The OWASP Top 10 Explained: Today’s Top Risks in Web Apps and LLMs
Key takeaways
- The OWASP Top 10 is a foundational, community-driven, and regularly updated list highlighting the most critical web application security risks, helping organizations focus their remediation efforts on vulnerabilities attackers most commonly exploit.
- Regularly updating and integrating the OWASP Top 10 into the software development lifecycle enhances security awareness, promotes secure coding practices, and proactively addresses evolving threats.
- Leveraging tools like Splunk to continuously monitor, detect, and respond to OWASP Top 10 threats enables real-time visibility, faster incident response, and a stronger overall web application security posture.
Over the past few years, cyberattacks have escalated to unprecedented heights. Just last year, in 2024, 94% of organizations reported being the victims of phishing attacks. And in the first five weeks of 2025, ransomware attacks increased by 149% in the first 5 weeks of 2025.
Organizations and users need help understanding and navigating these changing risks to fight against the rising tide of cybercrimes.
Thankfully, that is exactly what The OWASP Foundation aims to do. In this article, we’ll look at:
- Who OWASP is
- The latest OWASP Top 10 for web applications
- The emerging Top 10 list for LLMs
- Projects in progress
What is OWASP?
OWASP, or the Open Worldwide Application Security Project, is an international non-profit focused on improving software security. Founded in 2001, OWASP is an open community with a membership in the tens of thousands. Together, the community helps organizations develop, obtain, maintain, and manage trusted applications.
What’s the OWASP Top 10?
One of OWASP’s most ambitious and widely known projects is the OWASP Top 10, a regularly updated report outlining the ten biggest web application security risks. Their very own website describes it as a "standard awareness document for developers and web application security", and we can sum up its two main purposes:
- To provide a consensus from members about the most critical security risks web applications and organizations face.
- To help the community secure their applications by identifying and explaining the most common vulnerabilities.
A critical benchmark since its inception in 2003, OWASP updates the list every few years as a direct response to what’s happening in the world: evolving attack techniques and emerging threats.
For example, previous versions have highlighted risks that are now commonplace, like broken authentication, injection flaws, and evolving security misconfigurations.
2021 OWASP Top 10: Why it matters and what’s changed
OWASP Top 10 is a crucial resource for organizations dedicated to enhancing web application security. It outlines the most pressing security vulnerabilities in web applications, serving as a critical guide for organizations to identify and manage potential risks.
Understanding and adhering to OWASP Top 10 is not only good cyber practice but a critical way to support regulatory compliance. Many industry and legal regulations reference OWASP Top 10 as a standard for security applications. Organizations must align with these guidelines in order to:
- Meet regulatory requirements
- Avoid penalties
- Promote client and partner trust
The OWASP Top 10 helps organizations code securely. It provides actionable information on common security vulnerabilities, which helps educate developers, QA personnel, critical employees, and stakeholders. It’s an effective tool to prioritize security efforts, directing attention and resources to the most severe threats.
2025 OWASP Top 10
To be clear, OWASP has not yet released the 2025 Top 10 list for web applications, though they intend to do so, as they’ve been gathering data from across the industry since the 2021 list. At the time of this article’s publication, the OWASP website says they’ll be releasing the 2025 version in the first half of the year.
OWASP website on March 25, 2025.
The current OWASP Top 10 vulnerabilities
The OWASP Top 10 was updated in 2021 from the 2017 version to better reflect the transforming landscape of web application security risks. Some of the most notable changes include:
- New or reframed risks. The 2021 list added risks not present in the 2017 version, or reframed and broadened them to reflect the changes in the cybersecurity landscape.
- Ranking changes. Changes in the ranking of various risks indicate shifts in their severity or prevalence.
- Removed risks. Some risks from the last version no longer appear, which suggests they’re less prevalent or other risks have surpassed them in importance.
The 2021 version reflects a broader approach to modern security, with an emphasis not just on individual vulnerabilities but also on security design and management practices.
(Understand the relationship between vulnerabilities, threat, and risk.)
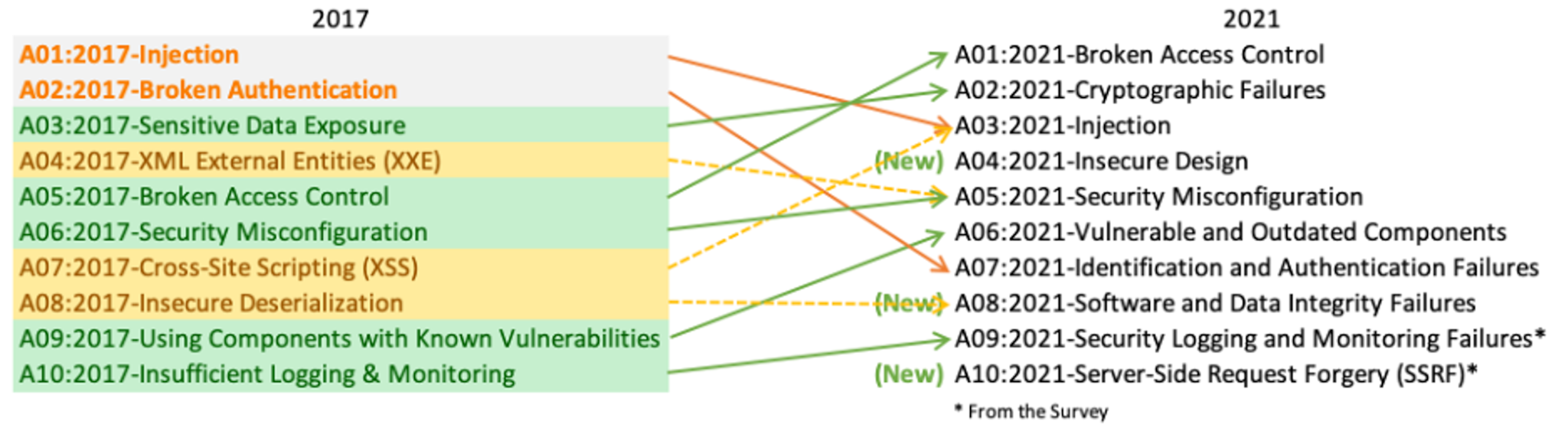
(Source: https://owasp.org/www-project-top-ten/)
OWASP Top 10 Vulnerabilities (2021)
As of this publishing, OWASP has not yet released an update to its top 10 web application security lists that was published in 2021. However, the speedily changing threat landscape and the integration of AI seemingly everywhere suggests potential shifts in focus for an upcoming 2025 list.
(OWASP has released a specialized top 10 list in November for security concerns related to Gen AI and LLM applications. More on that after this list.)
Here are the top ten security risks according to OWASP for 2021:
#1: Broken access control
OWASP moved broken access control to #1 after discovering that 94% of the applications they tested had some broken access control.
Broken access control occurs when organizations do not adequately enforce authenticated user restrictions. Attackers exploit this weakness to access sensitive data and functionality.
#2: Cryptographic failures
Known as “sensitive data exposure” in 2017, this vulnerability moved up one spot from number 3. Here, cryptographic failures includes anything related to misusing (or not using) cryptography when needed to protect data. These failures lead to data exposure that cybercriminals can exploit.
#3: Injection
Injection moved down from the number one spot in 2017 and added cross-site scripting as a part of the category.
Injection flaws happen when data from unverified sources is relayed to an interpreter as an element of a command or query. It potentially deceives interpreters into performing commands that were not intended or allowing access to restricted information.
This vulnerability is now evolving and includes emerging threats that target AI driven applications, like prompt injection attacks.
#3a: Prompt injection attacks
This is a security threat meant for AI-driven application. This attack particularly targets large language models (LLMs).
The attacker manipulates prompts to alter the behavior of the AI, thus bypassing restrictions or extracting confidential data. Prompt injection is quite similar to traditional injection attacks, but it exploits AI models by injecting malicious instructions that override the required functionalities, leading to misinformation or potential data leaks.
(Read our article on SQL injections for an exploration of injection attacks.)
#4: Insecure design
A new category in 2021, insecure design includes all vulnerabilities that result from insufficient consideration of security during the design and architecture of the software. It leads to inherently insecure software that is open to exploitation.
(Related reading: the concept of “secure by design".)
#5: Security misconfigurations
This moved up one rank from number 6 in 2017. Security misconfiguration occurs at any level of an application stack, including the platform, network services, application server, web server, frameworks, database, custom code, pre-installed containers, virtual machines, or storage.
Attackers exploit these misconfigurations to access unauthorized information or functionality.
#6: Vulnerable and outdated components
Moving up three ranks from 2017, this now includes components that pose both known risk and potential risk.
Applications that incorporate components with recognized vulnerabilities weaken the defensive system measures, opening up opportunities for various forms of attacks and consequences. These components are the vulnerable points that attackers look for when exploiting systems.
#7: Identification and authentication failures
Known as “broken authentication” in 2017, this moved down from #2. In this scenario, if the software fails to identify and authenticate users properly, it cannot enforce access controls. Attackers exploit these issues to impersonate other users or elevate their privileges.
#8: Software and data integrity failures
A new category in the 2021 OWASP Top 10, this involves insecure code or data handling, leading to potential manipulation and untrusted information within the software development lifecycle.
These types of vulnerabilities can result in unauthorized changes to data or software execution paths.
#9: Security logging and monitoring failures
This entry moved up from #10 on the 2017 list when it was known as insufficient logging and monitoring. Inadequate logging and monitoring, along with poor or non-existent coordination with incident management, provides bad actors with opportunities to:
- Escalate system attacks
- Establish ongoing access
- Migrate to additional systems
- Interfere with, extract, or destroy data
#10: Server-side request forgery (SSRF)
This is another new category for 2021. In an SSRF attack, a cybercriminal can manipulate server functionalities to access or alter internal resources. The bad actor has the capability to provide or modify a URL, to which the server-based code will retrieve or input, often leading to unauthorized actions.
(Related reading: when to use server-side rendering.)
OWASP Top 10 for GenAI and LLM Applications (v1.0)
Historically, OWASP primarily focused on risks in web apps. Tellingly, however, OWASP officially released an updated top 10 just this year — this time for LLMs, or more precisely: applications using large language models (LLMs).
Certainly, this is in response to the sudden speed and power that developers and hackers alike have for using generative AI to develop and/or detect vulnerabilities and threats. So, let’s discuss some security implications of an LLM based system agency.
LLM-based system agency & its security implications
Typically, LLM-based systems are granted some degree of agency. This agency allows it to automatically scan through inputs, generate response and sometimes trigger actions in applications.
While this enables the application to have a more dynamic and interactive experience, it also increases security risks.
Attackers can harness offensive tactics like prompt injection, resulting in unauthorized transactions, harmful code generation, altering or leakage of sensitive data, etc. In the absence of a strict control or governance system, the AI systems can act beyond their intended scope — which may lead to compliance or security breaches.
(Concerned about security in your LLMs? Learn how to defend against the OWASP Top 10 for LLMs.)
System prompt leakage in LLM
A major risk associated with LLMs in apps is system prompt leakage. Let’s explain.
System prompts are hidden instructions that can regulate the response of a model. Leakage of system prompts occur when attackers extract hidden system prompts that are embedded within an LLM. There are confidential guidelines in the prompt that control the interaction of a model with users — similar to any proprietary algorithm, such as Google’s search engine.
Once these prompts are leaked, the attacker can more fully manipulate the LLM, tricking it into:
- Revealing sensitive data.
- Bypassing restrictions.
- Altering security protocols.
This vulnerability is particularly concerning in AI-driven customer service and support — anywhere you’re dealing directly with customers — because the leaked prompt may expose sensitive information like user’s authentication method, private records, or proprietary algorithms.
Preventing such breaches requires prompt obfuscation techniques and strong access control.
Apart from controlling the system's behavior, attackers can also use a breached LLM to spread misleading or false information, leading to our next major concern.
Misinformation from LLMs is a vulnerability
LLMs do not verify their output's accuracy, which increases the likelihood of misinformation being generated as the response. This lack of factual evaluation means anyone can intentionally feed misleading data to an LLM. Potential outcomes here include:
- Harmful recommendations
- False reports
- Manipulated facts
Intentional misinformation — including lies — is dangerous everywhere, and perhaps especially in domains like law, finance, and journalism.
With LLMs, “security” isn’t just about protecting internal information, as we often think of with cybersecurity. LLM security is really about looking at all the ways people can abuse or misuse them, and the downstream effects that misuse causes — because LLMs are continually learning. So, anywhere that you’re using LLMs, you must work to reduce the risk of misinformation, by implementing processes like:
- Source attribution features
- Fact checking protocols
- Model training safeguards
Boundless resource consumption is a security risk
While misinformation affects integrity and trust, another challenge that arises from LLM usage is managing resource consumption, a risk that can negatively impact the efficiency and stability of the LLM.
Most LLMs are designed to let compute resources flow unbated: the idea of boundless consumption. This feature can also be harnessed for attacks. Here, attackers can trick the model, making it process huge amounts of data, resulting in:
- System slowdown
- Extraordinarily high costs to operate
With carefully crafted prompts, attackers can exploit this resource vulnerability and force the LLM into generating long responses or indefinite loops. In the worst case, unbounded consumption can lead to DoS (denial-of-service) attacks. The system gets overwhelmed and becomes unable to process legitimate requests.
To prevent this exploit, you must:
- Enforce strict token limits.
- Monitor real time AI workloads.
- Limit the rate of responses.
What is the OWASP Top 10 2025 Data Analysis Plan?
With its data analysis plan, OWASP is in the process of compiling an extensive data set of identified vulnerabilities collected from different sources, like consultancies, security vendors, bug bounty programs, etc. This collected data will facilitate the analysis for their coming-soon 2025 Top 10 list and also support future research.
To compile the dataset, OWASP, plans to use its Azure cloud infrastructure to collect, analyze, and store the contributed data. This initiative consists of both pseudo-anonymous as well as verified submissions, with an added preference for known contributors for enhancing data validation.
The window of contribution was open until December 31st, 2024. Contributors were encouraged to provide detailed metadata, like the count of tested applications, type of testing, primary languages used for programming, geolocation and industry sectors.
This approach ensures an insightful and robust analysis, guiding the cybersecurity community and informing the OWASP top 10.
Understanding risks inside web applications
As organizations navigate an evolving and threatening digital landscape, it’s critical that we understand the potential security risks. The OWASP Top 10 servers are a vital guide to identifying, understanding, and mitigating these risks. It reflects the changing threat landscape and highlights the need for constant vigilance and adaptation in the face of emerging threats.
As technology continues to transform, so too will the threats your organization faces. Staying up to date on lists like the OWASP Top 10 is crucial for maintaining a robust defense. In today’s interconnected world, a commitment to cybersecurity is not just an option — it’s a necessity.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.



