Security Compliance: A Complete Introduction

With the rise of sophisticated cyber threats and stringent regulations, organizations must protect sensitive data and adhere to established standards. Compliance is a helpful “tool” for achieving this.
Failing to meet security requirements can expose businesses to security breaches, legal penalties, and loss of customer trust. By integrating compliance into their security strategy, organizations create a strong foundation for resilience and long-term success.
This article will explore key roles within security compliance, the importance of this tool, how to achieve cybersecurity compliance, and much more.
What is security compliance?
Cybersecurity compliance refers to aligning with laws, industry guidelines, and best practices to mitigate risks, safeguard assets, and foster trust.
Non-compliance can lead to severe consequences. For example:
- Hefty fines
- Reputational damage
- Operational disruptions
By prioritizing compliance, businesses protect themselves and gain a competitive edge in a security-conscious market.
Security compliance also helps organizations streamline their security frameworks, making it easier to identify and address vulnerabilities proactively. Regular audits, employee training, and robust security policies play a crucial role in maintaining compliance and adapting to evolving threats.
Key players in cybersecurity compliance
Employees at every level must adhere to security protocols, understand their role in maintaining compliance, and contribute to a culture of cybersecurity. From leadership setting the tone to staff avoiding phishing scams, every action matters.
Typically, these roles lead the charge:
Achieving compliance, however, requires collective effort.
Security vs. compliance
Though closely related, security and compliance are distinct concepts that complement one another.
- Security refers to organizations' strategies and measures to protect their systems, data, and networks from threats
- Compliance ensures adherence to external regulations and internal standards
Cybersecurity is proactive, focusing on preventing breaches through technology, policies, and processes. It’s the management of risks through the implementation of controls.
Compliance is regulatory, ensuring organizations meet legal and industry-specific requirements. Think of measuring controls against a standard.
The interplay
Compliance provides a foundational framework, but security goes beyond the minimum requirements to address evolving threats. For example, GDPR mandates encryption for data protection—a compliance measure. However, a robust security strategy would include advanced threat detection and rapid response systems to prevent breaches.
A nice way to look at this is: Being compliant with regulations doesn’t necessarily make you secure, but it's hard to be secure without some level of compliance program in place.
(Related reading: regulatory compliance.)
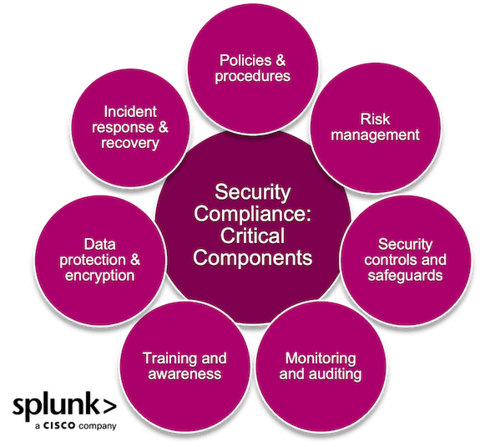
Components of security compliance
Achieving cybersecurity compliance involves addressing several critical components. Here are the key areas organizations should focus on:
Policies and procedures
These documents set the foundation for compliance. Clear policies outline how sensitive data should be handled, stored, and accessed. For instance, GDPR requires organizations to establish data processing and retention policies, ensuring transparency and accountability.
Risk management
Effective risk management identifies weaknesses and implements controls to mitigate them. For example, financial institutions prioritize protecting customer data from fraud through encryption and multi-factor authentication.
Security controls and safeguards
These security controls include firewalls, intrusion detection systems, and endpoint protection. For instance, PCI DSS mandates the encryption of payment card information to prevent unauthorized access.
(Related reading: endpoint security.)
Monitoring and auditing
Continuous monitoring ensures systems remain compliant, while regular audits verify adherence to standards. ISO 27001, for example, requires periodic reviews to identify security gaps.
Training and awareness
Educating employees about cybersecurity reduces the risk of human errors, such as falling for phishing scams. A Data Breach Investigations Report revealed that 68% of breaches involved the human element, highlighting the importance of awareness.
Data protection and encryption
Encryption is critical for safeguarding sensitive information during storage and transmission. Under GDPR, encryption renders personal data unreadable to unauthorized parties.
Incident response and recovery
A well-documented incident response plan helps organizations detect, contain, and recover from breaches. GDPR, for instance, requires organizations to report data breaches within 72 hours, emphasizing the need for swift action.
GDPR is one example of security compliance.
Importance of cybersecurity compliance
The overall benefits of compliance lie in its security and legal functions. These benefits include:
Saves cost
According to a data breach report, the global average cost of a data breach in 2024 was $4.88 million. Beyond that, Regulatory bodies impose fines and penalties on businesses that fail to adhere to security standards.
For example, Amazon faced an €887 million GDPR fine in 2021 for data privacy violations. Such penalties highlight the financial risks of ignoring compliance.
Protects sensitive data
Compliance mandates robust data protection measures to safeguard personal and organizational information.
An example is PCI DSS, which requires organizations to encrypt payment card information, ensuring that it's rendered unreadable even if hackers access the data.
Builds customer trust
Customers expect their personal and financial data to be protected, and they’re more likely to do business with companies that demonstrate a commitment to security. By adhering to regulatory standards, businesses signal to their customers that they take data protection seriously.
Enhances operational efficiency
Compliance frameworks require businesses to establish well-defined security processes. By adhering to these guidelines, organizations are forced to standardize their internal processes, which reduces redundancy and ensures consistent execution.
Compliance standards like ISO 27001 require organizations to develop an Information Security Management System (ISMS). This standardizes security operations, making it easier to track, audit, and manage security controls across the entire organization.
Proactive risk management
Compliance frameworks often emphasize proactive risk management, helping organizations identify and mitigate potential vulnerabilities before they turn into costly security incidents. These activities ensure that security flaws are addressed promptly, preventing the need for extensive remediation efforts later.
How to achieve cybersecurity compliance
Here’s a simple process to achieve cybersecurity compliance in your organization
Understand the requirements
Identify the frameworks relevant to your industry, location, and operations. For example, GDPR is essential for businesses handling EU citizens’ data, while PCI DSS is crucial for e-commerce platforms processing payments.
Conduct risk assessments and gap analysis
Carry out a comprehensive risk assessment to determine vulnerabilities and prioritize remediation efforts. A gap analysis helps identify gaps between your current practices and compliance requirements, highlighting areas requiring immediate attention.
Implement controls
Apply technical measures like firewalls, intrusion detection, encryption, and multi-factor authentication to protect systems. Administrative controls, such as role-based access and incident response plans, also help ensure compliance.
Engage experts and vendors
Use specialized tools and third-party services like compliance-as-a-service (CaaS) solutions to enhance compliance. Consult legal, cybersecurity, and IT professionals for more complex compliance requirements.
Regularly monitor and update
Compliance isn’t a once-and-done thing. It requires continuous monitoring and adaptation. For example, GDPR regulators frequently update their guidelines; businesses therefore must adjust practices to maintain compliance.
Conduct regular internal audits, track emerging threats, and stay updated on changes to relevant frameworks.
Document
Keep detailed records of compliance efforts, from risk assessments to employee training. These documents can demonstrate your organization’s commitment during audits or breach investigations.
Common compliance challenges and how to solve them
In your journey to building a compliant cyberspace, you may encounter some of the following challenges:
Changing regulations
Compliance frameworks are frequently evolving, making it hard for organizations to stay updated.
Solution
- Subscribe to updates from regulatory bodies and compliance framework publishers
- Engage compliance experts or consultants who can track these changes and advise on necessary adjustments
- Use automated compliance tools that notify you of updates and adjust configurations accordingly
Limited resources
Small businesses or understaffed IT teams may lack the time, expertise, or budget to meet compliance requirements.
Solution:
- Utilize managed security service providers (MSSPs) for affordable, expert assistance
- Focus on implementing the most critical compliance controls first (e.g., CIS Top 5)
- This free tool, NIST Cybersecurity Framework Starter Kit, helps smaller organizations begin their compliance journey
Employee non-compliance
Human error remains a leading cause of security breaches. Employees may inadvertently violate compliance policies due to a lack of training or understanding.
Solution:
- Implement training programs to reinforce best practices
- Implement user-friendly policies and tools like single sign-on (SSO) or automatic data encryption
- Carry out regular phishing simulations can also help build awareness and measure progress
Complex data management
Managing large volumes of data across multiple systems and platforms can lead to gaps in security and compliance.
Solution:
- Create a data inventory to track what data is stored, where, and how it’s protected
- Use data loss prevention (DLP) tools to detect and prevent unauthorized data transfers
Legacy systems
Older systems may not support modern compliance requirements.
Solution:
- Phase out outdated systems and prioritize upgrades for critical operations
- Use middleware solutions to bridge gaps between legacy systems and newer technologies
Lack of support from leadership
Without support from executives, compliance initiatives may fall short.
Solution:
- Highlight the business benefits of compliance, such as avoiding fines and improving customer trust
- Present case studies of organizations penalized for non-compliance to demonstrate the risks
- Use clear metrics, such as ROI from reduced breach incidents, to gain leadership support
Key cybersecurity compliance frameworks
Various cybersecurity frameworks exist as a set of standards and guidelines that help organizations manage and reduce cybersecurity risks. Some of the most notable include:
General Data Protection Regulation (GDPR)
This protects the personal data of EU citizens and applies globally to organizations handling such data. Mandated by the EU regulatory authorities, GDPR imposes fines of up to €20 million or 4% of annual global revenue (whichever is higher) for non-compliance.
It is essential for businesses in all industries that process personal data and emphasize data security and accountability through measures like encryption and breach notifications.
Health Insurance Portability and Accountability Act (HIPAA)
It’s enforced by the U.S. Department of Health and Human Services to safeguard sensitive health information. With annual penalties reaching $2 million, HIPAA is critical for healthcare providers and insurers in the U.S. It focuses on access controls, privacy, and breach notifications.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS ensures the secure handling of payment card transactions. Overseen by the PCI Security Standards Council, it mandates encryption, regular vulnerability scans, and secure network configurations. Non-compliance can lead to fines ranging from $5,000 to $100,000 per month, affecting industries like retail, e-commerce, and financial services.
ISO 27001
ISO 27001 is a globally recognized framework by the International Organization for Standardization (ISO). It provides a comprehensive approach to managing information security through an Information Security Management System (ISMS). While voluntary, certification enhances trust and reduces reputational risks.
It is widely adopted in IT, finance, healthcare, and multinational enterprises.
SOC 2 (System and Organization Controls)
Developed by the American Institute of CPAs, it ensures secure data management and processing. Though voluntary, it is usually a client requirement for SaaS providers that store, process, or transmit sensitive customer data.
SOC 2 focuses on the following principles:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
CIS controls
The CIS controls, created by the Center for Internet Security, provide 18 prioritized actions for securing systems and data. They are voluntary but highly effective for organizations starting their cybersecurity journey.
NIST Cybersecurity Framework (NIST CSF)
Developed by the National Institute of Standards and Technology, offers a flexible framework focusing on six core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
- Govern
It is particularly popular in critical infrastructure sectors.
Best practices for achieving security compliance
Here are things to consider to successfully achieve security compliance.
Foster a compliance culture
Make compliance a shared responsibility across the organization. Encourage leadership to champion compliance initiatives and integrate them into everyday operations.
Leverage technology
Automation simplifies compliance by streamlining monitoring, reporting, and incident response. Use Security Information and Event Management (SIEM) tools for real-time threat detection and compliance tracking.
Involve leadership
Gain executive support to secure funding and visibility for compliance initiatives. Leaders should actively participate in compliance reviews to align goals with business strategies.
Stay updated
Monitor regulatory changes and adapt practices accordingly. Subscribe to updates from regulatory bodies and participate in industry forums to stay informed. Regularly review and refine security measures to address emerging threats and align with evolving standards.
Welcome third-party audits
Engage external auditors to validate compliance efforts and identify gaps. Third-party audits offer an unbiased perspective and help organizations strengthen their security posture.
Data minimization
Limit data collection and retention to only what is necessary. By reducing the amount of sensitive data stored, organizations can lower their risk profile and simplify compliance efforts.
Cybersecurity compliance is more than a regulatory checkbox
Cybersecurity compliance is not just a legal obligation but a strategic imperative. By integrating robust security measures with compliance frameworks, organizations can protect their assets, build trust, and thrive in an ever-evolving cyber landscape.
Achieving compliance is an ongoing commitment that pays dividends in resilience, reputation, and operational excellence.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.





