Splunk SOAR Evolved: A Unified TDIR Approach to Automation
In a world where attackers are continually devising more sophisticated ways to breach enterprises, the value of automation has become critically important. To make matters worse, today's SOC is grappling with swivel chair movement across various security products, which sometimes includes a standalone automation product. SOCs are faced with the additional burden of integrating a standalone SOAR with their existing SIEM while fragmenting context across separate products, which, in reality, should always have been a unified platform.
Splunk SOAR solves all these problems by taking a unified threat detection, investigation, and response (TDIR) approach.This approach to consuming, sharing and building automation sets Splunk SOAR apart from many standalone automation products in the industry.
The Splunk SOAR product team is delivering a series of innovations to Splunk SOAR over the next few weeks across two key releases - Splunk SOAR 6.3.0 and 6.3.1. These capabilities constitute a significant evolution in how automation is consumed, shared and built across the SOC.
Redefining the Consumption Model: SIEM and SOAR is a match made in heaven
At .conf24, Splunk announced Splunk Enterprise Security (ES) 8.0 - a revolutionary step forward that natively integrates Splunk SOAR with Splunk Enterprise Security. This revolutionizes the consumption model for automation within a SOC, bringing automation to all tiers of analysts thereby democratizing the SOC. Delivering on the promise of the SOC of the Future, with SOAR Release 6.3.0, Splunk SOAR is now ready to integrate with Enterprise Security 8.0, which will be coming soon:*
- Splunk customers can now pair Splunk SOAR and Splunk ES within seconds without worrying about data formats or setting up different apps.
- Splunk SOAR playbooks and actions are now directly integrated within the Splunk Enterprise Security analyst queue. You can run playbooks and see the results of those playbooks without leaving the Splunk Enterprise Security interface.
- The Automation Rules feature in Splunk Enterprise Security lets you create automation rules to assign playbooks to specific detections so that playbooks run automatically when your selected detections produce findings. This not only provides better visibility and control over what playbooks are being triggered automatically, but also supports both generic enrichment and hyper-specific automation use cases.
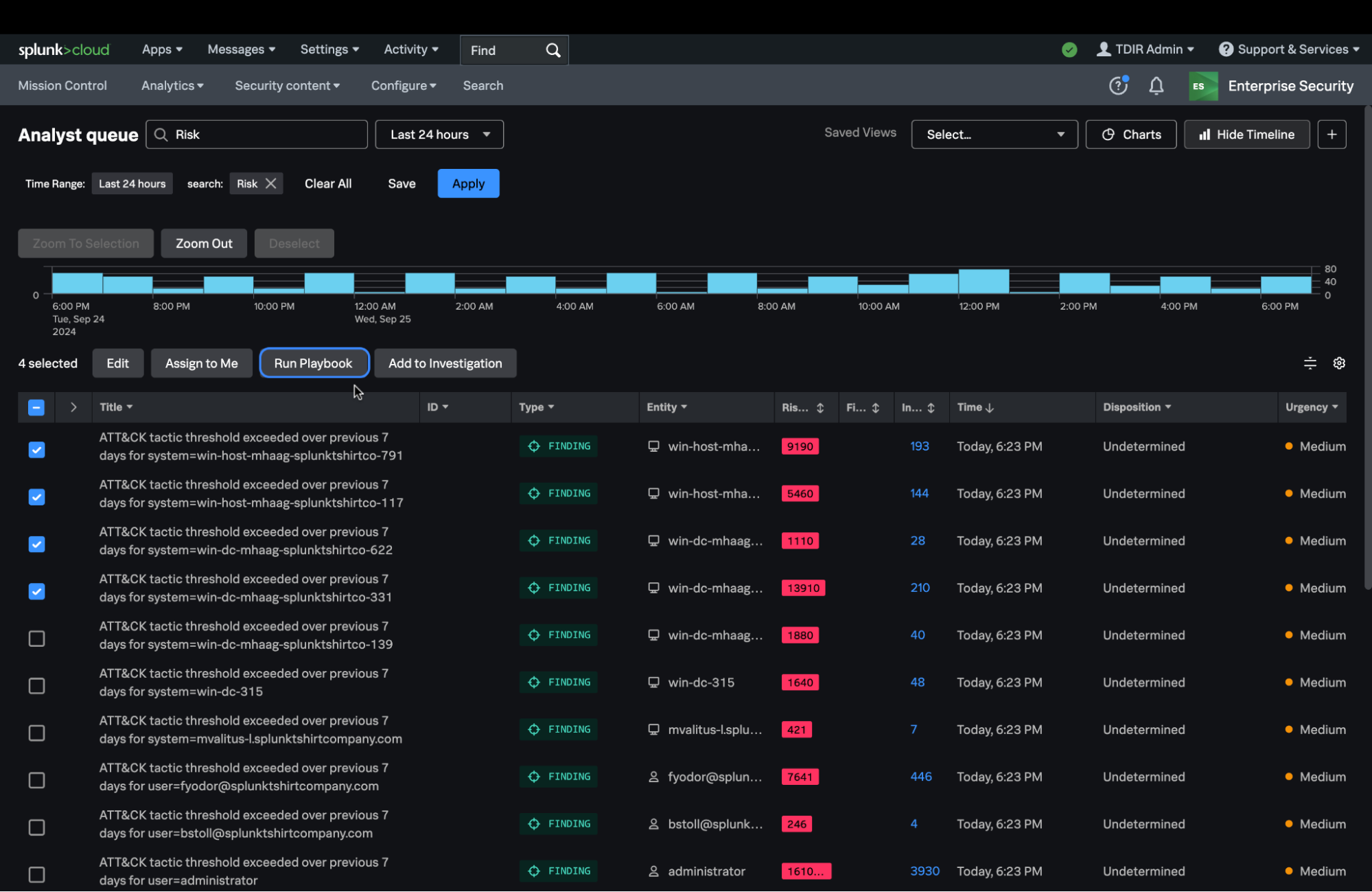
See below how Splunk Enterprise Security and Splunk SOAR seamlessly integrate to provide the best SecOps experience available today.
As shown below, the “Run Playbook” button is directly integrated into the analyst queue where an analyst can simply select findings and run automation on them with a single click of the button without ever navigating away from the ES user interface.

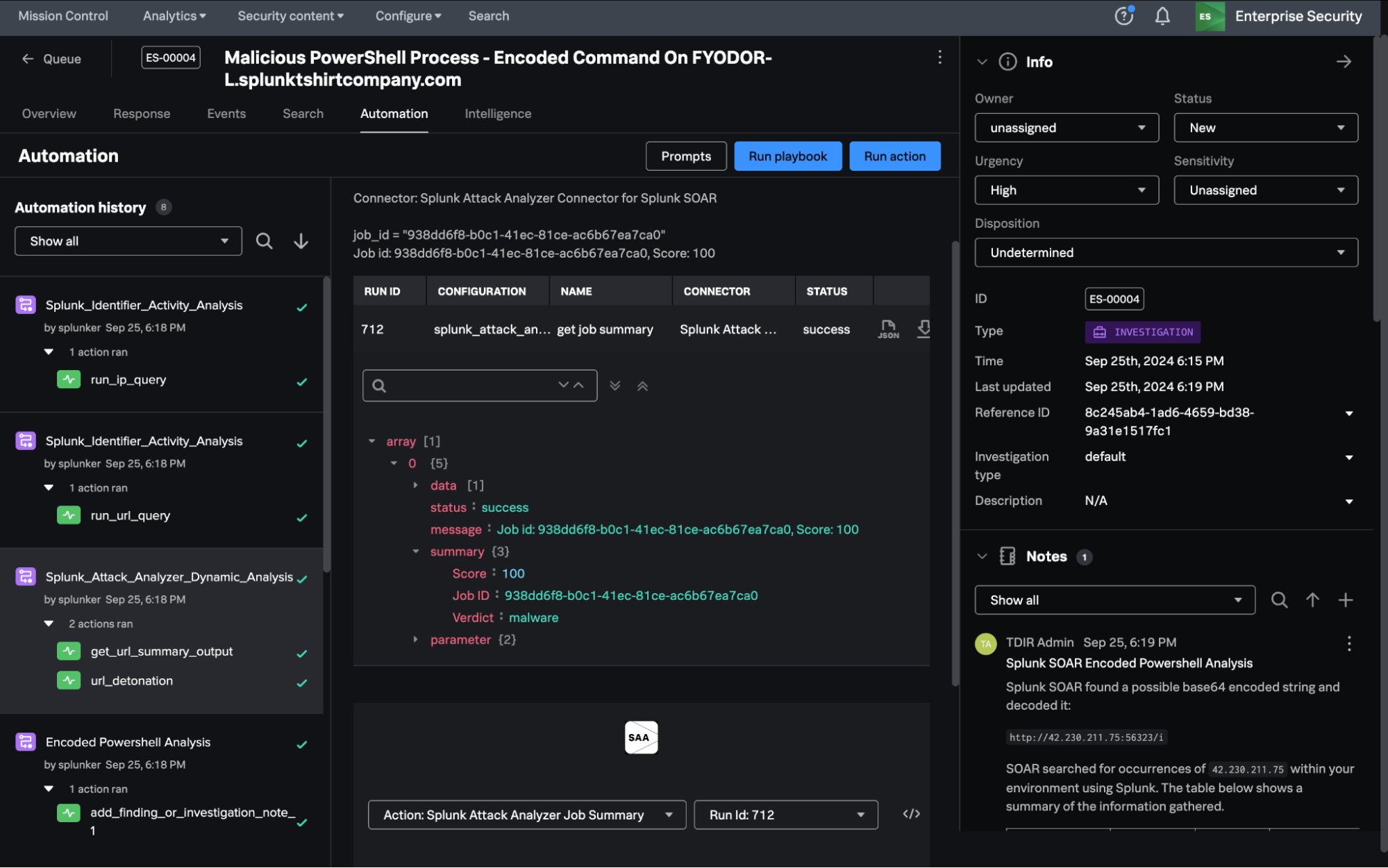
Below you see an open investigation with built-in Response Plans that provide prescriptive guidance to the analyst with suggestions on what playbooks can be run as part of this investigation. This allows the analysts to orchestrate playbooks from within an investigation in just a few clicks.
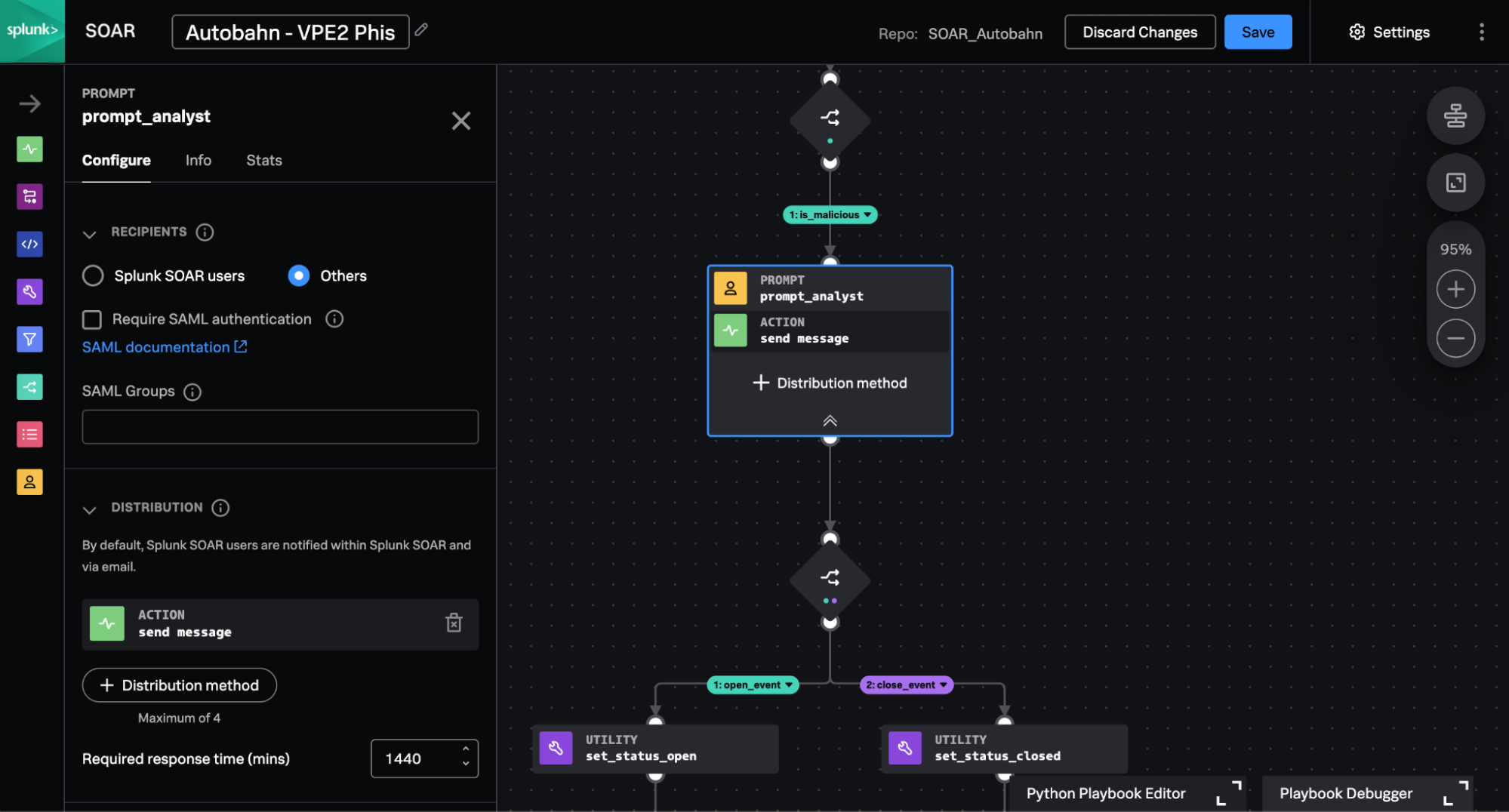
Collaborative SecOps that Go Beyond the SOC: Prompt-Driven Automation with human-in-the-loop
SecOps teams continue to face challenges in responding to threats efficiently due to fragmented and siloed teams. Effective communication with teams like IT, Network Security, HR, Legal, and end-users is crucial for informed security decisions. However, much of this communication occurs out-of-band, reducing SOC responsiveness and potentially alienating end-users. Streamlining these interactions is essential for a more agile and inclusive security strategy.
With Prompt-driven Automation, you can send real-time, secure prompts to teams outside the SOC—like IT and HR—to streamline response workflows and resolve security incidents cases faster.
But why would someone outside the SOC need to assist in a security investigation?
Consider a scenario: A potential phishing attempt is detected,triggering a playbook to analyze email. This analysis returns Indicators of Attacks (IOAs), such as malicious URLs and command-and-control IP addresses, which need to be blocked across the network security infrastructure managed by the network security team. Here, Prompt-driven automation sends an approval request to the network security team delivered via any supported SOAR applications. Once approved, the system automates the blocking of malicious URLs/IPs across the network security technologies such as firewalls or secure web gateways. The same prompt can also be sent to the end-user to verify if they entered their corporate credentials on the phishing website, which can further automate the reset of their username/password.
With the new Splunk SOAR release, these external prompts are sent directly to the end-user with simple, straightforward questions that they can respond to. Delivered through any ITOps, ChatOps or Ticketing SOAR applications, these prompts enable faster response time from end-users and other teams, allowing the SOC to respond to incidents more quickly, efficiently and effectively.
A Re-imagined Automation Building Experience: Guided Automation with Real Incident Data
Splunk SOAR has long offered a feature-rich, powerful visual playbook editor that enables customers to build highly sophisticated automations, including custom code. While we acknowledge the importance for this customizability, we’re also focused on making automation faster, easier and more accurate. It’s important to remember that automation isn’t a one-size fits all solution— low code options are only effective when the automation author has a clear understanding of both the data and the process flow.
With Guided Automation, coming soon in Splunk SOAR 6.3.1, playbook building is easier than ever. Guided automation unlocks a whole new visual experience overlaying real incident data atop the logical sequencing in a playbook. This superimposition not only drastically reduces the time to build automation but also improves accuracy as you can see output results in each individual playbook block based on real incident data.
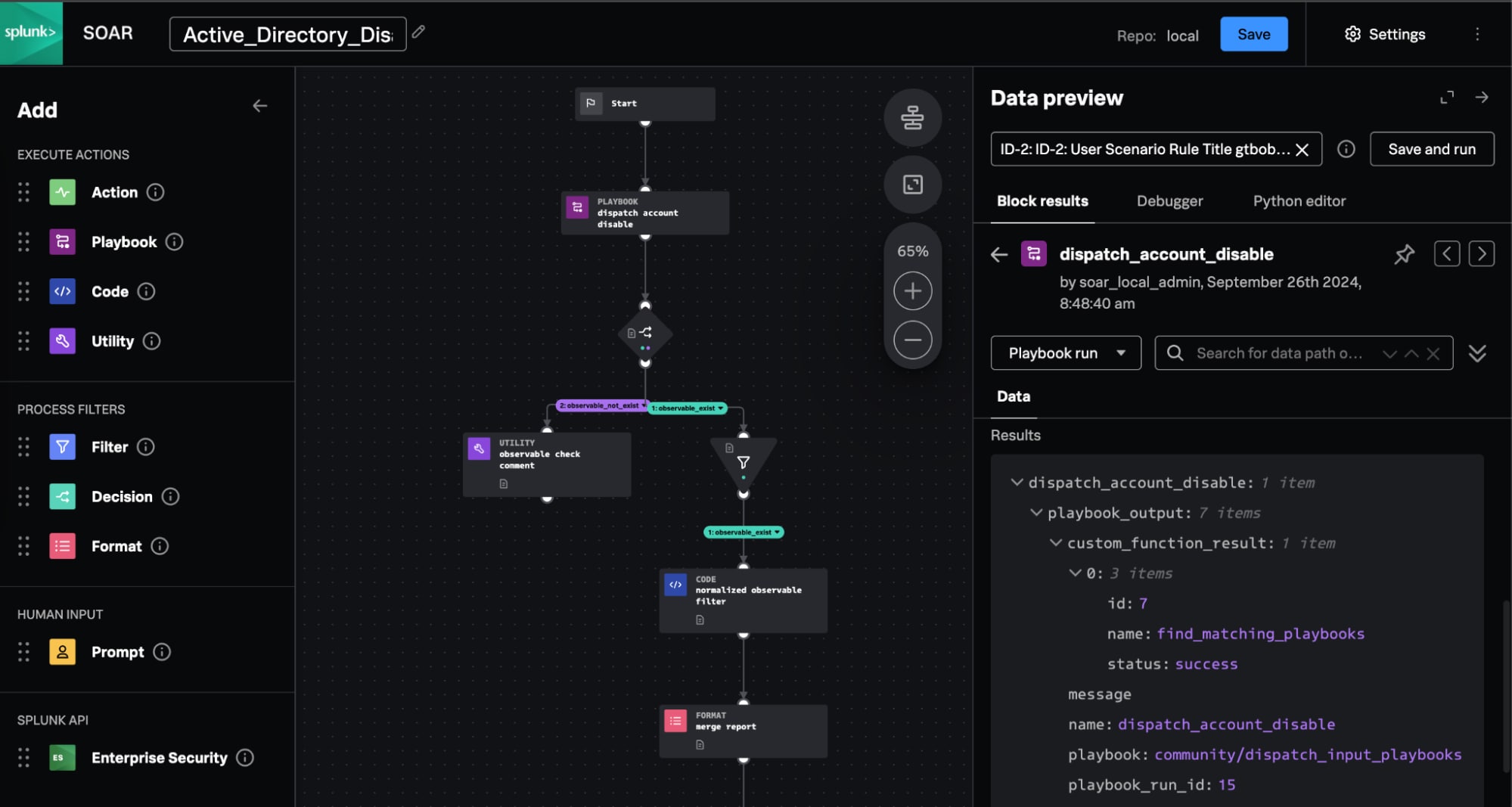
Now, security analysts and automation engineers can:
- Build automation playbooks more easily with intuitive at-a-glance data visualizations that show data in the context of specific security investigations
- Build faster with suggested actions to quickly add the right action blocks, filters, and prompts with a single click
- Build accurately by visualizing results rooted in real data from individual blocks
These enhancements ensure that automation playbooks are built and deployed rapidly to protect organizations from ever-evolving threats.
And there is more …
Quick and Easy UI Navigation: SOAR Wayfinder
Wayfinder, a powerful new feature that offers a streamlined discovery and navigation experience, allowing you to navigate effortlessly through the Splunk SOAR interface. With keyboard shortcuts, you can now instantly access key incidents, playbooks, and critical information for a smoother and efficient experience.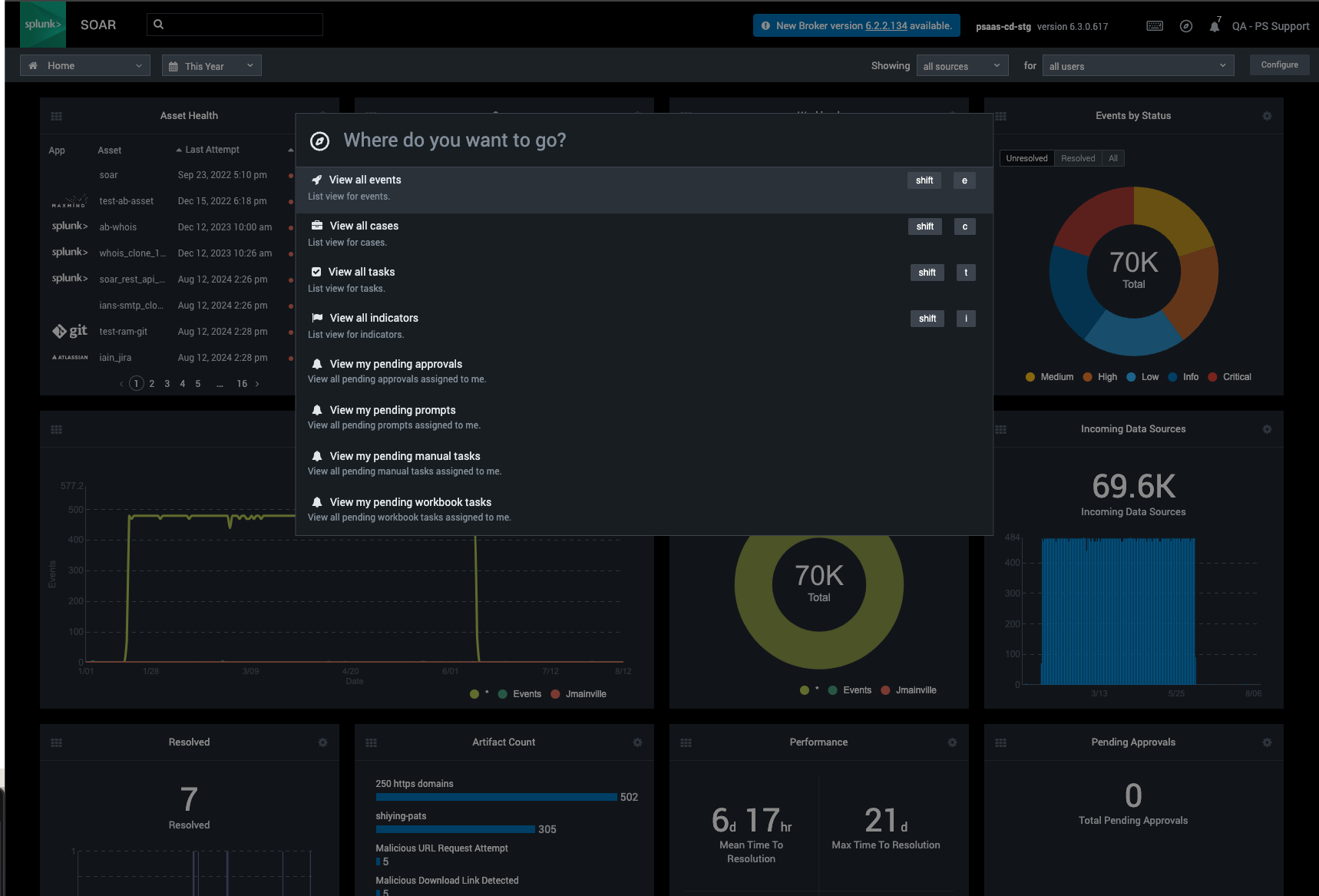
Wayfinder provides:
- Keyboard-driven navigation: Skip the menus and jump directly to what you need with the "." key
- Dynamic content discovery: Easily search for tasks, playbooks, or pages, with Wayfinder surfacing relevant results as you type
- Metadata-rich guidance: Results are accompanied with helpful metadata, ensuring you quickly reach the right destination
Wayfinder makes navigating Splunk SOAR faster, easier, and more intuitive than ever.
Splunk SOAR Achieves FedRAMP Moderate Certification
We’re excited to announce that Splunk SOAR is now FedRAMP Moderate certified. This highlights Splunk’s unwavering commitment to delivering secure, reliable solutions for the US Public Sector.
Splunk SOAR Evolved, Starting Today
A new way to SOAR is here, and it’s time to experience it firsthand. Dive into the powerful new features and capabilities of Splunk SOAR. Customers like Johnson Matthey are already seeing real value:
“Splunk SOAR facilitates communication,” says Nathan Lowey, cybersecurity engineer at Johnson Matthey. “With the click of a button, our analysts can seamlessly share case information with the OT team through IT service management, ensuring everything is protected in one unified system.”
Ready to transform your security automation? Take a guided product tour of Splunk SOAR, and start your journey today!
*Enterprise Security 8.0 general availability coming soon
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.