Splunk SOAR Playbook of the Month: Splunk Attack Analyzer Dynamic Analysis
Alert triage can be a very cumbersome and time consuming process for SOC teams. Our State of Security report found that 26% of respondents agree that the volume of alerts they deal with makes it difficult to keep up with addressing emergencies.
While tools like virtual sandboxes can help analysts better test and understand the severity of the threats they encounter, the process of testing and documenting results can add further tedium to an already prolonged process.
Splunk Attack Analyzer automates threat analysis
Splunk Attack Analyzer can help SOC teams automate these key threat analysis tasks by performing the actions required to fully execute an attack chain, including:
- Clicking and following links
- Extracting attachments and embedded files
- Dealing with archives
- And much more
When paired with Splunk SOAR, Splunk Attack Analyzer can conduct automated analysis of identified indicators without SOC analysts having to perform manual investigative tasks.
These two products can be used together to help SOC teams tackle a variety of security use cases and reduce the time consuming staring on the alert triage process.
For this month’s edition of Splunk SOAR Playbook of the Month, we’ll be taking a look at how you can use one of our out-of-the-box playbooks for faster, simpler, and more effective dynamic analysis.
The Playbook
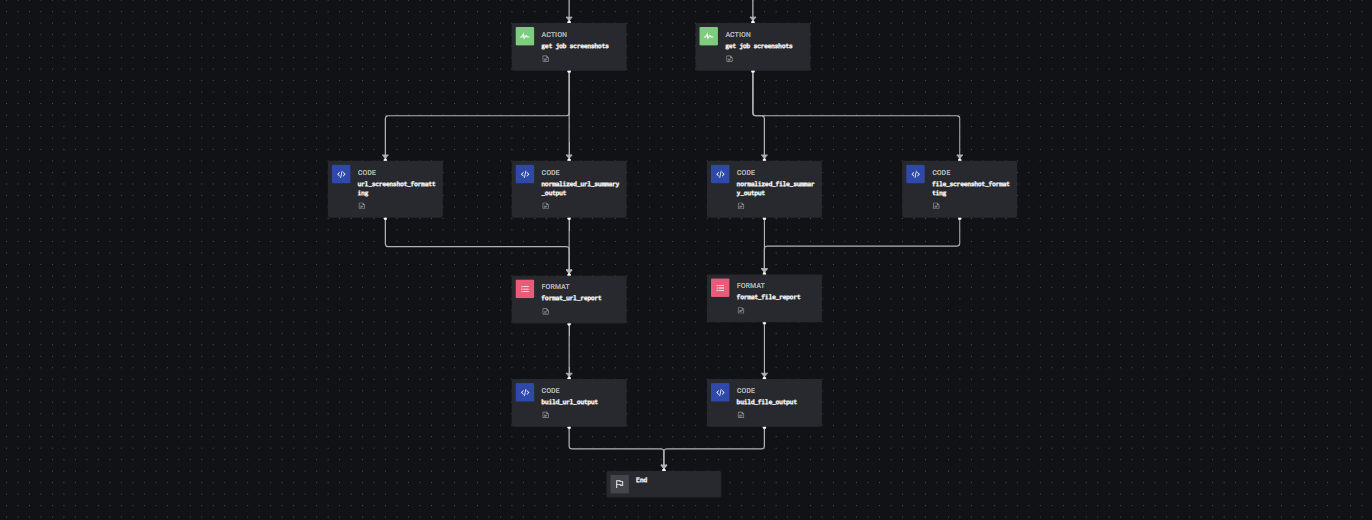
The Splunk Attack Analyzer Dynamic Analysis Playbook is an input playbook that accepts url link, domain or vault_id (hash) to be detonated using the Splunk Attacker (SAA) API connector. This process aligns with Mitre D3FEND’s Dynamic Analysis technique which involves executing or opening a file in a sandbox environment to see if the artifact in question is a malicious program or if it attempts to exploit another program.
Getting Started
- Before using the playbook itself, you will first want to make sure that you have the Splunk Attack Analyzer Connector for Splunk SOAR downloaded and configured. This will ensure you are able to run the playbook and get the results all without needing to pivot out of Splunk SOAR.
Using the Playbook
- From the artifacts tab, select the artifact(s)that you want to investigate.
- Select the “Run Playbook” option for the nav bar on the upper right.
- Search for Splunk_Attack_Analyzer_Dynamic_Analysis in the search bar and then select the playbook.
- Click the blue “Run Playbook” button in the bottom right of the window.
- Running the playbook will cause Splunk Attack Analyzer to perform detonation analysis on the selected URL and vault_id values of the selected artifact(s).
- Once this process is completed, Splunk Attack Analyzer generates a global report, a per observable sub-report and provides a normalized score which can be viewed in Splunk SOAR.
By using this playbook, you can easily tap into the combined potential of Splunk SOAR and Splunk Attack Analyzer for more effective dynamic analysis of threats to enable more informed response and remediation efforts.
Get more Splunk SOAR Playbooks
For the latest on Splunk SOAR playbooks, please visit research.splunk.com/playbooks. Also, check out our previous blog where we discussed how to implement the Cisco Umbrella DNS Denylisting playbook.
As always, we look forward to hearing about your experience with this month’s featured playbook as well as any other playbooks you’ve been using. We’ll be back next month with more playbooks and demos, but until then, get out there and get automating!
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.