Splunk recognizes that financial services institutions (FSIs) must comply with stringent regulations regarding outsourcing, cloud services, and third-party risk management. Across global regulatory frameworks, FSIs are required to ensure that their cloud and solution providers maintain robust security, data protection, resilience and risk management practices. While FSIs are ultimately responsible for compliance with these regulations, Splunk offers a dedicated program specifically designed to help FSIs meet material regulatory requirements applicable to Splunk as a vendor providing cloud services. Our program is tailored to provide Splunk FSI customers with the necessary assurances to confidently rely on Splunk. This page outlines our FSI program and governance, including the certifications, attestations, terms, and documentation we provide to support due diligence, contracting and oversight responsibilities of our FSI customers.
Continue reading to discover how Splunk addresses the specific needs of the FSI sector.
Financial Services FAQs
Splunk has developed a dedicated program for our customers in the FSI sector who are subject to regulations concerning outsourcing, third-party risk management, and cloud services. Our program takes into account a range of global regulations detailed in the ‘What regulations has Splunk considered when building its FSI programs?’ section below.
More information about Splunk’s approach to FSI regulations is available in our Splunk and Financial Services white paper which offers in-depth insights into how our FSI program helps customers maintain compliance and manage risk.
Our FSI program includes:
- Robust security program
We protect our Cloud solutions and your customer data against threat actors, unauthorized access, destruction, loss, alteration, or unauthorized disclosure or access. To achieve this, we have implemented comprehensive security measures, including administrative, technical, and organizational safeguards and controls. Our program includes:
- Detailed information security policies and procedures;
- Ongoing security awareness training;
- A continuously updated threat and vulnerability management program;
- Incident response framework; and
- Vendor risk management program.
We align our offerings with recognized industry standards, verified by independent third party audits, such as ISO/IEC 27001, SOC2 Type II, PCI-DSS, or FedRAMP [moderate].
We also provide contractual commitments to our customers through offer-specific security addenda, which are incorporated into Splunk customer agreements.
The ways we adhere to global and industry compliance standards are described on our dedicated security and privacy website, Splunk Protects. For Splunk Cloud Platform and Observability Cloud, we have developed Cloud Security Principles in response to the UK National Cyber Security Centre’s (NCSC) Cloud Security Principles, outlining our approach to product security.
- Business continuity and resilience management program
We recognize the importance of minimizing potential interruptions to Splunk’s critical business functions, especially those that may affect the availability of Splunk offerings to customers. To mitigate this risk, we maintain an enterprise-level business continuity and disaster recovery program, governed by our Business Continuity (BC) and Disaster Recovery (DR) Management Policy aligned with the ISO22301 Standard for Business Continuity.
- Performance management, monitoring, and audit rights
We facilitate precontractual assessments of our security posture by providing comprehensive information on the Customer Trust Portal and responding to security questionnaires. Once under contract, customers can easily access, or receive via email upon subscription, system status (availability) information. Issues impacting the performance of Splunk offerings are promptly notified to customers, who can then consult security advisories regarding product vulnerabilities and our remediation or recommendations aimed to reduce risk. Finally, our three-tier audit program allows customers to periodically verify Splunk’s compliance with the standards committed to in our contracts.
- Strict subcontracting rules
We maintain a third-party vendor management program to oversee our subcontractors. It includes assessment and audit rights to ensure subcontractors meet Splunk’s requirements. Splunk contracts with subcontractors incorporate key obligations such as security, privacy, confidentiality, and integrity. Additionally, subcontractors must adhere to our Supplier Code of Conduct, ensuring they conduct business ethically and legally. These principles, along with our commitment to sustainability, are reflected in the Splunk Code of Conduct and Ethics. We also publish a list of our subprocessors, their locations, and what services they support. Customers can subscribe to receive notifications about additions to this list.
- Efficient termination and data portability rules
We recognize that sector-specific regulations may require early termination rights. We grant these rights to our FSI customers under specific conditions. For such exceptional circumstances, we have established processes to reduce undue impacts on our customers’ operations by facilitating data migration. Our governing agreements outline these rights, transition services and the specific modalities for data retrieval, migration, or deletion, as further detailed in the applicable product documentation.
We rely on independent third-party audits to demonstrate that our offerings align with recognized industry standards. We are certified for ISO/IEC 27001, SOC2 Type II, PCI-DSS, and FedRAMP [moderate]. Additionally, Splunk Cloud complies with NIST SP 800-171 (CUI) and U.S. Persons requirements under ITAR.
We have designed the Splunk FSI program with consideration of key regulations applicable to FSI customers. Below is the exemplary list of these key regulations:
- European Banking Authority (EBA) Outsourcing Guidelines 2019
- European Union MiFID II Organisation Regulation (Articles 30 and 31)
- Bank of England Prudential Regulation Authority (PRA) Supervisory Statements on Outsourcing and third-party risk (SS2/21) and Operational Resilience (SS1/21)
- European Union Solvency II Directive
- European Insurance and Occupational Pensions Authority (EIOPA) Guidelines on Outsourcing to Cloud Service Providers (with respect to insurance and re-insurance undertakings)
- Guidance issued by the United States Federal Banking Regulators (OCC, FDIC, and Federal Reserve) and Federal Financial Institutions Examination Council (FFIEC) on outsourcing and third-party risk
- Monetary Authority of Singapore Outsourcing Guidelines 2018
- Canada Office of the Superintendent of Financial Institutions (OFSI) Third-Party Risk Management Guidelines (revised B-10)
- Australian Prudential Regulation Authority (APRA) Prudential Standard CPS 231 (outsourcing) and CPS 234 (Information security)
- Financial Services Agency of Japan (JFSA) Comprehensive Guidelines for the supervision of major banks and other FSIs
We continuously monitor regulatory changes to stay informed about amendments or new requirements and evaluate them in a timely manner.

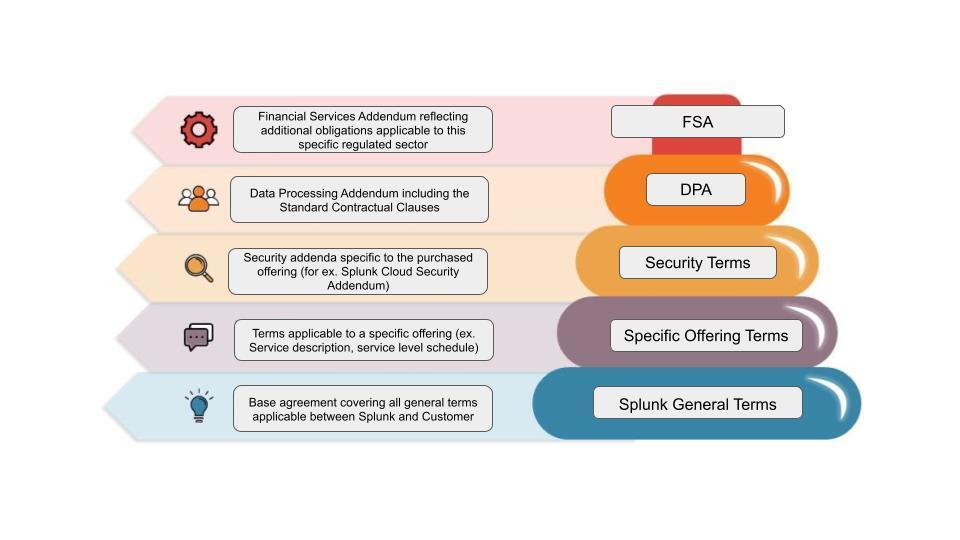
Yes, FSI-specific requirements, along with our additional commitments, are included in the Splunk Financial Services Addendum (FSA) that we offer to Splunk customers in the FSI sector. The FSA complements the Splunk contractual framework, as illustrated in the diagram below (highest priority document first):
The European Union’s Digital Operational Resilience Act (DORA) was designed to strengthen the digital resilience of FSIs by addressing risks in Information and Communications Technology (ICT). Enacted in January 2023 and enforceable from January 2025, various standards issued under DORA are being finalized through July 2024. DORA applies directly to FSIs and also extends to ICT vendors designated as critical third-party ICT providers to FSIs (CTPPs).
We have robust programs in place to address each of the DORA requirements for outsourcing to third-party ICT providers. Our programs are supported by auditable internal policies and plans and standard operating procedures, including:
- ICT risk management: We maintain formal, robust risk management programs at the enterprise level and product security-focused. Our risk management programs are designed to identify, assess, prioritize, and mitigate or remediate important risks.
- Incident management and notice: We maintain formal, robust incident management programs that are both security-focused and tied to product operations. We have prompt, focused notification processes for customers.
- Resilience testing: We conduct penetration and other security testing, as well as BC/DR testing internally and using industry-recognized third-party vendors, at least once a year.
- Vendor risk management: Our posted Supplier Code of Conduct and Code of Business Conduct and Ethics provide general insight into Splunk vendor risk management. We initially and annually assess/re-assess our key vendors and enforce requirements through contracts.
- Monitoring/auditing: We have a Splunk System Status page for ongoing monitoring and a Customer Audit Program with a wealth of online documentation available at Splunk’s Customer Trust Portal.
We understand the importance of DORA to our customers. Although Splunk has not been designated as a critical third-party ICT provider (CTPP), and the DORA standards have not yet been finalized, we have assessed the regulation and identified our programs that address each of the DORA requirements for outsourcing to third-party ICT vendors (see question above). We continue to assess the detailed standards issued under DORA as regulators finalize them and are actively working to mature our programs to meet the anticipated requirements outlined in the DORA standards. Examples of our maturation efforts include:
- ICT risk management: connecting our various risk management programs across the business more formally.
- Incident management and notice: expanding and streamlining our incident response programs to accommodate tighter notification timelines and more frequent and detailed notification obligations for our customers.
- Resilience testing: enhancing customer transparency in our penetration testing program and operationalizing customer engagement.
- Vendor risk management: enforcing additional contractual requirements in our arrangements with key subcontractors.
- Monitoring/auditing: incorporating additional information into our Customer Audit Program.
We have extensive experience in working with customers from the FSI sector, including banks, payment providers, and insurers. We are committed to building digital resilience in the FSI ecosystem and contributing to the creation of safer, more reliable institutions.
You can read more about how Splunk can help you achieve your digital resilience here.
You can also learn about inspiring use cases in the FSI sector to see how Splunk has helped its customers.
(May 2024)


