Logs Are For Campfires: Log Data, Big Data, and Splunk Asset & Risk Intelligence

Asset and Risk Intelligence
Purpose Built for Risk and Compliance
In part one of this series, we covered the similarities between big data and log data. And just like that, we have added the commensurate value to your log data that it truly deserves. Through this paradigm shift, you learned how to leverage your log data pre-emptively to gain advantages, not just as a reactionary post-mortem process that nobody looks forward to. In this context, Splunk Asset and Risk Intelligence (ARI) shines bright and delivers a top-tier experience. ARI takes all of your existing Splunk data to provide you with features like asset management, which your organization can use to avoid falling out of compliance, risk management before exploitation, vulnerability discovery, software tracking, and much more.
Some of our competitors would like to try categorizing Splunk as a database company, but that couldn’t be further from the truth. Splunk is a purpose-built platform that uses its log data management technology to complete various tasks. So yes, Splunk is a purpose-built platform, and no, Splunk is not a database company. Splunk Asset and Risk Intelligence provides a clear demonstration of this purpose-built functionality.
Asset Discovery
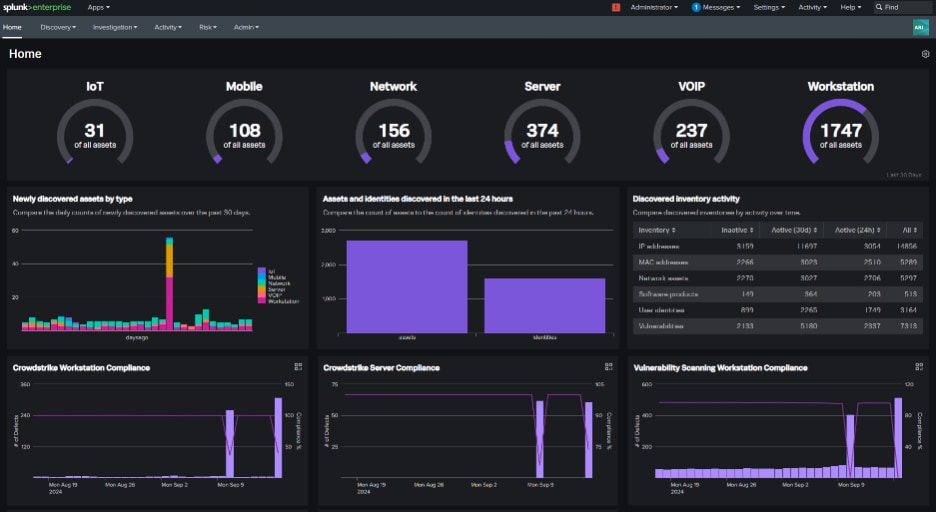
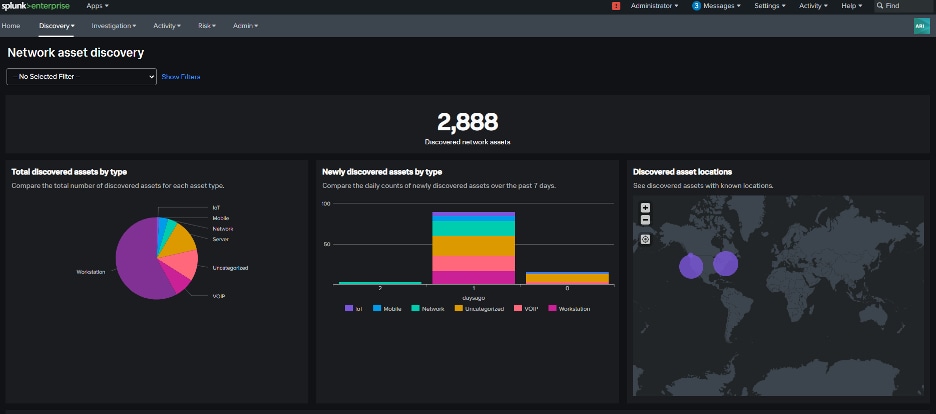
Splunk Asset and Risk Intelligence (ARI) consolidates data from various sources like network, endpoint, cloud, and scanning tools to create a unified and constantly updated inventory of assets and identities, eliminating outdated information for a more accurate and comprehensive view. By analyzing data from multiple sources, ARI identifies patterns, correlates assets reported by different systems, and provides a single reconciled view, ensuring a consistent asset inventory. Additionally, ARI offers a complete history of security events, attributing involved assets and tracking their changes and interactions over time, helping teams reduce risk exposure and identify potential blind spots.
ARI gives you a clear picture of everything connected to your network. It automatically gathers information about your devices, users, and cloud services, so you always have an up-to-date inventory. ARI consolidates this information into a single, up-to-date inventory, eliminating the need for manual tracking and outdated spreadsheets. This functionality helps you spot security risks like outdated software or suspicious user accounts and quickly respond to potential problems. With the asset discovery provided by ARI, you can avoid security threats and keep your systems safe.
Network Asset Investigation
Click here or on the image above for an ARI Guided Demo.
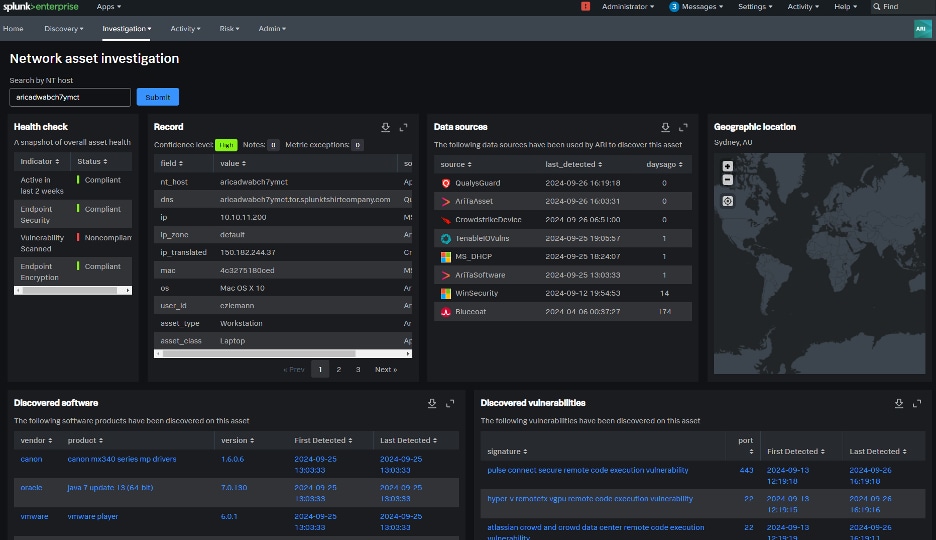
Splunk Asset and Risk Intelligence constructs asset inventories by consolidating data from diverse sources, including log files, network devices, cloud services, workstations, servers, and databases. The investigation dashboards offer a holistic context for investigations, providing visibility into critical asset data points such as health checks, geographical information, data sources, discovered vulnerabilities, and software. These vulnerabilities can be used to configure risk-scoring filters and rules that are also displayed in this dashboard, and we will discuss that further later.
The network asset investigation dashboard will show all the IP addresses associated with assets so you have a clear picture of the potential blast radius. This dashboard will also show you all of the users that have logged into the asset and the amount of time that these users have spent on this asset, allowing you to pivot easily to an IP address or user to further your investigation.
We’ve taken a look at how Splunk Asset and Risk Intelligence can provide a powerful solution for organizations seeking complete visibility and control over their assets. By automatically discovering, tracking, and analyzing all assets, ARI empowers security teams to proactively identify and mitigate risks, ensuring a fully optimized security posture to help reduce potential exposure to threats. With ARI, you can confidently navigate the complexities of modern IT and safeguard your valuable resources with complete context and visibility.
Stay tuned for part three in this series where we’ll dive into how ARI can help you discover potential vulnerabilities and provide your team with a power set of risk scoring filters and rules to help them stay on top of the potential threats that matter most.