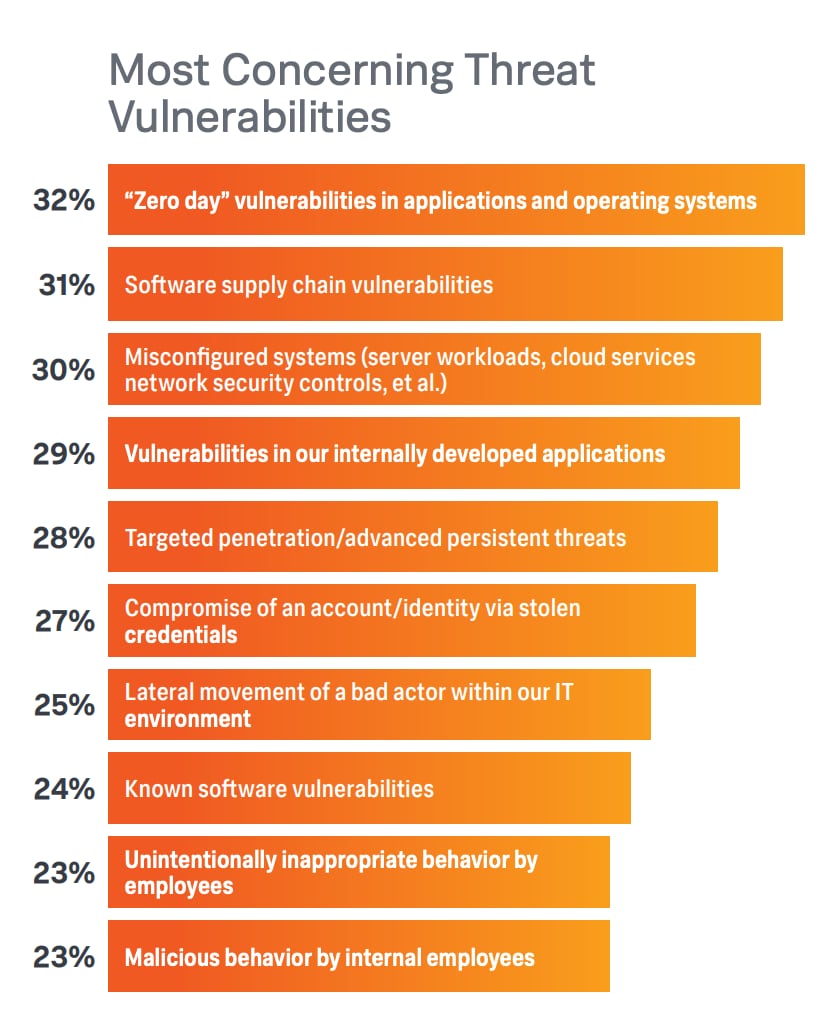
1. Supply chain
Software supply chain attacks are top-of-mind in the post-SolarWinds (and Log4j, and Kaseya, and ...) era. Fully 95% of organizations have increased their focus on third-party risk assessment activity, up from an already noteworthy 90% a year ago. Top responses to threats include assessing security controls to understand prevention and detection capabilities specific to supply chain attacks, hardening authentication systems and increasing security budgets.
2. Ransomware
Since the 2022 State of Security research, the percentage of organizations reporting that they had not yet been hit with a ransomware attack dropped from 21% to just 13%. There’s a wide range of tactics to combat ransomware, but two are more widespread with 33% adoption among respondents: investment in security information and event management (SIEM) solutions and focus on email security. Moreover, 91% of respondents agree that better capture and analysis of detection data is one of the most effective tools to prevent successful ransomware attacks.
3. Cloud security.
Respondents’ top three cloud security challenges are maintaining security consistency across their data center and public cloud environments (reported by 45%), keeping identity and access management (IAM) systems accurate and up-to-date (32%), and managing increasing cost and complexity of multiple cybersecurity controls (28%). Tactics in response to these challenges include identifying workload configurations that are out of compliance and/or don’t adhere to industry best practices (30%), configuring security groups (e.g., externally facing server workloads) (25%), and improving audit trail understanding among privileged and service accounts (24%).
These are just three challenges that threaten a CISO’s agenda. But it’s not all doom and gloom — we know more than we once did about how to prevent and remediate a supply chain attack, for one. Every cyber incident is a lesson learned, and the industry as a whole is more prepared than before for whatever arises.
For more recommendations on how to face today’s security challenges, read the full State of Security report.