The Purple Team: Combining Red & Blue Teaming for Cybersecurity

Organizations can often struggle to bridge the gap between offensive and defensive security strategies. The lack of collaboration and communication between red and blue teams can hinder their ability to effectively identify and mitigate security risks.
To solve this disconnect, organizations are opting to utilize a combined approach in cybersecurity strategy — a system colloquially known as “purple teaming”.
In this article, we’ll dive deep into the purple teaming approach, and help you understand how you can implement it in your environment.
What is the purple team?
The purple teaming approach combines the best attributes of both red and blue teams. Purple teams operate in a collaborative environment
- Simulating attacks like red teams.
- Defending against those attacks like blue teams.
They identify vulnerabilities within an organization's security infrastructure, evaluate existing defensive measures, and develop comprehensive plans to address weaknesses. This approach helps organizations stay one step ahead of potential adversaries.
From penetration testing and vulnerability assessments to incident response simulations, purple teams leverage the diverse skill sets of offensive and defensive experts to assess the effectiveness of security controls.
Purple team tasks and responsibilities
Purple teaming involves varied action items, including analysis and technical application — here’s what purple team members do as a part of their job:
Planning and strategizing
Red and blue teams join forces to define goals and objectives. By pooling their expertise, they develop a comprehensive strategy for conducting purple team exercises. This strategic approach ensures that the organization's security is thoroughly assessed, while creating a roadmap for continuous improvement and ultimately guiding the organization toward enhanced cybersecurity.
Vulnerability assessment and testing
Purple teams dig deep to identify weaknesses and vulnerabilities in the security infrastructure by simulating real-world attack scenarios. They secure the organization's defenses by testing the effectiveness of security controls and defenses.
After identifying potential vulnerabilities, purple teams apply prescriptive security controls to address them and thwart future attacks.
Attack simulation and red teaming
Simulating and executing controlled attacks on systems, networks, or applications challenges the organization's defenses head-on. By leveraging a wide array of attack techniques, tactics, and procedures (TTPs), purple teams evaluate the effectiveness of defensive measures.
Defensive evaluation and blue teaming
The red team works hand in hand with the blue team to dive deep into the effectiveness of security controls, reviewing the monitoring tools and incident response procedures currently in use. Once they have these analysis reports, they can provide valuable recommendations for improving the security posture of the organization.
Knowledge sharing and training
Purple teams hinge entirely on the information exchange between red and blue teams. Through training sessions and workshops, they enhance the skills of team members, equipping them with the latest techniques and strategies.
(Build your knowledge with these security certifications)
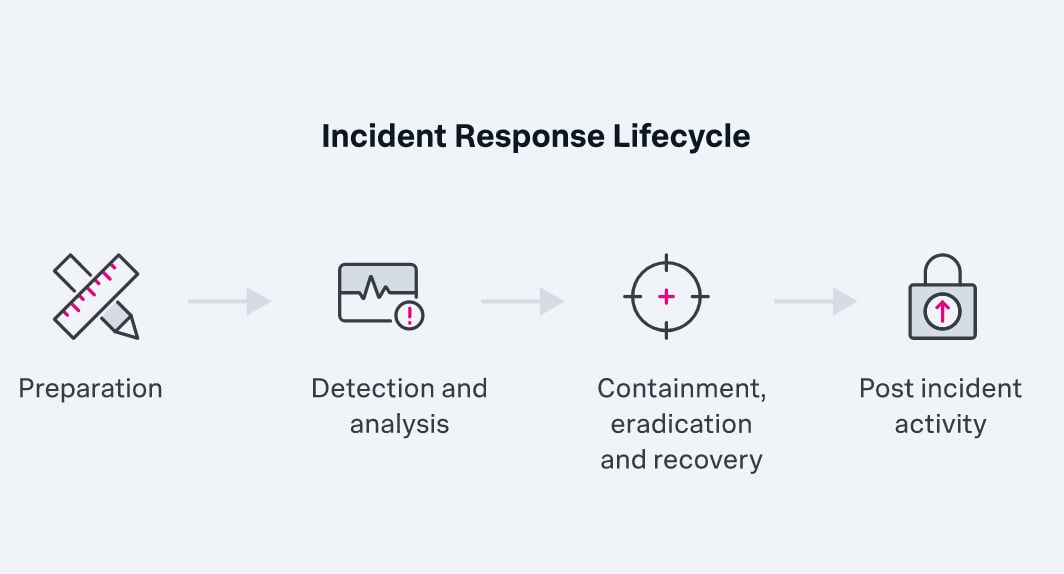
Incident response and management
When an attack is made, red teams jump into action, working side by side with the blue team to mitigate the impact of security incidents. After the dust settles, the purple team actively participates in post-incident analysis and remediation efforts.
By closely examining the root causes, they identify areas for improvement in incident detection, response, and recovery, to ensure that the organization becomes even more resilient to future threats.
(Read more about incident management & incident response metrics.)
Threat intelligence and research
The purple team constantly monitors the threat landscape to stay one step ahead of adversaries. They keep an eye on emerging attack vectors and tactics, techniques, and procedures (TTPs) to identify potential risks and vulnerabilities. Equipped with extensive research and knowledge, they provide valuable threat intelligence reports and recommendations to stakeholders to bolster defenses and make informed decisions.
Collaboration and communication
Purple teaming is all about strong communication between red and blue teams, but it also includes outside contacts. Purple teams establish strong connections with IT teams, executives, and other stakeholders to align security measures with the organization's goals.
They foster a collaborative culture by:
- Regularly reporting their findings
- Providing recommendations
- Updating about progress to management and decision-makers
Purple team framework: How to apply purple teaming in your organization
Putting these concepts into action, purple teams can follow this four-phase approach:
Phase 1: Gather threat intelligence
Cyber threat intelligence (CTI) provides evidence-based knowledge, context, indicators, and behaviors of potential threats that can impact an organization. A constant aspect of cybersecurity — this phase involves gathering threat data and disseminating analysis to red and blue teams.
By leveraging this intelligence, teams gain valuable insights into the tactics and techniques used by adversaries and are empowered in developing effective countermeasures.
Phase 2: Prepare the exercise
Preparation is crucial in setting the stage for a successful purple team exercise. In this phase, the purple team defines the goals and objectives of the exercise — establishing any guidance or constraints for red and blue teams. With thorough preparation, the purple team ensures that the exercise is focused, relevant, and aligned with the organization's security needs.
Phase 3: Execute the purple team exercise
In execution, the red team, representing the attackers, simulate real-world threat scenarios and attempt to exploit vulnerabilities within the organization's systems and networks.
The blue team, comprising the organization's defenses, actively monitor and defend against these simulated attacks. They analyze the red team's TTPs to gain insights into potential weaknesses in their defense strategies.
Phase 4: Review and document lessons learned
After a series of simulated attacks, the red and blue teams discuss the applied methodologies and work together to understand vulnerabilities in the system — as well as ways the organization may bolster its security posture.
After the exercise ends, purple teams capture the insights gained during the process. Exercise coordinators document minutes, notes, action items, and gather feedback from attendees and sponsors. From these inputs, they create a comprehensive “lessons learned” document. This report provides a roadmap for further improvements and adjustments to the organization's security posture.
Best practices for purple teaming
To ensure successful purple team exercises, organizations should follow these best practices:
- Clarify objectives for the purple team exercise, specifying what aspects of the security infrastructure will be tested and the expected outcomes.
- Engage skilled professionals from red and blue teams with the necessary skills for realistic, effective testing and productive collaboration.
- Foster collaboration, including open communication, knowledge sharing, and a supportive environment where teams can freely exchange information, insights, and lessons learned.
- Use realistic scenarios that emulate real-world threats and relevant attack techniques to provide accurate insights into the organization's security posture.
- Continuously improve, review, and update security controls based on findings and recommendations from exercises.
- Document and track exercise findings, vulnerabilities, and recommendations, tracking progress in addressing weaknesses and measuring the effectiveness of security enhancements.
- Involve stakeholders, such as senior management and relevant departments, to create awareness of cybersecurity risks, gain support for security initiatives, and facilitate necessary changes.
- Customize and scale purple team exercises to fit the organization's specific needs and size, adapting the approach to new technologies, threats, and business requirements as the organization evolves.
Advantages of purple teaming
Purple teaming offers several advantages for organizations, and some of them include:
Better collaboration: Purple teams facilitate collaboration and communication between red and blue teams, promoting knowledge sharing and breaking down silos.
Realistic testing: Simulating real-world attack scenarios provides organizations with realistic testing scenarios to identify vulnerabilities and weaknesses in their defense mechanisms.
Improved detection and response: Purple teams help organizations improve their detection and response capabilities by providing insights into new attack techniques and fine-tuning monitoring and alerting systems.
Training and skill development: Purple teaming allows blue teams to learn from red teams' offensive techniques, helping security professionals enhance their cybersecurity skills and understanding of vulnerabilities.
Risk mitigation: Identifying and addressing security vulnerabilities through purple team exercises helps organizations reduce risk exposure and mitigate potential threats.
Validation of controls: Purple teams validate the effectiveness of existing security controls and measures, providing valuable feedback on strengths and weaknesses in an organization's security infrastructure.
Compliance and regulatory requirements: Purple teaming assists organizations in meeting compliance and regulatory requirements by testing their security posture and demonstrating their commitment to robust cybersecurity measures.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




