Detect Faster, Rapidly Scope an Incident, and Streamline Security Workflows with Splunk Enterprise Security 7.1

 SOC teams continue to struggle with slow detection times, lack of context around security incidents, and inefficient implementation and execution of incident response workflows. The latest release of Splunk Enterprise Security directly addresses these challenges.
SOC teams continue to struggle with slow detection times, lack of context around security incidents, and inefficient implementation and execution of incident response workflows. The latest release of Splunk Enterprise Security directly addresses these challenges.
Splunk Enterprise Security 7.1 is now available! In this release, we provide three new capabilities to help security teams detect suspicious behavior in real-time, quickly discover the scope of an incident to respond accurately, and improve security workflow efficiencies using embedded frameworks. Let’s get into it!
Detect Suspicious Behavior in Real Time
Attacks are faster and more sophisticated than ever. That’s why Splunk continues to develop capabilities within Splunk Enterprise Security to improve and support the SOC’s ability to detect suspicious and malicious behavior.
A new feature called cloud-based streaming analytics integrates with Splunk’s risk-based alerting (RBA) framework to deliver enhanced analytics for improved situational awareness and response time to suspicious behavior. This feature brings scalable real-time streaming analytics for a broader range of advanced security detections and focuses on addressing common use cases including insider threat, credential access and compromise, lateral movement, and living off the land attacks. Cloud-based streaming analytics will support ‘Windows Event Log’ XML source-types, and provide Splunk Enterprise Security users with an introductory set of 50 real-time streaming detections focused on insider threat use cases. This augments our traditional search-based correlation to scale security monitoring, and drive down detection time, firing off alerts in seconds versus minutes.
Splunk Enterprise Security 7.1 users get:
- Real-time detections for common insider threat use cases
- Seamless integration with content management and the RBA framework in Splunk Enterprise Security, proven to increase visibility, drive true-positive detection, and reduce alert fatigue
- Scalable analytics to analyze data as it is sent by offloading to stream analytics, complementing traditional scheduled searches with more valuable security content delivered directly from Splunk
- A simple to deploy, cloud-native, and low maintenance feature that runs as a complementary analytics engine for Splunk Enterprise Security Cloud
Quickly Discover the Scope of an Incident to Respond with Accuracy
As security practitioners, we often cannot see the forest for the trees. It’s sometimes easier to see the details of an incident, but not be immediately able to decipher the bigger picture. When investigating a security incident, we have to quickly be able to see the situation from both lenses simultaneously.
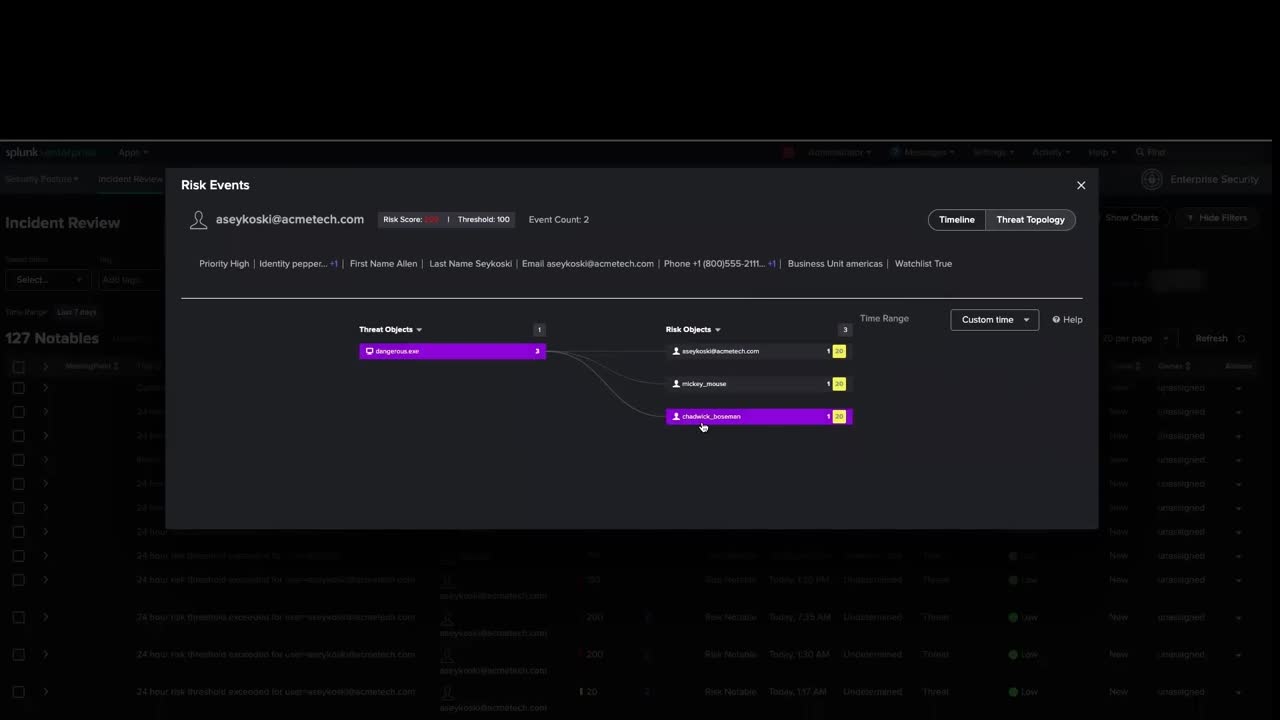
This is why we developed a feature called threat topology visualization. Using this feature, security analysts can quickly discover relationships between Splunk Enterprise Security assets and identities (a.k.a. users and machines) and threat objects (a.k.a. malicious executables, IP addresses, and file hashes). Analysts can pivot between affected assets and users in the investigation to see the scope of the incident beyond the infected user, providing improved situational awareness and an expanded viewpoint. This also allows the analyst to quickly determine the severity level of an incident, and identify additional impacted subjects without having to write a single line of code. And perhaps most importantly, it saves time and increases productivity, further reducing mean time to response (MTTR) for the SOC.
In summary, threat topology visualization enables Splunk Enterprise Security 7.1 users to:
- Get a more comprehensive view into security incidents
- Quickly determine the severity level of an incident
- Achieve faster time to initiate an investigation with point-and-click exploration without writing new queries
- Identify additional impacted subjects of an investigation without writing a single line of code of query language
See threat topology visualization in action in this demonstration video.
Improve Security Workflow Efficiencies with Embedded Frameworks
Stick to the plan. This has never been more important than in security. To investigate and respond to incidents quickly, efficiently and comprehensively, SOC analysts should adhere to tried and true industry frameworks, and embed those workflows into the operational fabric of their SOC.
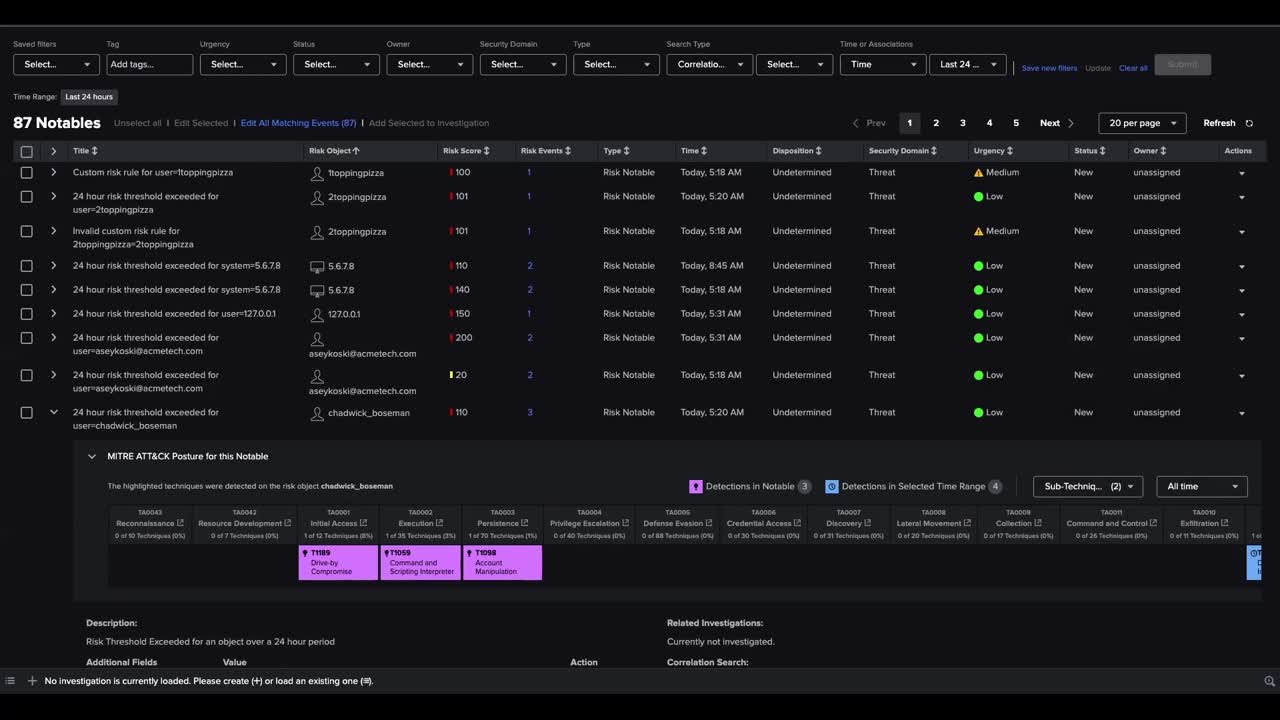
Using our new MITRE ATT&CK® visualization capability, security analysts can quickly build situational awareness around an incident in the context of the MITRE ATT&CK Matrix. Security analysts can leverage and visualize MITRE ATT&CK annotations in Splunk Enterprise Security risk events and get a comprehensive picture of how the asset or identity has been impacted by various tactics and techniques. From there, analysts can easily drill down into MITRE ATT&CK reference material to gather additional context and plan the response. This will allow analysts to operationalize the MITRE ATT&CK Framework as they respond to notable events, and speed their understanding of the attack lifecycle as they defend the organization's assets.
In summary, MITRE ATT&CK visualization enables Splunk Enterprise Security 7.1 users to:
- Visualize MITRE ATT&CK tactics and techniques in risk notable events
- Operationalize the MITRE ATT&CK framework when responding to notable events
- Improve productivity and response time while defending the organization's assets
- Quickly identify the tactics and techniques observed in a notable event, and historically in older notable events for a given user or machine
See MITRE ATT&CK visualization in action in this demonstration video.
One More Thing
Splunk Enterprise Security 7.1 also delivers features that increase deployment flexibility, improve the user experience, and increase the fidelity of risk-based alerting.
- Advances in Risk-Based Alerting: Enterprise Security continues to innovate our risk-based alerting feature set with new enhancements to help customers prioritize threats, including:
- New Risk Object Normalization - Risk objects and their associated risk scores are now normalized to a single score if they match an asset or identity.
- Additional Context in Risk Event Timeline - The risk event timeline now displays the “risk message” by default, giving analysts additional context when triaging risk notables.
- New Entity Zone Support - RBA adds support for entity zones for environments that contain conflicting IP address ranges. With this enhancement, assets in separate entity zones maintain separate risk scores as well.
- Risk Timeline by Original Event Time - The risk event timeline now displays risk events based on the original time of the events contained in the risk event, providing a more accurate view of an incident.
- Widened Configuration Panels: You asked, we answered. Splunk Enterprise Security 7.1 delivers a widened correlation search editor to make it easy to view and customize Splunk security detections. Additionally you will find that other commonly used configuration panels have also been widened for easier workflow and better screen real-estate.
- Splunk Dashboard Studio: Upgrading Splunk Enterprise Security dashboards from simple XML to Splunk Dashboard Studio helps to improve performance and consistency so that you can gather better insights from your data visualizations. For more information, see Compare classic Splunk Dashboards (Simple XML) with Splunk Dashboard Studio
Upgrade Today!
There you have it. Splunk Enterprise Security 7.1 updates are available today in both cloud and on-prem environments.
To learn more about Splunk Enterprise Security 7.1, check out a few demos, release notes, and the Splunk Enterprise Security website.
Happy Splunking!
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




