Massively Scalable Data Analytics Platform
Federal IT leaders face multiple priorities, from modernization to risk management to citizen experience improvements, and they are increasingly turning to data-driven strategies. Only Splunk offers a cost-effective, extensible everything and massively scalable data platform that helps that helps agencies make confident decisions and take action at mission speeds.
Splunk Enterprise is under evaluation for Common Criteria certification (VID #11016) by the National Information Assurance Partnership (NIAP). Splunk Cloud meets FedRAMP security standards at the Moderate Impact Level, accelerating time-to-value. The Splunk Cloud FedRAMP service also meets U.S. Persons requirements under ITAR and is ISO 27001 certified.
- Maximize ROI by ingesting data once and using it across multiple agency challenges, be it cybersecurity, citizen service or modernization initiatives
- Drive modernization initiatives such as DCOI, application rationalization and cloud migration efforts with confidence and ease
- Proactively manage risk and meet various compliance mandates with the security analytics platform of choice among government agencies
- Reduce human tedium, identify hard-to-find patterns and predict issues before they adversely impact the mission with AI/ML technologies


United States Census 2020
At the core of our fusion center are Splunk's dashboards and reports, which leadership relies on to know what's going on and make better decisions.
Continuous Diagnostics and Mitigation
Splunk is the data integration platform of choice for DHS’s Continous Monitoring and Diagnostics (CDM) program, enabling real-time visibility and automated response and reporting to meet agency objectives across all its program phases. Its seamless ingestion and data transformation capabilities help agencies aggregate, report and share critical security and risk information, while automation quickens response time across all four program phases.

Insider Threats
While the signs that you may have a malicious insider are varied, the analysis and data types needed for discovery are almost always the same. Splunk correlates system and security logs with organizational and external context to detect malicious insider activity. Using statistical analysis, personal-activity comparative analysis, and user-activity context analysis, Splunk technology can correlate these key data types with user activities to provide a more complete story around suspected malicious behavior.
- IT system and security logs: Any data generated by the user as a result of credentialed human-to-machine activities
- Organizational context: Information about the employee - usually contained in a business system such as an HR database or time management system
- External context: Data that an employer can access as a result of an employment agreement, especially for those handling sensitive information or intellectual property

Cybersecurity
Traditional perimeter-based defense approaches are ill-equipped to handle today's sophisticated security threats. Splunk solutions for big data are ideal for detecting patterns and discovering malicious behavior and attacks not seen by signature and rule-based systems.
Splunk customers gain the most value and the fastest incident response times when capturing data from traditional security point solutions and from credentialed user-to-machine interactions and then combining this data with IT operations data for additional context. Recognized by Gartner as a leader in the SIEM magic quadrant, Splunk can complement existing SIEM deployments or replace them.
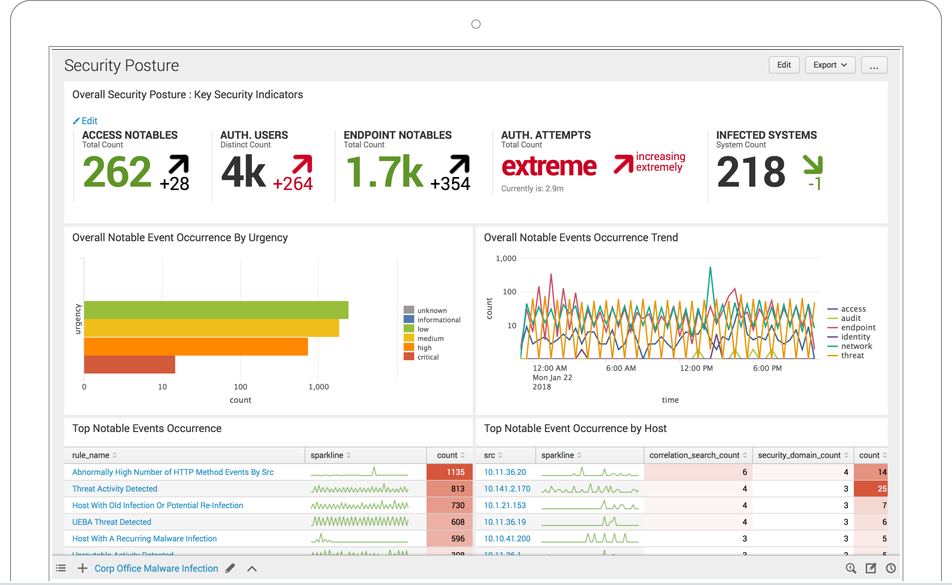
Fraud
Fraud at government agencies is growing at an alarming rate and includes activities like the "social engineering" of call center personnel, "water-holing" schemes, phishing attacks and applications for undeserved benefits. Call data records, XML forms and structured data residing in a database are all sources of information that can be used to analyze and detect fraud.
Splunk provides multiple checks to monitor and proactively prevent fraud by:
- Using trended statistical analysis
- Applying logic to data collected in forms and watching for illogical patterns
- Performing look-ups to external sources of data
- Automatically interacting with other systems based on the search results
Thousands of private sector companies in the telecommunications, education, and financial services industries rely on Splunk to protect them against financial losses from fraud.




