What Is Cyber Hygiene? Introduction, Best Practices, and Next Steps for Organizations

Good cyber hygiene prevents the worst security attacks.
Cyber hygiene has become a highly visible topic in all business segments. Creating software and new features happens at a very fast pace — requiring lots of internal processes and operations to keep this up to date.
However, it's also very important to be concerned with the fundamentals of information security in order to keep the company's digital assets protected. In this article, we'll discuss in detail the concept of cyber hygiene and some good practices to follow.
(For the latest in cybersecurity, check out these security & InfoSec events.)
What is cyber hygiene?
This is the idea behind cyber hygiene: to create a structured and intelligent environment that reduces the risks of external contamination without having to consistently spend lots of IT effort on these processes. This way, you and your team have more time to use the same environment in more productive and strategic functions, generating good business and operational results.
Cyber hygiene is basically a structured approach to cybersecurity across an organization., though it's less formalized than cyber frameworks.
We can understand cyber hygiene by making an analogy related to a hospital: the structure helps so you don't have an entire team of paramedics solving emergencies all the time. Think of the basic actions of a hospital to prevent viruses from spreading, to prevent patients from taking risks and to make the work of doctors easier. In this example, we can point to a few important components:
- There's strict control in triage and in relation to the access of patients and companions. Inpatients can be visited, but visitors need to register and are monitored at all times by nurses.
- The site routine undergoes cleaning and conditioning checks to ensure that there are no harmful agents in the environment.
- In cases that are more serious, with greater risks of contamination, patients stay in isolated areas with greater restrictions and close control over the situation.
Benefits of cyber hygiene
Components of cyber hygiene
You may have already noticed how the same structure can be applied in a company's system or database. We can summarize these components of cyber hygiene:
- Systems and databases need to be monitored.
- User access needs to be managed.
- The most sensitive and important data needs special care and extra protection barriers.
A couple options here are the use of SOAR solutions and SIEM solutions:
- Security orchestration, automation and response (SOAR) solutions enable organizations to efficiently observe, understand, decide and act upon incidents from a single interface.
- Security information and event management (SIEM) solutions offer a streamlined view of data, security activities and operational capabilities, allowing you to effectively detect, investigate and response to security threats.
As both do work that is impossible to tackle manually, many organizations deploy both side by side, further increasing resilience against increasingly sophisticated security threats.
(See what Splunk SOAR & Splunk Enterprise Security can do for your organization.)

The relationship between security compliance and cyber hygiene
Proper cyber hygiene practices keep organizations ahead of security threats by following standard regulatory practices. This ensures that organizations understand and enforce regulatory policies. Cyber hygiene practices include scanning the organization's infrastructure to check for vulnerable loopholes and inconsistencies in compliance with regulatory policies.
This is very important in checking whether an organization's framework complies with standard regulations.
Applying proper cyber hygiene practices ensures that an organization stays in line with legal practices while handling data. This reduces the risks of legal actions from customers.
(Related reading: learn how to navigate SecOps compliance with this blueprint for success.)
Cyber hygiene services from CISA
In the U.S., the Cyber Security and Infrastructure Agency (CISA) provides free cyber hygiene services to certain organizations, including U.S.-based federal, state, local, tribal and territorial governments, as well as public and private sector critical infrastructure organizations are welcome to enroll. Some international organizations may be eligible as well.
As part of this offering, organizations can get help with vulnerability scanning and application scanning, that "uncover vulnerabilities and misconfigurations that attackers could exploit", including but certainly not limited to vulnerabilities listed in the OWASP Top Ten.
Enroll and learn more about cyber hygiene services from CISA.
Cyber hygiene best practices for organizations
So, cyber hygiene is a way of structure your cybersecurity strategy. Let’s look at best practices that organizations of all sizes should follow.
1. Implement a strong automated backup system
The first attitude that IT managers need to have cyber hygiene is to ensure that, even if something happens, the company will not lose work or important information for its operations. With the increasing importance of IT, data risks, and market dynamism, a manual backup routine is no longer enough for a secure business. Look for automated alternatives like good cloud services. This can lighten your work and still free up time for the team.
2. Practice risk management
What happens if someone breaks into the company and manages to compromise sensitive data? How would IT react in this case? What are the containment plans? When should they be applied?
These and other questions are part of good risk management — when the technology team prepares for break-in and outage scenarios and creates plans to respond. Risks will always exist, and you need to know them well.
3. Control access
As in the hospital example, much of the control problems over who is in the corridors starts at the reception area. Access control is one of the biggest barriers to data protection, so invest heavily in this area. Look for services and tools that automate authentication and monitoring and that also alert you when there are anomalies when trying to enter the system. This enables two important things:
- It significantly reduces the chance that the company will be compromised.
- It is much easier to identify the cause and origin of possible leaks.
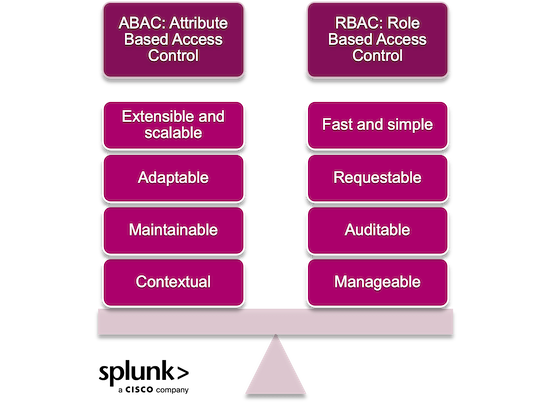
Popular concepts for access control include RBAC, role-based access control, or ABAC, attribute-based access control.
4. Control the use of administrative privileges
Once in possession of a credential with administrative privileges, the attacker will be able to walk through the entire environment in a calm and silent way, leaving few traces along the way. Remember, security is not provided by a single solution or measure in isolation. In this sense, the exposure of privileged credentials can be a vulnerability resulting from the absence of certain measures.
It's not uncommon to see companies granting administrative privileges without an adequate process in place. Instead, consider a practice of least privilege access, which will:
- Assess the need.
- Determine the validity period
- Implement multiple authentication factors.
There's also the necessity to revoke the credential in case the user no longer works for the company or a particular person doesn't need administrative privileges anymore. These types of requests have to be very timely, so you have to ensure you have the people and/or mechanisms in place to revoke privilege at any point.
5. Continuously manage vulnerabilities
We need to perform scans to identify vulnerabilities on a recurring basis in the shortest possible interval, considering the capacity of the resources — which will manage these vulnerabilities — and the internal processes for carrying out the respective treatment. This process will minimize the surface exposed to services and applications as much as possible.
In a mature environment, we need to combine the automated vulnerability management process with a more thorough and manual analysis process involving mainly critical systems and conducted by a team of penetration testing specialists.
(See how vulnerabilities are the starting point for cyberattacks and kill chains.)
6. Secure hardware & software
Most information technology solutions, whether hardware or software, are provided by default with an initial configuration that prioritizes simplicity and practicality in the deployment process. In this sense, it's common for these solutions to come with modules and excessive services enabled and with security levels in basic or nonexistent authentication and communication protocols.
This process is commonly called hardening and consists of deactivating any enabled resource that's useless for the purpose of the service, in addition to raising the security levels of authentication and encryption mechanisms without even degrading performance or functional requirements.
7. Monitor, analyze and audit logs
Logs are extremely important, both in the incident identification process and in the forensic investigation process. However, for this information to deliver the benefits that we need, it first needs to exist, and then we need to read it.
For some years now, we've understood that the main challenge of the strategy and security measures implemented is no longer preventing cyber criminals from entering the perimeter — but rather identifying and neutralizing the attack vector in the shortest possible response time. Properly implemented mechanisms should isolate and limit the internal movement of the threat, minimizing the impact of the attack as much as possible.
However, just producing logs is not enough. The next step will be to ensure that we analyze them regularly in order to identify patterns of behavior or anomalous activities. According to the size of the environment and the number of assets, we understand that a nonautomated analysis of this information will soon become unfeasible. In this case, the implementation of storage, analysis and correlation solutions for these records will be essential.
According to Tina Williams-Koroma, cybersecurity expert and founder of TCecure, some of the most important cyber hygiene best practices include:
- Know what's in your organization (inventory). You can't secure what you don't know exists. Start with asset discovery.
- Know your security requirements. Who are your customers, what security and privacy requirements need to be in place to properly protect that data?
- Run compliance/configuration scans based on customer security requirements to understand technical gaps, and fix those gaps (test the fixes first).
- Patch early and often. Test patches first to ensure no adverse operational impact.
- Install and schedule antivirus updates, to run daily, and address any flags.
- Run vulnerability scans at least monthly to identify any new/missing patches that may be needed.
Meanwhile, common mistakes include:
- Not testing updates/patches prior to rolling them out to the production environment
- Not understanding that hackers and adversaries get informed about new patches and vulnerabilities as soon as legitimate organizations do. They start developing exploits to take advantage of organizations who don't keep up with their hygiene; organizations often take far too long to make updates, thinking they won't be a target. (You will.)
Cyber hygiene best practices for individuals
Of course, cyber hygiene doesn’t stop or start with organizations. Individuals also play a major role in maintaining the security of your organization. Here’s some tips that organizations can help promote to employees, partners, customers and others in your influence.
Use strong passwords
When creating a password, avoid short words and very simple numbers, such as your first and last name, license plate, or birthday, as these are easy combinations to be hacked. Use uppercase and lowercase letters, as well as symbols, to create a strong, more elaborate password with elements that make it difficult to disclose.
The truly best practice here is to use a password manager like LastPass or Dashlane. These easy-to-use apps generate, store and encrypt your passwords so that you only have to remember a master password to access your dozens (or hundreds!) of other passwords.
Change passwords frequently
Your data may be at risk if you use the same password across several websites or services. If a keyword is hacked, criminals will look for other accounts of that same user. So change your credentials regularly — which is exactly what a password management tool can help you do.
Do not open suspicious emails
Got a strange email from your bank? Don't open the message, as you may be the target of a phishing scam. Criminals can gain access to your information and even use your computer to break into your company's internal network.
Avoid downloads from unknown sources
Software is often the target of viruses and scams by internet criminals. Avoid downloading these software as much as possible, as they can steal data and passwords from your computer. This also applies to browser extensions (applications that add extra functions to programs). Check user ratings and comments about the app before downloading.
Cyber hygiene best practices for small businesses
According to cybersecurity & social engineering expert and mentalist Gary S. Chan, these are the basic considerations for small business cyber hygiene:
- Back up your data.
- Know your legal obligations.
- Establish cyber policies.
- Grant limited access rights.
- Provide training to employees.
- User multi-factor authentication (MFA).
- Use next-generation endpoint security software.
- Update and patch software and systems.
- Implement email security.
- Manage mobile devices.
- Secure Wi-Fi.
- Establish policies.
Want to learn more about mentalism and social engineering? Check out Gary's keynote speech from the Gateway to Innovation Conference below.
Cyber hygiene is just the beginning
Obviously, a properly designed security program covers many additional points in addition to those mentioned. Cyber hygiene only recommends measures classified as technical and is not part of the scope of the concept. For example, the design and implementation of physical or administrative measures are also essential for the consolidation of an adequate security posture.
A good information security program must be comprehensive, integrated and optimized and not restricted to a specific group or category of solutions.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




