Hacking 101: Black Hat vs. White Hat vs. Gray Hat Hacking

"Hacking" is the term for any type of unauthorized access to a computer or network, achieved by exploiting a weakness in the system.
Essentially, someone breaking into your computer and data who shouldn’t be there. This definition suggests the negative connotation of hacking — especially considering the state of cybersecurity and privacy risks facing an average internet user.
The cost of global cybercrime is expected to reach $10.5 trillion annually by the year 2025, risking the privacy of internet users. In fact, internet users now total over 64% of the global population, or 5.16 billion individuals. This makes cybercrime activities (aka hacking) a concern for every one of those internet users — not to mention organizations that rely on the internet.
But is hacking evil? As it turns out, many organizations and security experts adopt a popular strategy when it comes to cybersecurity: the best defense is a good offense. The practice of ethical hacking has gained popularity in recent years and has given rise to three main categories of hacking:
- Black hat
- Gray hat
- White hat (Ethical hacking)
Let’s review the key differences between these hacking categories and understand what they mean for our online presence.
What is black hat hacking?
Defining black hat hacking
Black hat hacking refers to the practice of unauthorized computer system access with malicious intent. Their actions violate laws, compromise security, and often result in harm to individuals and organizations. They may be any number of threat actors:
- Individuals intending to access another user’s online accounts and data.
- Organized cybercrime rings that steal personal information such as credit card information, or hold access to data and computers in exchange for financial or socially motivated goals.
- State-sponsored cybercrime rings that compromise critical infrastructure and organizations to achieve political or strategic military goals.
Black hat hackers adopt a range of strategies to compromise their targets. They may use social engineering activities such as phishing to compromise the human element — the weakest link in the cybersecurity chain — especially when the target is an individual user.
They may exploit known vulnerabilities in technologies to target a large audience group, some of which may fall victim to the attacks. State-sponsored hacktivism takes it a step further and exploits backdoors planted into technologies used by government and military organizations in other countries.
Black hat hackers typically coordinate their activities and gain access to hacking tools in underground dark web markets — most of their attacks are not aimed at specific individuals but user groups that may be running outdated vulnerable technologies. They rely on low-effort social engineering and zero-day exploit attacks.
State-sponsored hacktivists, on the other hand, typically rely on sophisticated tools, try to find unknown (and unpatched) technology vulnerabilities, and have vast resources at their disposal. The Stuxnet attack is a notorious example.
(Black hat hacking shares a name with one the longest standing security events: Black Hat and the related DEFCON.)
The motivation behind black hat hacking
So, why do black hat hackers hack? Many reasons:
Financial gain
Black hat hackers may steal sensitive information to use or sell it, or compromise systems for financial gain. Another option: they could freelance for other parties who are willing to pay them a good amount for their services.
(Related reading: cybercrime as a service.)
Ideology and beliefs
Some black hat hackers hack to promote their ideologies and beliefs: this group is sometimes known as "hacktivists". They perform attacks that either result in upholding their beliefs or bringing down entities that are against their beliefs.
Revenge
Black hat hackers hack when they believe some individual or system has wronged them. They launch attacks on these parties as a way of payback. This could be ex-employees of an organization or someone the individual has interacted with in the past.
Adrenaline rush
“Some people just want to watch the world burn.” Some black hat hackers fall into this category where they don’t have particular benefits. They launch attacks because they seek thrill from it and get satisfaction when they succeed.
Famous examples of black hat hacking
- Equifax data breach: In 2017, black hat hackers breached Equifax's security and compromised sensitive data such as names, addresses, and phone numbers of 148 million users. It's believed that this attack was sponsored by China.
- WannaCry ransomware: Black hat hackers spread dangerous ransomware that infected thousands of computers around the world. The WannaCry ransomware encrypted business-critical and sensitive data, and the black hat hackers demanded ransom payments for decryption of data.
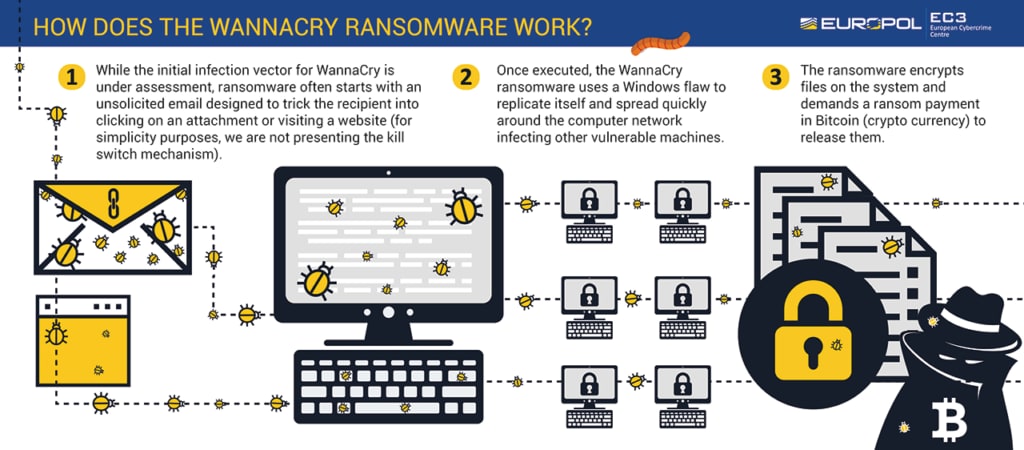
(Image source: EUROPOL)
What is white hat hacking?
Defining white hat hacking
At the opposite end of the spectrum is white hat hacking, also known as ethical hacking. White hat hacking is the antithesis of black hat hacking.
White hat hackers are individuals authorized to find and exploit vulnerabilities in a system. They try to hack the target with the permission of the owners and within legal frameworks.
They may be employed by technology companies, business organizations, and government entities to identify weak links in their security chain. These are security specialists with certified academic backgrounds — as opposed to black hat hackers, who tend to be hobbyists — and are employed as key members of the security department, partner team, or external consultants.
The goal of white hat hacking is to examine every possible security risk acting from the perspective of a cybercriminal. Once a vulnerability is identified, the organization works with white hat hackers and security pros to issue a fix. It’s often one part of a larger cyber threat intelligence (CTI) strategy.
The motivation behind white hat hacking
Improving security
White hat hackers try to identify security weaknesses in systems. This helps organizations to prioritize and fix them and prevent malicious actors from exploiting them.
Protecting data
White hat hackers play a vital role in safeguarding personal and corporate data. They help in preventing breaches that could result in identity theft, financial loss, or legal repercussions.
Regulatory compliance
White hat hackers help organizations test their defenses. Their evaluation helps organizations determine whether they comply with applicable regulations. And if there’s any aspect that doesn’t meet the standards, organizations can then work on achieving those standards.
Experience and compensation
White hat hackers are well paid. According to salary.com, the average base salary of a white hat hacker is over $100,000. The more ethical hacking projects they take up, the more experience they gain. And the higher the experience and expertise, the better the compensation.
In recent years, the scope of white hat hacking has extended beyond internal cybersecurity departments. Tech companies regularly offer bounty programs that motivate hobbyists and industry experts to find vulnerabilities in their systems in exchange for rewards and recognition.
Famous examples of white hat hacking
- Heartbleed: In 2014, a team of white hat hackers team discovered a vulnerability in a version of the OpenSSL cryptography library. The Heartbleed vulnerability allowed hackers to steal sensitive data, including passwords and encryption keys, from web servers. After disclosure, OpenSSL released an update where this vulnerability was mitigated.
- Tesla’s vulnerabilities: The Synacktiv team discovered multiple security weaknesses in Tesla’s software (view their PDF) that could allow attackers to execute malicious code. Tesla rewarded the researchers with good compensation and a car for their future research.
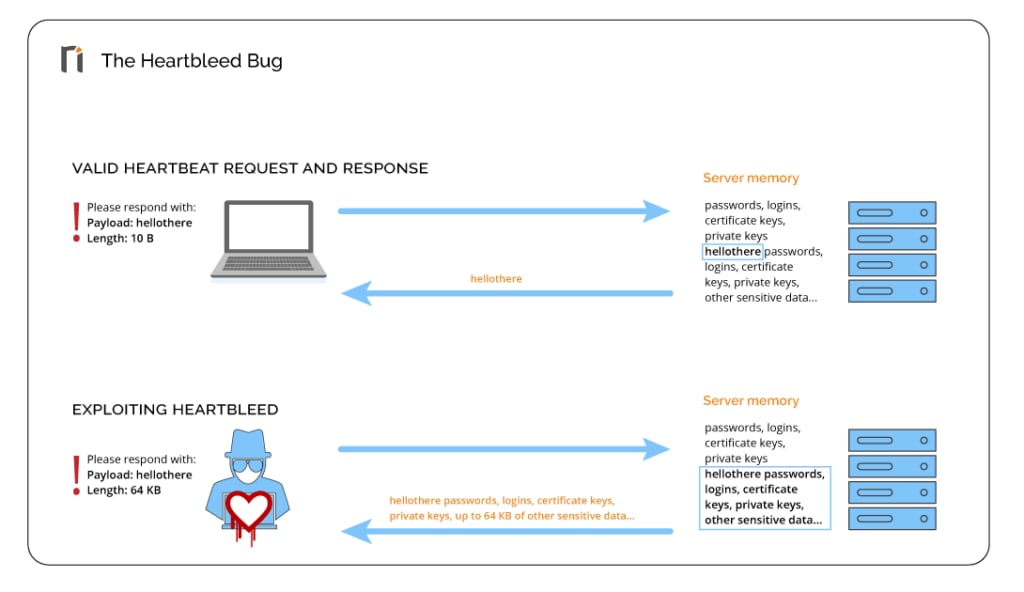
(Image source.)
What is gray hat hacking?
Defining gray hat hacking
At the middle of the hacking spectrum is the practice of gray hat hacking. These hackers are neither motivated by malicious intent nor are they formally employed and authorized to conduct hacking activities. Gray hat hackers typically don’t cause damage to a victim — they discover vulnerabilities that can potentially cause damage. Then, these gray hatters reach out to the affected parties and notify them regarding the issues.
In case the party fails to respond or notice, the gray hat hackers often expose the exploit publicly, typically at white hat conferences and groups where the community can work together to fix the problems.
The motivation behind gray hat hacking
Curiosity
Gray hat hackers are a curious bunch. If they come across security weaknesses or something else that piques their curiosity, they try to explore it more. They find it thrilling to test their skills. Gray hat hackers might also hack to try to understand how things work internally. Again, curiosity.
Self-promotion
When a gray hat hacker successfully hacks into something, they're proving their skills. This becomes a way for them to promote or advertise themselves and gain recognition. Their proven ability can gain them a reputation, especially in the hacking community.
Public service
Some gray hat hackers believe that they're serving society with their skills. They try to find security weaknesses in organizations and report to the organization to help them fix the weaknesses before someone else exploits them for malicious purposes.
Famous examples of gray hat hacking
In 2016, a security researcher named Justin Shafer discovered a security issue in one vendor's Electronic Health Records (EHR) system that was in use at a large hospital system. At first, Shafer responsibly informed the organization about this issue. But, after zero response from them, he posted about the issue on his blog.
What was the grey area here? Some critics saw Shafer's hacking into the EHR software as unethical: he didn't have proper authorization. Still, despite the real controvery, the hospital system and the vendor both took steps to shore up security.
Before that incident, and with less serious consequences, a gray hat hacker discovered a glitch in Facebook in 2013. This glitch allowed him to post on Mark Zuckerberg’s Facebook wall. He tried reporting the security issue to Facebook's team, but after no convincing response, he wrote on Mark's wall about the issue.

Facebook CEO’s personal Facebook page, gray hat hacked in 2013. Remember this interface? (Image source)
What are other types of hackers?
Apart from the major categories ("colors") we've covered, we have a few more hats of hacking:
- Green hat: Green hat hackers refer to new hackers who are still learning the basics of hacking and have limited skills. They are usually eager to experiment with hacking and learn as they go.
- Blue hat: Blue hat hackers are external security professionals that companies bring in to test their systems and networks for security weaknesses.
- Red hat: Red hat hackers are vigilantes in the hacking world: they target black hat hackers. What distinguishes them from white hat hackers is that red hat hackers are more aggressive and offensive toward black hat hackers and may not always operate within legal boundaries.
- Purple hat: Purple hat hackers are hackers who mean no harm to others but are also not directly helping organizations improve security. They usually hack their own systems or networks to learn and upskill themselves.
(Related reading: red vs. blue security teams & purple teams.)
Protecting against hacking
So how do you protect against all kinds of hacking attempts: white hat, black hat, or gray hat? Since most of the hacking attempts rely on simple social engineering tactics and known vulnerabilities, the following best practices can help improve your online security against hacking activities:
- Use strong passwords.
- Never download files or click links unless received from a confirmed legitimate source.
- Watch out for symptoms of hackers impersonating legitimate organizations. A typo or capitalized letter in the website URL likely points to a hacking attempt.
- Keep your systems and software up to date.
- Limit the information you share online.
- Keep track of your online financial activities. Alert the correct authorities in case of anomalous or suspicious activity.
- Keep strong Identity and Access Management (IAM) systems for your business, adopting the principle of least privilege access.
As always: follow cyber hygiene standards and normal security controls for any organization.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




