unified view into what’s going on across the security stack in real time. It also provides the ability to:
- Manage event logs from one central location.
- Correlate different events over multiple machines or multiple days.
- Tie in other data sources like registry changes and ISA Proxy logs for the complete picture.
Not only should your SIEM be able to collect data from hundreds, even thousands of sources, but it must offer a user-friendly, intuitive interface that you can actually use to manage and retrieve log data. This log data will play into more areas of SIEM:
- Data orchestration and management: data cleansing, normalization, transformation, enrichment, transformation, standardization and movement across the data platform
- Forensics and investigation: real-time monitoring, data analytics, anomaly detection and event correlation
- Automated threat remediation
- Compliance management and reporting
Real-time security monitoring and analysis
The longer you wait to address attacks or known threats, the more damage they do. Your SIEM should offer you a real-time, bird’s-eye view of what’s happening within your network, including:
- Activity associated with users, devices and applications.
- Any activity not specifically attached to an identity.
You need monitoring capabilities that can be applied to all data sets no matter their origin. Beyond the monitoring aspect, you need the ability to synthesize the information into a format that’s usable. Choose a SIEM with:
- A library of customizable and predefined correlation rules
- Out-of-the-box correlation searches
- A security event console for a real-time view of security incidents and events
- Dashboards that provide live visualizations of threat activity
Incident investigation, forensics, and response
Chances are your security team spends too much time investigating low-value alerts with too little context. Improperly defined detections can lead to a high volume of false positives and a lot of extra noise, quickly overwhelming and overburdening anyone on the front lines. A modern SIEM is able to:
- Visualize and correlate data.
- Map categorized events against a kill chain.
- Provide insight into which tactics have been used by an adversary that map to a particular known vector.
Risk attribution can also help optimize threat hunting and reduce the volume of alerts — thereby increasing true positives — while surfacing more sophisticated threats, like low and slow attacks
User monitoring
At the most basic level, your SIEM tool should offer user monitoring that analyzes access and authentication data, establishes user context, and provides alerts relating to suspicious behavior and violations of corporate and regulatory policies.
If you are responsible for compliance reporting, you may also need to monitor privileged users — users who are especially likely to be targeted by an attack — a common requirement for compliance reporting in most regulated industries.
Threat intelligence and detection
Your SIEM should help you identify key external threats, such as known zero-day exploits and advanced persistent threats. Threat intelligence helps you to recognize abnormal activity and to identify weaknesses in your security posture before they're exploited. That way you can plan responses and remediate properly.
This information then informs your detection capabilities.
Risk-based alerting
Traditional cybersecurity alerting relies on tools that forward data to a SIEM, where detection logic or vendor-provided content generates alerts for potential threats. However, this approach often overwhelms Security Operations Centers (SOCs) with excessive alerts, leading to abandoned or ignored alerts, delayed responses, and analyst burnout.
Risk-based alerting addresses these challenges by consolidating noisy alerts into fewer, high-priority incidents based on risk attribution. This method correlates related events into a single incident, enhancing investigation and response efficiency. Key benefits include:
- Tagging observations with security metadata (e.g., alert source, ATT&CK technique, and scores).
- Dynamically adjusting risk scores based on object attributes, such as privileged user involvement or external server exposure.
- Triggering alerts only when sufficient correlated observations are present.
This approach streamlines security operations, reduces noise, and improves incident resolution.
Advanced analytics and machine learning
All the data in the world won’t help you if you can’t use it to gain clear insights. Advanced analytics employs sophisticated quantitative methods, such as statistics, descriptive and predictive data mining, simulation and optimization to provide deeper insight.
SIEM tools powered by machine learning are capable of learning over time what represents normal behavior and what is a true deviation, improving their accuracy. This is especially critical today, given that technology, attack vectors and hacker sophistication evolve faster than ever.
Best practices for getting started with SIEM
To maximize the value of your SIEM solution, it's essential to align it with your business needs, industry risks, and long-term security goals. Follow these best practices to build a solid foundation and realize the full potential of your SIEM:
Plan thoroughly
- Define specific goals for your SIEM deployment.
- Prioritize use cases, considering data requirements, network size, compliance obligations, budget, and staff expertise.
- Factor in future growth and security maturity, starting with basic capabilities and evolving to advanced features like User and Entity Behavior Analytics (UEBA) and Security Orchestration, Automation, and Response (SOAR).
Outline use cases and security roadmap
Identify your organization’s security objectives. Ensure your SIEM receives complete, accurate, and actionable data. Its effectiveness depends on the quality of data fed into the system.
Maintain and continuously improve
SIEM is not a "set-and-forget" tool. Regular reviews and adjustments are necessary to adapt to evolving business and security needs.
Fine-tune alerts
Define criteria for generating alerts and ensure SIEM responses are well-calibrated to focus on genuine threats. Continuously refine alert settings to reduce false positives and maintain operational focus.
Invest in skilled staff
- Train personnel to implement, manage, and maintain the SIEM.
- Recognize that while SIEM simplifies security management, it requires human expertise for fine-tuning and adapting to changes in the IT environment.
By carefully planning, maintaining, and optimizing your SIEM deployment, you’ll enhance your security operations while staying aligned with your organization's evolving needs.
Choosing your solution: what’s the best SIEM?
That’s the question that will inevitably follow once you have a basic understanding of SIEM: How do I choose the best SIEM solution for my industry, threat profile, organization and budget?
This depends on what you’re looking for. You want something that can handle modern volumes of data, the sophistication of today’s attacks, and the need to drive smart, real-time incident response.
Analyst takes on SIEM
When it comes to SIEM, there are a variety of analyst reports that help customers, vendors and the providers themselves understand what they need and what options are out there. These firms survey the given industry and understand its strengths and weaknesses, positioning and future growth and outlook. Among the biggest analyst firms are Gartner, Forrester and IDC. Here are some of the most common SIEM analyst reports:
Splunk Named SIEM Leader 10 Years Straight
See why Splunk has been named a Leader - again - in the 2024 Gartner Magic Quadrant for Security Information and Event Management (SIEM). Get The Report
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.