Don’t Get a PaperCut: Analyzing CVE-2023-27350

Splunk is committed to using inclusive and unbiased language. This blog post might contain terminology that we no longer use. For more information on our updated terminology and our stance on biased language, please visit our blog post. We appreciate your understanding as we work towards making our community more inclusive for everyone.
PaperCut NG is a popular print management software that has 100 million users at over 70,000 organizations around the world. Recent discoveries have unveiled critical vulnerabilities in this widely-used software, specifically the CVE-2023-27350 authentication bypass vulnerability. This vulnerability, if exploited, allows an attacker to execute arbitrary code with elevated privileges on a target system. By understanding the mechanisms behind this critical vulnerability, defenders can better protect their systems and ensure a more secure printing environment. This blog walks through the process the Splunk Threat Research Team used to set up a PaperCut NG server, delves into the details of the CVE-2023-27350 proof of concept scripts and how to run them, how to set up Splunk logging, and dives into some fresh security content to identify adversaries.
What Happened?
Trend Micro reported to PaperCut NG that “... two vulnerabilities, CVE-2023-27350 and CVE-2023-27351, in Papercut, a print management software solution that is used by over 100 million users globally. Evidence was found that one of these two vulnerabilities, CVE-2023-27350, is being actively exploited by malicious actors for remote code execution (RCE).”
On April 18, 2023, a PaperCut customer noticed unusual events, indicating that servers without the latest patches might be vulnerable to exploitation through CVE-2023-27350. After conducting a thorough investigation, PaperCut found that the earliest signs of potentially related activity to CVE-2023-27350 can be traced back to April 14, 2023.
Which PaperCut Products Are Affected?
The following PaperCut versions and components are affected by CVE-2023-27350:
- PaperCut MF or PaperCut NG version 8.0 or later, on all OS platforms
- PaperCut MF or PaperCut NG Application Servers
- PaperCut MF or PaperCut NG Site Servers
Meanwhile, the following PaperCut versions and components are affected by CVE-2023-27351:
- PaperCut MF or PaperCut NG version 15.0 or later, on all OS platforms
- PaperCut MF or PaperCut NG ApplicationServer
Full details may be found on the PaperCut site here.
Next, let’s dive into setting up PaperCut on Windows.
Windows Installation
For our setup, we used Windows Server 2019 and installed the vulnerable version 17 from the PaperCut source: https://cdn.papercut.com/files/pcng/17.x/pcng-setup-17.4.4.exe

Double Click the installer to get started. The prompts are very simple.
Once install is complete, the URL is http://localhost:9191/app?service=page/Dashboard

For Windows, the Splunk Threat Research Team also wanted to capture any and all network traffic. We wrote this script a while back to install Suricata on Windows to provider granular network data. First install the TA on the Universal Forwarder. The script for Suricata on Windows is as follows: https://github.com/MHaggis/notes/blob/master/utilities/Install-Suricata.ps1
This is a two step process as the npcap software requires manual clicks:
1. Install the suricata TA to $splunkUF/etc/apps on a Windows System.
1a. Once extracted, modify the inputs.conf and add the following to collect the log data on Windows:
[monitor://C:\Program Files\Suricata\log\eve.json] host = suricata sourcetype = suricata index = network
Ensure the monitor path is windows specific to the eve.json file for Suricata
2. Run this script from disk, or copy and paste into PowerShell/PowerShell_ISE. Run.

2a. Mid install, it will present the explorer window in c:\temp; double click npcap and follow the prompts for installation.
Once complete, Suricata will start:

Now Suricata has started successfully. Suricata log data is now being collected and sent to Splunk.
In addition to the Windows Server having the TA, the Surcata TA will need to be installed on the Splunk Search Head to ensure proper data model usage.
In addition to network and endpoint logs, be sure to enable debug logging for PaperCut NG.
To enable debug logging, take the following steps inside the PaperCut NG web portal: head to Options -> Advanced ->
Select the check box for Enable Debug Mode.

The local C:\Program Files\PaperCut NG\server\logs\server.log will now populate with more data. It is probably best to not leave this on indefinitely however, for environments that cannot patch in a timely manner, these logs will be important for monitoring.
Modify inputs.conf to collect the server.log file similar to this:
[monitor://C:\Program Files\PaperCut NG\server\logs\server.log] host = papercutng sourcetype = papercutng index = win
Now that we have PaperCut NG running and logging all configured for network traffic and the debug log, we can dive into exploitation and see how these two scripts operate.
Exploitation
Horizon3
For our testing, we utilized the POC script provided by Horizon3 here.
Let’s break it down a bit to better understand what it does. Here is a summary of the HTTP requests sent to each URL path:

(For a larger resolution of this diagram visit this link)
1. `/app?service=page/SetupCompleted`: An HTTP GET request is sent to this path to initiate the session and obtain the initial cookies. The response should include the `JSESSIONID`.
2. `/app`: This path is used for several HTTP POST requests throughout the script:
a. The first POST request is sent to complete the initial setup and get a valid session with the target application. It submits a form with the required data and headers.
b. Further POST requests are sent to update settings (`print-and-device.script.enabled` and `print.script.sandboxed`) and execute the provided command on the target system.
3. `/app?service=page/PrinterList`: An HTTP GET request is sent to this path to navigate to the printer list page.
4. `/app?service=direct/1/PrinterList/selectPrinter&sp=l1001`: An HTTP GET request is sent to this path to select a printer with the ID `l1001`. This is a hard-coded printer ID, which may not work for every target system.
5. `/app?service=direct/1/PrinterDetails/printerOptionsTab.tab`: An HTTP GET request is sent to this path to navigate to the printer options tab for the selected printer.
These HTTP requests are used to obtain session information, update settings, and inject a custom print job hook script to execute the user-provided command on the target system.
In our testing, we ran the script twice as follows:
python3 CVE-2023-27350.py --url 'http://<remoteIP>:9191' --command 'cmd.exe /c powershell.exe calc.exe'
python3 CVE-2023-27350.py --url 'http://<remoteIP>:9191' --command 'powershell.exe -EncodedCommand "V3JpdGUtSG9zdCAnSGVsbG8gV29ybGQn"'

As shown in the screenshot, both tests were successful against our fresh PaperCut NG environment.
MetaSploit
The MetaSploit module found in this pull request https://github.com/rapid7/metasploit-framework/pull/17936/files, performs very similar steps:
1. /app?service=page/SetupCompleted
HTTP Method: GET
Purpose: Bypass authentication and create a session, while also obtaining the CSRF token for future requests.
2. /app?service=direct/1/ConfigEditor/quickFindForm
HTTP Method: POST
Purpose: Perform a quick find for a specific configuration option. This is used to set and check the values of 'print-and-device.script.enabled' and 'print.script.sandboxed' options.
3. /app?service=direct/1/ConfigEditor/$Form
HTTP Method: POST
Purpose: Update server configuration options. This is used to enable scripts (if needed) and disable sandboxing (if needed).
4. /app?service=direct/1/PrinterDetails/$PrinterDetailsScript.$Form
HTTP Method: POST
Purpose: Inject the payload into the printer script, which will be executed later.
5. /app?service=direct/1/PrinterList/selectPrinter
HTTP Method: GET
Purpose: Select the printer (Template Printer) for modification. This loads it into the Tapestry session to be modified with the payload.
Once the module is loaded in MetaSploit, we can check out the info and get it set up for exploitation.
Info from within MetaSploit:

And the options:

Now that things are set, we can run exploit and voila - meterpreter is here:

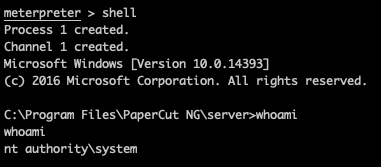
From meterpreter, run shell and whoami:
To expand a bit on the similarities between the two scripts, the table below showcases the URIs next to each other:
| MetaSploit | Horizon3.ai |
|---|---|
| /app | /app |
| /app?service=page/SetupCompleted | /app?service=page/SetupCompleted |
| /app?service=page/PrinterList | /app?service=page/PrinterList |
| /app?service=direct/1/PrinterList/selectPrinter | /app?service=direct/1/PrinterList/selectPrinter |
| /app?service=direct/1/PrinterDetails/printerOptionsTab.tab | NA |
| NA | /app?service=direct/1/PrinterList/selectPrinter&sp=l1001 |
Keep in mind that the URIs used in both scripts are very similar since they target the same PaperCut application. However, the MetaSploit script has an additional URI for `PrinterDetails/printerOptionsTab.tab`, and the Horizon3.ai script has an extra URI parameter in the `PrinterList/selectPrinter` endpoint.
We built a lab, got logging and successfully exploited PaperCut NG. Now we can dive into these logs and begin generating some security content.
Security Content
Windows PaperCut NG Spawn Shell
The following analytic identifies a Windows shell - Cmd.exe or PowerShell, or java.exe spawning from pc-app.exe.
| tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.parent_process_name=pc-app.exe `process_cmd` OR `process_powershell` OR Processes.process_name=java.exe by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.original_file_name Processes.process Processes.process_id Processes.parent_process_id

For MetaSploit, a java payload is the default; therefore once the application is exploited, pc-app.exe will spawn java.exe

Once meterpreter was running on the attacker side, we ran `execute -f whoami.exe` and the result spawned cmd.exe from java.exe

From MetaSploit:

Note the user context is NT AUTHORITY\SYSTEM.
PaperCut NG Remote Web Access Attempt
This analytic utilizes the Web data model to identify the common URI paths abused. We ignore the private IP space and focus solely on a public IP address enumerating the application.
| tstats count from datamodel=Web where Web.url IN ("/app?service=page/SetupCompleted", "/app", "/app?service=page/PrinterList", "/app?service=direct/1/PrinterList/selectPrinter&sp=*", "/app?service=direct/1/PrinterDetails/printerOptionsTab.tab") NOT (src IN ("10.*.*.*","172.16.*.*", "192.168.*.*", "169.254.*.*", "127.*.*.*", "fc00::*", "fd00::*", "fe80::*")) by Web.http_user_agent Web.http_method, Web.url,Web.url_length Web.src, Web.dest Web.dest_port sourcetype | `drop_dm_object_name("Web")` | `security_content_ctime(firstTime)`
| `security_content_ctime(lastTime)`

This screenshot is what it looks like when the MetaSploit module is used. Notice the difference in user agents.

An additional artifact using MetaSploit is the src IP, our PaperCut NG server, contacting the C2 for the java payload:

PaperCut NG Suspicious Behavior Debug Log
This particular log comes directly from the PaperCut NG Application and must be enabled. It is strongly recommended to not leave it on indefinitely However, for testing purposes or until patching may occur, it may be worth it. This analytic takes a different approach by looking for public IP addresses, admin user and one of the URI’s identified up above in the debug log.
`papercutng` (loginType=Admin OR userName=admin) | eval uri_match=if(match(_raw, "(?i)(\/app\?service=page\/SetupCompleted|\/app|\/app\?service=page\/PrinterList|\/app\?service=direct\/1\/PrinterList\/selectPrinter&sp=l1001|\/app\?service=direct\/1\/PrinterDetails\/printerOptionsTab\.tab)"), "URI matches", null()) | eval ip_match=if(match(_raw, "(?i)((25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))") AND NOT match(_raw, "(?i)(10\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))|(172\.(1[6-9]|2[0-9]|3[0-1])\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))|(192\.168\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))"), "IP matches", null()) | where (isnotnull(uri_match) OR isnotnull(ip_match)) | stats sparkline, count, values(uri_match) AS uri_match, values(ip_match) AS ip_match latest(_raw) BY host, index, sourcetype
 This screenshot shows MetaSploit usage against the application and how it looks very similar to the Horizon3.ai POC script.
This screenshot shows MetaSploit usage against the application and how it looks very similar to the Horizon3.ai POC script.

The discovery of the CVE-2023-27350 vulnerability in PaperCut NG highlights the importance of staying vigilant in the ever-evolving world of cybersecurity. By understanding the mechanisms behind this critical vulnerability, defenders can better protect their systems. It is crucial for organizations using PaperCut NG to apply the necessary patches and closely monitor their environment for any suspicious activities. By following the steps outlined in this blog, understanding proof of concept scripts, and implementing robust logging and Splunk security content, organizations can effectively detect and respond to threats associated with this vulnerability.
Learn More
You can find the analytic story for PaperCut here and additional content about security analytic stories on GitHub and in Splunkbase. Splunk Security Essentials also has all these detections now available via push update.
For a full list of security content, check out the release notes on Splunk Docs.
Why Should You Care?
The CVE-2023-27350 vulnerability in the PaperCut software exposes organizations that employ this popular print management software to the public internet. This vulnerability allows a potential attacker to bypass authentication and execute arbitrary code with elevated privileges on a target system.
Given that PaperCut software is widely used by organizations across the globe, this vulnerability has the potential to expose vast amounts of sensitive information and business-critical data, making it a lucrative target for malicious actors.
The analysis in this blog offers a deep dive into the nature of the vulnerability, its exploitation methods, and how to monitor and protect your systems from potential exploits. By properly setting up your PaperCut software and Splunk logging, you can effectively manage and reduce your organization's risk exposure.
Feedback
Any feedback or requests? Feel free to put in an issue on GitHub and we’ll follow up. Alternatively, join us on the Slack channel #security-research. Follow these instructions if you need an invitation to our Splunk user groups on Slack.
Contributors
We would like to thank Michael Haag for authoring this post and the entire Splunk Threat Research Team for their contributions: Teoderick Contreras, Mauricio Velazco, Lou Stella, Bhavin Patel, Rod Soto, Eric McGinnis, and Patrick Bareiss.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




