Shift Left Security Today: Adoption Trends & How To Shift Security Left

For a long time, cybersecurity and development were two distinct aspects of software programming. As organizations started to leverage software and technology, the speed and quality of development became more important than ever. Organizations no longer had time after development was complete to address security vulnerabilities.
Catching vulnerabilities too late opens companies up to unnecessary risk and can be costly to fix. In fact, security is a problem for many companies: 79% pushed a vulnerable code to production, even though they rated their application security as good.
Many organizations have started incorporating security practices from the beginning of development — known as shifting left. A shift left approach to security allows companies to:
- Keep their software secure during development.
- Catch issues before they become problems.
- Provide a better-quality product.
In this article, we will cover what you need to know about shift left security, including what it is, why it is critical, and best practices for implementing a shift left approach for your development team.
What is shift left security?
Shift left security is the practice of implementing security measures over the entire development cycle rather than waiting until it is nearly complete. It enables teams to uncover vulnerabilities, defects, and bugs earlier in the development process to improve systems' speed and quality.
The software development lifecycle (SDLC) can vary in formal steps but it generally covers these activities:
- Defining requirements
- Designing
- Development and building
- Testing
- Deployment and maintenance
Why is it called “shift left”? Because we want to shift the focus on security to earlier in the SDLC. Developers are focused on the left side (from left to right) of this cycle, so moving anything towards their domain requires shifting left.
(Related reading: Secure by Design emphasizes embedding security measures early in the dev phase.)
Security tests to incorporate in the SDLC
Organizations shift security left with a series of tests throughout the development process. That way, they can catch and amend any weaknesses before moving on to the next stage. Let’s take a brief look at these tests.
SCA: Software composition analysis
The first test starts on the developer’s desktop. Software composition analysis (SCA) tests the external libraries and components and answers critical questions about the integrity of the software.
Used effectively, it catches potential security concerns and bugs before the developer even writes code.
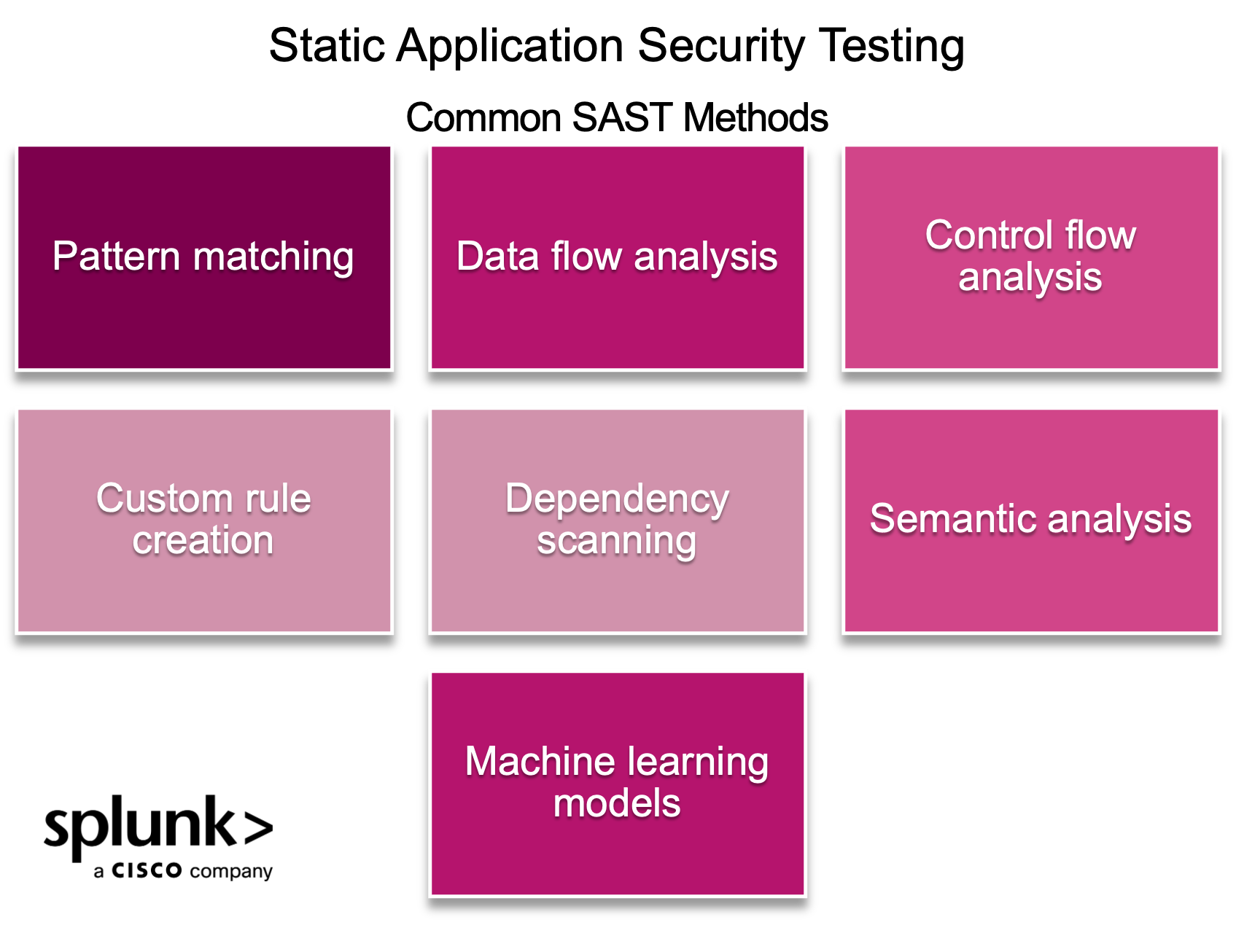
SAST: Static application security testing
Once the developer starts writing the coding and completes a function, the second test is static application security testing (SAST). Using “white box” testing, SAST ensures the code is secure. For example, it might show things like:
- The developers inputted verification.
- The libraries used are up to date and patched.
This testing is completed after each line of code. Automation has made this test faster and easier than ever. In fact, it can even catch issues while the developer is typing.
Infrastructure as Code security inspection
After passing the two tests, the developer now has a version and created a feature ready for the test environment. The third test, Infrastructure as Code (IAC) security inspection, ensures that the test environment is not vulnerable to security lapses. It checks for two primary things:
- Open ports or buckets
- Secure images (since images online could be embedded with a virus)
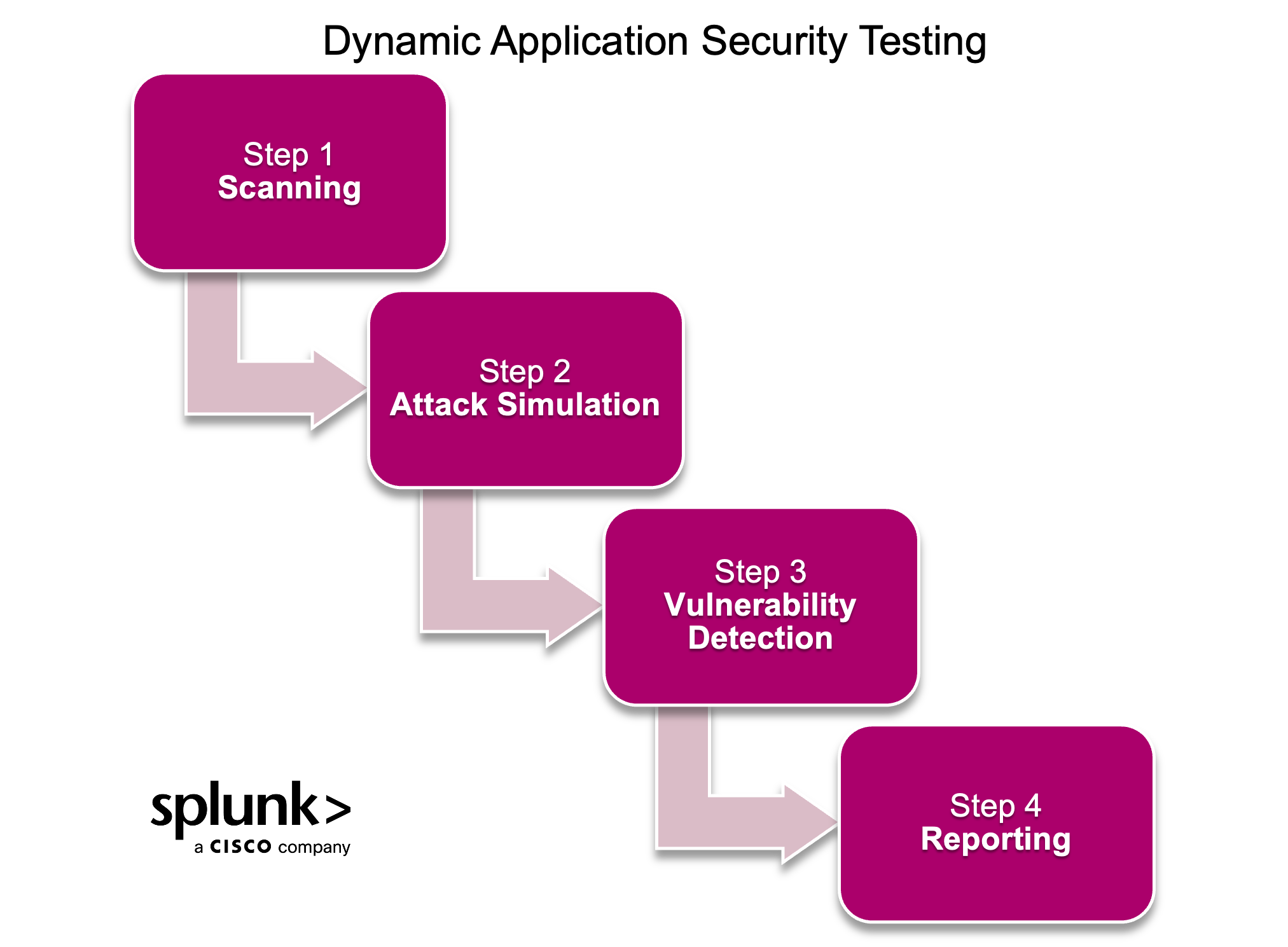
DAST: Dynamic application security testing
Once the code is in the test environment, DAST provides the next layer of security. It runs the code and tries manipulating it for “black box” testing. By inputting different decodings, large-size inputs, and stress loading, DAST can identify hard-to-find problems before it becomes public.
Embedded secrets
The last test runs the code to check for secret keys or application secrets — like API keys, database credentials, and security certificates — before it moves on to production. Developers may accidentally leave important authentication keys embedded in their code. This can lead to problems: over 5 million secrets were detected in public repositories in 2021, up 20% from the previous year.
These tools have become faster and easier for developers to use with the rise of automation. By automatically checking for weaknesses, developers are no longer forced to manually check code.
(Read our software testing introduction.)
Why shift left security matters
Catching problems early makes them much easier to fix for all involved:
- Developers don’t have to apply workarounds to flawed implementations.
- Operations/DevOps don’t have to maintain a flawed application in production.
Discovering issues during production also means that developers can get to the root cause of the problem instead of continuously putting Band-Aids on the issue. It means that they can modify the application architecture of underlying components and enhance the overall application.
Shift left security adoption trends today
Shift left security is often seen as a guidance concept with practical use cases. You can find several flavors of shift left security guidelines for SecOps and DevSecOps frameworks. Two key ingredients common in these frameworks are:
- (Intelligent) automation
- A platform for collaboration between Devs and InfoSec teams
This platform includes the infrastructure, tooling stack, knowledge, and seamless integration of services across the domains of development and information security. This is required because security functions must appear early during the SDLC and because the roles of Devs and InfoSec overlap.
So, what happens when you try to implement an exhaustive collaborative strategy, infrastructure, and tooling to enable these capabilities?
Shift left security is different from the traditional approach to security, which assigns isolated security responsibilities to experts before a completed feature build is ready for testing prior to shipping to production. At that moment, a security bug may be hard to discover, too difficult to fix or may be ignored as a strategic business decision.
Without a DevOps-led or Agile framework and automation capabilities, shifting security responsibilities to the left are challenging.
Challenges with shifting security left
A study among 250 enterprises with more than $1 billion in revenue reveals some of the key obstacles to implementation of frameworks for shift left security:
- Technical challenges
- High cost of implementation, resistance to change, and other organizational barriers
- Lack of time to complete such a change project effectively
- Lack of education around new shift left security best practices and lack of skills
- · Lack of automation and tooling
Yet, these organizations are also embracing the movement. The same report finds that more than half of these organizations are adopting DevSecOps best practices including shift left security to:
- Improve product quality (54%)
- Accelerate release cycles (30%)
By far the biggest challenge seen, with 73% agreeing, include lack of automation and manual processes for security and compliance.
A 2024 survey of over 5,000 DevSecOps professionals found that intelligent automation is considered as a top priority to realize these goals. The use of AI has increased from 64% in 2023 to 78% in 2024 — automation jumped from 6th to 4th.
AI and shift left security
Today, nearly three-quarters of professionals want to consolidate their toolchain using AI. This will directly impact the collaborative shift-left security responsibilities of otherwise isolated teams in Dev and InfoSec.
For example, embedding automated security controls and testing capabilities into the CI/CD pipeline will be a key trend for shift-left security in coming years. Other capabilities include self-healing systems without manual intervention by analyzing security performance and gaps early in the SDLC pipeline.
And the investment trends are aligned with these observations. In fact, four out of five CIOs are increasing cybersecurity budgets in their IT spending, which increased by 8% in 2024 to reach $5.1 trillion globally. These trends come down to two essentials:
- The rapid escalation of security threats
- The increasingly stringent legal mandates for data privacy and security.
(Related reading: the latest IT spending trends.)
Best practices for shifting security left
A shift left strategy requires organizations to rethink their approach to security and impacts the very company culture. Here are some best practices to ensure your strategy is successful:
Identify your goals
Defining clear security policies will help pave the way and shape shift left security. Creating these policies will consistently set boundaries before beginning work, delivering critical information for all development processes.
A shift left approach is a change at the cultural level of an organization. Each tool or process added to the development cycle will have broader implications for all stakeholders. Every team leader must make crucial decisions together to ensure changes are established.
Understand how software is created
For many organizations, the most challenging of the shift left approach is understanding how and where your software creates organization. The complexity here depends mainly on the size of your organization. If development is outsourced to vendors, it might require contract reviews and more work. Enterprises that have not organized this process will likely spend months unpacking the process.
Step back and get an organizational-wide look to document the flow of the software. Larger companies should start at a big-picture level and then move into individual business units. From there, they’ll likely find that each unit has separate software development tools and processes.
Critical items to include in your research include:
- The people developing and managing code
- How it moves from development laptops to production (the CI/CD pipeline)
- The technology that devs use during the process
Train your development teams
While your development team may know how to code, it’s critical to ensure they know how to do so securely. You’ll also have to provide the right tools and environments to maintain that security. In fact, 70% of developers said they were expected to write code securely, but just 25% said their organization had “good” security practices.
Part of the process of shifting left your security is ensuring the ones who create your coding know what it takes to do it securely. Create objective measurements to see where their skills are and identify a plan to improve over time.
Fix security when building the code
The faster developers can implement fixes, the quicker and easier the process will be. Strive to introduce security as the development process occurs and give feedback as quickly as possible.
Shift security left for the future of development
As organizations look to produce high-quality software quickly, shift left security becomes essential. By enabling developers to catch problems, bugs, and potential security issues in advance, it becomes faster and easier to address them.
While shift left security has become a cornerstone DevSecOps strategy, it must be done responsibly to be effective. Implementing the right tools and empowering developers with the information they need will ensure a seamless and automated process. It will help them work faster and avoid the frustrations of the shift right approach.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.





