Splunk SOAR Playbook of the Month: Threat Hunting with Playbooks

As SOCs continue to grow and mature, it's vital that they establish effective and repeatable programs in proactive defense. This also means that threat hunting needs to become a critical function. Numerous advanced and sophisticated threats are able to get past more traditional cybersecurity defenses and SOCs need skilled Threat Hunters who are able to search, log, monitor, and remediate threats before they create a serious problem.
Luckily, Splunk SOAR can help Threat Hunters easily identify potential threats in their environment through the power of automation via the Hunting playbook. For this month’s edition of Playbook of the Month, we’ll look at how you can use Splunk SOAR’s Hunting playbook to perform threat hunting activities at machine speed.
What is Threat Hunting?
A threat hunter's job is to find the unknowns. Threat hunters conduct analysis through vast amounts of security data, searching for hidden malware or signs of attackers by looking for patterns of suspicious activity that may not have been uncovered by tools. They also help develop in-depth defense approaches by understanding attacker tactics and techniques so they can help prevent that type of cyberattack. They use common frameworks such as MITRE ATT&CK to help adapt them to the local environment.
The Playbook
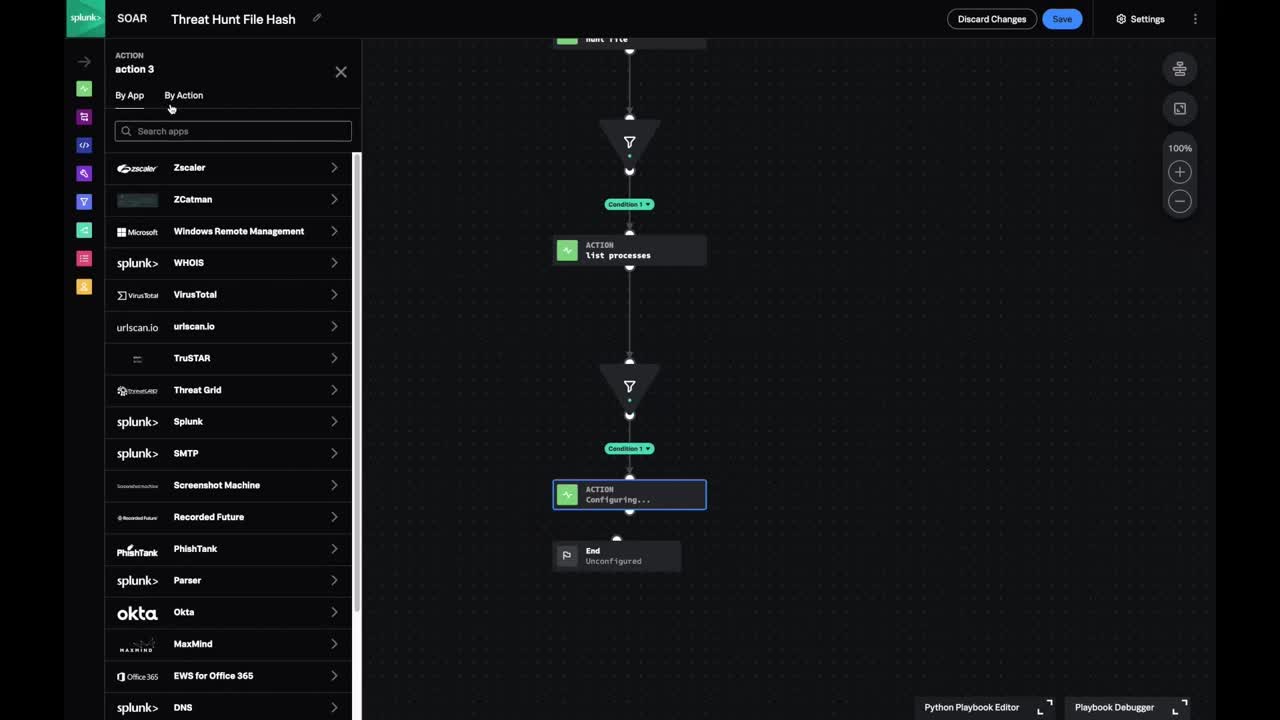
The Hunting Playbook queries a number of internal security technologies in order to determine if any of the artifacts present in your data source have been observed in your environment. Here’s how to use it:
Initial Setup
- Load a CSV from a threat feed into Splunk SOAR via the “Add events” button
- Select the newly created Event. From the “Files” tab, either select the CSV from the “Browse Files” button or drag the file into the “Drop Files to Upload” field.
- Select the Vault ID that displays for the file and select the “Run Action” tab. Extract the necessary data from the file by selecting “Generic > extract ioc.” From the “Run action” window that appears, adjust the file type field to CSV, enter your container ID, and then press the “Launch” button in the lower right corner.
- On the “Artifacts” tab, select the 3 dots in the upper right corner to open a drop down menu and make sure that the fileHash option is checked off under the “Data Fields” section. This will display the fileHash for each artifact you have via a hyperlink.
Customizing the Playbook
- From the Playbook screen, search for the “Hunting” prebuilt playbook and open it.
- Select the “Hunt File” action block and adjust The hash* field under “Inputs” to “fileHash”
- Add a filter block and set the parameter to hunt_file_1 > device_count. Select the “Greater than” condition and set the specified value to 0.
- From this filter, add an action block to “list processes” and adjust the ioc* input to “filter_1 > hash” and the id* to “filter_1 > device_id.”
- Add an additional filter to the previous action blog with the settings “list processes_1 > process_count. Select the “Greater than” condition and set the specified value to 0.
- From this filter, add an action block to “get process detail” set the process_id* value to “filter_2 > process_id.”
- Save this custom playbook
Running the Playbook
- Click the “select all” checkbox from the Artifacts tab.
- Click the “More” button in the upper right corner and select the “Run Playbook” option from the drop down menu.
- Search for your custom playbook, select it, and then hit the “Run Playbook” button
Watch the video to see this playbook and setup process in action.
And with that, you now have a playbook to help you automatically hunt for indicators of compromise, identify those threats in your environment, learn the details of the affected machine, and learn how to better explore the affected file system.
Be sure to check out research.splunk.com/playbooks to explore even more useful playbooks. Additionally, if you haven’t seen last month’s blog and video, be sure to give them a look here. We look forward to hearing about your experience with this month’s featured playbook as well as any other playbooks you’ve recently implemented. We’ll be back next month with more playbooks and demos, but until then, get out there and get automating!
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




