What is Network Security?

With non-stop cyber threats, you must ensure your networks are strong. Strong enough to combat risks and threats to their security.
So, let’s dive deep into the world of network security. In this article, you’ll learn:
The actual meaning of network security in computer networks
Different types of attacks on your networks
Network security tools you can use to protect against these attacks
Key challenges in securing your network
Let’s get straight into the topic.
Defining network security
Network security secures digital data and infrastructure from cyber threats while ensuring your systems' confidentiality, integrity, and availability.
Integrating policies, technologies, processes, and people, the practice of network security aims to protect networks from unauthorized access, attacks, and misuse. This discipline protects sensitive information in personal and professional contexts and maintains operational continuity with trust.
As cyber threats continue to grow, you must understand network security to prevent real-world security breaches in your organization.
Active vs. passive network attacks
The world is full of threats, ranging from silent observers to immediate attackers. These threats manifest as passive or active attacks and create unusual challenges to network systems.
Passive attacks
Passive attacks involve attackers intercepting or monitoring data without altering it. These attacks stand out for their stealth and persistence.
Here are some examples of passive attacks:
Eavesdropping attacks — also known as sniffing or snooping — occur when attackers intercept, delete, or modify data transmitted between two devices. These attacks exploit unencrypted network communications to access data in transit.
For example, in modern-day systems, attackers intercept phone calls without physical access to the device. Similarly, they can compromise computers to capture voice conversations, online chats, and keystrokes.
Port attacks occur when attackers quietly scan your network's ports to map out vulnerabilities. They identify open ports to plan future attacks without getting detected.
For example, a hacker finds your open ports that are not secured. Upon discovering an open FTP port, the attacker exploits it to gain unauthorized access to the network. They then use this entry point to deploy malware, disrupting operations and stealing sensitive information.
Traffic analysis is when attackers analyze communication patterns within a network to infer sensitive information. They examine the flow of data — its volume, timing, and destination to carry out targeted attacks.
For example, a sudden spike in communication between financial servers indicates a financial transaction, which attackers could target for fraud.
Active attacks
Active attacks disrupt data and network functionality. These attacks make their presence known through their disruptive techniques.
Viruses are malicious programs that replicate and spread. When they spread in your systems, your data corrupts, and your files are destroyed. They can cause anything from minor disruptions to catastrophic data loss.
For example, if an employee accidentally opens a malicious email attachment, thinking it's a legitimate document, the virus quickly spreads through the company's network. It corrupts files and causes system malfunctions. (This employee accident is one form of insider threat.)
As a result, critical data is lost. And that’s how just a single, innocent click can lead to significant data recovery costs.
Denial-of-service attacks occur when attackers flood your network with overwhelming traffic. Once your system slows down so much that it becomes unusable, they spot vulnerabilities and either collect your data or disrupt your files.
For example, in February 2020 AWS reported mitigating one of the largest DDoS attacks ever, with a peak traffic of 2.3 Tbps. This colossal attack used CLDAP (Connection-less Lightweight Directory Access Protocol) web servers that amplified the volume of attack traffic directed toward AWS's infrastructure.
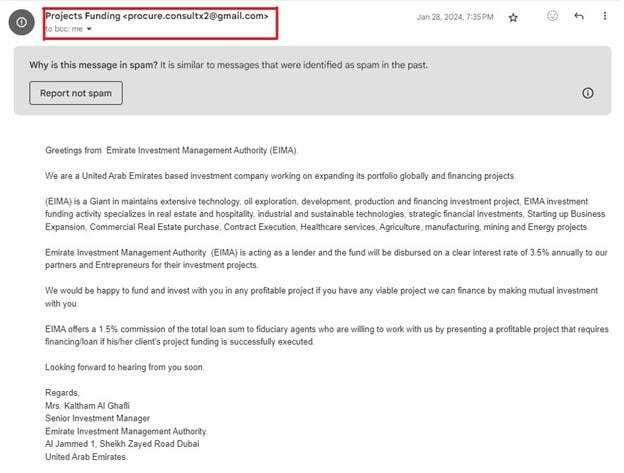
Phishing means tricking individuals like you into revealing sensitive information or granting access to secure systems.
In such cases, attackers disguise their attacks as legitimate communications to exploit trust and breach defenses. An attacker might send emails that appear to be from a trusted source, such as a reputable organization—asking you to share important details.
For example, this is an email I got pretending to be from the federal government agency in Dubai. How do I know it’s fake? By looking at the email address. Why would a federal government agency from a foreign country want to know my financial project details? If it doesn’t make sense, be aware.
|
Network security tools & protections
Strong network security requires a suite of tools and protections to safeguard against cyber threats and unauthorized access. Let’s look at the best safeguards within the four primary areas of network security.
Access control
Access control includes a mix of smart technologies — from passwords to biometrics — that ensure your digital identity is as unique and protected as your fingerprint. It restricts access to networks and makes it easier for authorized users to access them.
Zero trust treats trust as a vulnerability. It assumes everyone is a potential threat — after all, breaches happen every day. To prevent such breaches, zero trust verifies everything, making security dynamic and adaptive.
Threat prevention and response
Firewalls monitor and regulate network traffic. They adhere to established security rules and ensure that only legitimate traffic enters or exits. As a result, this critical layer of defense protects against potential threats to network security.
Intrusion prevention systems (IPS) identify and neutralize threats before they can disrupt systems. These systems identify and block attacks to shut down potential breaches by analyzing network traffic in real-time. As a result, this proactive approach can:
Thwart known threats.
Adapt to counter new, emerging challenges.
Anti-virus and anti-malware software scans, detects and removes malicious software to safeguard against viruses, worms, and other cyber threats. This maintains system integrity and ensures that sensitive data is safe.
By understanding the normal behavior of users and systems, behavioral analytics spots inconsistencies that signal a security threat. This sophisticated approach leverages data analysis to identify unusual patterns and give an early warning sign against potential breaches.
Data protection
Data loss prevention (DLP) monitors, detects, and blocks the transfer of sensitive data outside the network's security limits. These systems prevent data leaks that could lead to financial loss or reputational damage.
Email security implements robust measures that filter harmful content and prevent unauthorized access. Security teams can use advanced scanning techniques to identify and neutralize threats before they reach the inbox, ensuring that email remains a safe and reliable form of communication.
Application security protects business applications from vulnerabilities that attackers could exploit. This includes:
Conducting regular security assessments.
Applying patches promptly.
Organizations can reduce risk profiles by prioritizing these areas and ensure their operations, data, and communications are secure.
Network management and segmentation
Network segmentation means organizing your network into secure, manageable segments instead of one open space. By dividing the network into segments, you limit access to authorized users and reduce the attack surface. With network segmentation, you can:
Enhance security.
Improve performance.
Troubleshoot easier.
Hyperscale network security expands security protocols to protect large-scale networks without sacrificing performance. You leverage automated security tools, advanced threat intelligence, and robust incident response strategies to protect larger networks.
Key challenges in network security
Despite advancements in network security, the fact remains: our networks are under threat every day. Here are some of these key network security challenges — along with their mitigation strategies.
Ransomware security and remediation strategy
Ransomware affected 66% of organizations in 2023. This reminds us that the risk of ransomware is too big — with potential permanent data loss looming over encrypted files and secure databases. It's a threat that can cripple even the most robust organizations.
The frontline of defense starts with your people. So, educating employees about the pitfalls of phishing and the risks of malicious links is an empowerment strategy.
You’ll also need a remediation strategy to replicate data. Have plans B, C, and D ready if plan A doesn’t work. It is precisely in the aftermath of an attack when the ability to recover quickly separates the resilient from the rest.
Simply put, tackling ransomware is as much about mindset as technology. Despite focusing on the technical aspects, you must:
Establish a culture of vigilance.
Embrace up-to-date defenses.
Always have a recovery plan (or two).
(Beware these ransomware trends.)
Risk of identity theft
Hackers create phishing sites and emails to steal your login details. They expertly mimic real websites to trick you. These phishing attempts are often just the beginning. They pave the way for larger attacks. Here, the biggest vulnerability is your employees.
So, how do we turn the tide against these deceptive tactics? It starts with smarter web browsing rules. Limiting website access helps cut down risks. The real game-changer, however, is building a strong cybersecurity culture.
Teach your team to spot phishing scams. Make it second nature. Encourage them to question emails that ask for personal information, even if they look legitimate. This will create a workforce that's as alert and responsive as any premium security software.
DDoS attacks
Cybercriminals behind DDoS (Distributed Denial of Service) attacks have a variety of motives. For some, stealing financial data drives their actions. Wondering how? They leverage DDoS attacks to extract ransom from companies and regain access to their online services.
Others try to undermine competitors. They aim to destroy reputations and disrupt business operations. The end result of their actions impacts businesses and consumers alike.
However, traditional defense mechanisms no longer suffice. And the nature of DDoS attacks is mutating, with cybercriminals constantly devising new methodologies to exploit vulnerabilities. This requires a dynamic response.
Try a new solution that defends against known threats and adapts to new tactics. The key here is to become used to automatic updates.
Integrating automatic updates ensures that defenses remain robust, even if attackers refine their strategies. This approach will make networks more resilient and infuse confidence among stakeholders, from business owners to end-users.
‘Bring Your Own Device’ policy
Bring Your Own Device (BYOD) policies have become a trend. However, this trend has its pitfalls —particularly related to IT security. The risks associated with stolen or hacked devices are threats businesses can’t ignore. For this reason, preparing an effective BYOD policy avoids these risks and any associated threats.
The basics of the BYOD strategy revolve around securing mobile devices. Recognize that complacency is the enemy. Set strong passwords to make it the first line of defense.
Equally critical is the principle of specific access rights. Limiting access to sensitive data based on roles minimizes the risk of internal threats and creates a more streamlined environment.
Implement identity and access management
Identity and Access Management (IAM) empowers organizations to establish granular control over access to applications and data. It verifies user identities and grants access based on predefined roles and responsibilities.
This ensures users can only access the specific applications and data required to perform their designated tasks. As a result, this minimizes unauthorized access risks and subsequent data leakage.
To mitigate potential security threats, here’s what IAM systems do:
Monitor user login behavior.
Flag suspicious activity.
Trigger additional authentication steps.
Organizations can build a resilient and secure digital foundation by deploying a comprehensive IAM solution.
How secure is your network?
Whether your organization wants to defend against passive eavesdroppers or active disruptors — the right mix of tools and awareness can help.
From access control to data protection and beyond, every measure counts. But technology alone isn't enough. Creating a culture of cybersecurity awareness and preparedness is just as crucial. So, how secure is your network?
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.