The Caesar Cipher, Explained

Around 58 BCE, Julius Caesar used a special technique in his military campaigns to make it difficult for his enemies to understand his commands. He did this by shifting each letter in his commands.
The enemy had to make an extra effort to intercept and decipher what the command meant.
This was the first-ever reported substitution cipher used in the world. Later, this technique became more popular as an encryption method and was named the Caesar Cipher as a tribute to its inventor.
In this article, we'll discuss what it is, how it works, its features, rules, pros, cons, and useful tips for breaking a Caesar Cipher.
What is Caesar cipher?
The Caesar Cipher is one of the oldest encryption techniques used to communicate securely with different parties. The most widely used name is Caesar Cipher, though some people may call it Caesar's cipher, the shift cipher, Caesar's code, or the Caesar shift.
In the Caesar Cipher, letters in plain text are replaced by other letters or symbols by shifting them a fixed number of positions in the alphabet. This is why the Caesar Cipher is sub-categorized as a substitution technique.
This is the earliest known and simplest method of encryption, used by Julius Caesar and followed by many other military leaders to protect their communications during military operations.
Caesar preferred a shift of three, but today, a common use of the Caesar Cipher is called "ROT13." This stands for "rotate by 13 places," which means moving each letter of the alphabet 13 spots forward.
Importantly, this technique is not widely used today — that’s because it is easy to break. We will discuss why in the latter part of the article.
(Related reading: end-to-end encryption.)
Caesar Cipher & cryptography
Due to its simplicity and ease of use, Caesar cipher created the foundation for modern cryptographic techniques.
The Caesar Cipher introduced the idea of substituting one letter for another — a basic but important principle in cryptography. Its simplicity really laid the foundation for creating more advanced and secure encryption methods.
People often use the Caesar Cipher in various educational programs to teach encryption and decryption basics. This can be a great kick-off for people to understand more complex topics like:
- Substitution ciphers
- Transposition ciphers
The idea of a fixed shift in the Caesar Cipher eventually evolved into more sophisticated techniques, like the Vigenère cipher, which uses a variable shift based on a keyword. This shift from a simple fixed method to a more complex variable one shows how cryptographic methods have advanced to meet the need for better security.
(Explore common encryption standards: Triple DES, AES, and homomorphic encryption.)
How Caesar cipher works
To cipher a given text, we need an integer value, known as a shift. The shift indicates the number of spots each letter of the text has been moved down. The encryption can be represented using modular arithmetic by first transforming the letters into numbers, according to the scheme:
- A = 0
- B = 1
- C = 2
- …
- Z = 25
Encryption of a letter by a shift 𝑛 is shown here:
En(x)=(x+n)mod26 (Encryption Phase with shift 𝑛)
Dn(x)=(x−n)mod26 (Decryption Phase with shift 𝑛)
Let us further understand how Caesar's Cipher works with a very simple example.
Example
Imagine David and Nora want to communicate using Caesar's Cipher method. First, they should decide on a shift to use. Let’s say that they picked three as the shift. So, to encrypt her message David needs to apply a shift of three to each letter in his message.
That means A will become D, and B will become E. It will continue like that. This unrecognizable or encrypted message is now sent to Nora.
To decrypt the message, Nora needs to subtract three from each letter in the received message to read the original message.
- Original message David wants to send to Nora: Call me Tomorrow
- How it looks once Caesar Cipher applied to the message: Fdoo ph Wrpruurz
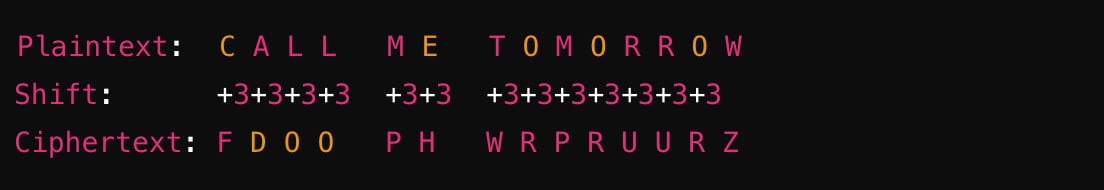
What happens when the shift exceeds 26 in Caeser Cipher?
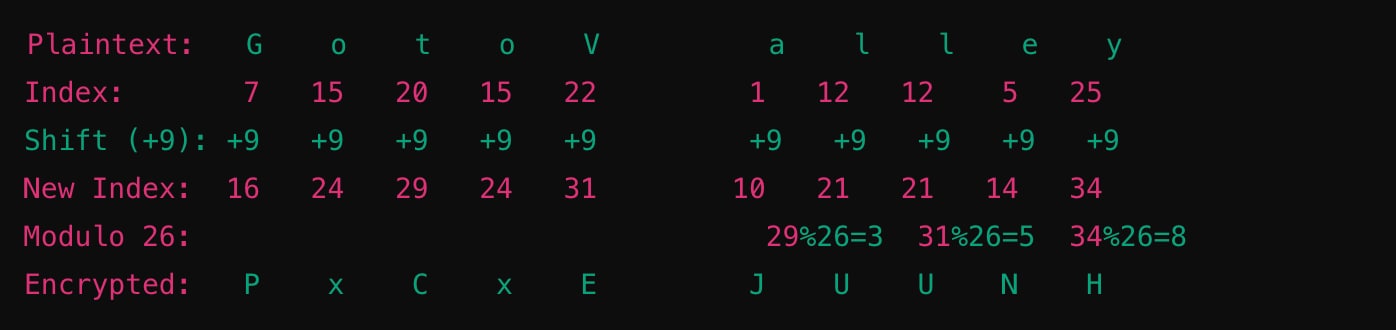
Let's encrypt the phrase "Go to Valley" using the Caesar Cipher with a key of 9.
When you add the shift to the letter's index and the result exceeds 26, you should take the modulo 26 of the result to wrap around within the alphabet.
- G is the 7th letter. Adding 9, we get 16. The 16th letter is P.
- O is the 15th letter. Adding 9, we get 24. The 24th letter in the English alphabet is x.
- T is the 20th letter. Adding 9, we get 29. Since 29 exceeds the alphabet range, we take modulo 26 (29 - 26 = 3). The 3rd letter is C.
- O is the 15th letter. Adding 9, we get 24. The 24th letter in the English alphabet is x.
- V is the 22nd letter in the English alphabet. Adding 9, we get 31. Since 31 exceeds the alphabet range, we take modulo 26 (31 % 26 = 5). The 5th letter is E.
- A is the 1st letter. Adding 9, we get 10. The 10th letter is J.
- L is the 12th letter. Adding 9, we get 21. The 21st letter is U.
- L is the 12th letter. Adding 9, we get 21. The 21st letter is U.
- E is the 5th letter. Adding 9, we get 14. The 14th letter is N.
- Y is the 25th letter. Adding 9, we get 34. Since 34 exceeds the alphabet range, we take modulo 26 (34 % 26 = 8). The 8th letter is H.
Once complete, the encrypted message is: Px Cx EJUUNH
Caesar cipher features
It's important to understand the features of the Caesar Cipher so people can evaluate the technique and decide whether it is suitable for their needs or if they should consider an alternative solution.
The Caesar cipher replaces each letter in the message with another letter a fixed number of positions down the alphabet. Therefore, it falls under the category of substitution cipher. Here are the primary features of this cipher:
- It uses a fixed key. We call this a shift as well. This key/shift is the number of positions each letter is shifted. Both the sender and receiver know this key.
- Due to its simplicity, the Caesar cipher is often used as a teaching tool to introduce basic concepts of cryptography.
- The Caesar cipher is symmetric. That means it uses the same key for encoding by the sender and decoding by the receiver.
- The English alphabet has only 26 letters. Therefore, in this method, you can use only 26 possible keys. This limits the keyspace.
- Because there are only 26 possible keys, it's easy for attackers to try all options and break the cipher.
- While not suitable for serious security needs, the Caesar cipher can add a basic level of security to messages.
- The Caesar cipher is simple to use. It only needs basic arithmetic, making it popular as a simple encryption method.
Pros & cons of Caesar cipher
| Pros | Cons |
Very easy to design, implement, and use. Can be easily modified to create more secure versions by using multiple shifts or keywords. Requires minimal pre-shared information. It is great for beginners to learn encryption.
| Not secure against modern decryption techniques. Vulnerable to known-plaintext attacks where both the encrypted and plaintext versions are available. A limited number of possible keys. So it's easily susceptible to brute force attacks. Not suitable for encrypting long texts due to ease of cracking. Ineffective for secure communication as it can be easily broken. No message confidentiality, integrity, and authenticity. |
Useful strategies to break a Caesar cipher
Breaking a Caesar Cipher, despite its simplicity, requires some strategic thinking. It's important to identify what are the effective strategies one can use to decode a message encrypted with a Caesar Cipher.
Each method has its own strengths, and the best one to use often depends on the length and nature of the message.
Brute force attack
A brute force attack is the most common method to break a Caesar Cipher. In this approach, you try each possible shift from 1 to 25 until you get a meaningful message. Caesar Cipher has only 26 possible shifts. Therefore this method is guaranteed to find the correct one eventually.
When to use: Especially useful for short messages, as it doesn’t take much time to go through all the possibilities when you program it.
Frequency analysis
Frequency analysis means that certain letters appear more frequently in natural language texts. For example, in English, the letter 'E' is the most common. By comparing the frequency of letters in the encrypted message to the typical frequency of letters in English, you can guess the shift used in the cipher.
When to use: This method works best with longer texts, where the letter frequency distribution is more evident.
Crib dragging
Crib dragging involves using known or suspected words or phrases within the ciphertext to find the shift value.
For example, if you suspect that the word "the" appears in the message, you can align it with various parts of the ciphertext until it gives a proper meaning. Once you find a match, you can guess the shift and decrypt the entire message.
When to use: This technique is helpful when you have some idea about the content of the message.
Known plaintext attack
A known plaintext attack can be very effective if you have access to some of the original plaintext along with the encrypted message. By comparing the plaintext with the ciphertext, you can easily determine the shift value used.
When to use: This method is easy to use and quick since it uses the direct relationship between the known and encrypted texts to break the cipher.
Is the Caesar cipher dead?
With the advancement of technology, techniques like the Caesar Cipher and ROT13 are not practical for serious encryption. You can easily find tools online to crack these ciphers just by copying and pasting the encrypted text.
There are still some applications of Caesar cipher as a part of more complex schemes. Other than that, the most common use of these ciphers is for educational purposes, helping beginners understand the basics of encryption and security.
Among various cipher types, monoalphabetic substitution ciphers have been easy to crack during the past hundreds of years. Especially with modern software, breaking them is very simple. Despite this, they still have their place in puzzle solving for fun and as time-killing exercises, much like sudoku puzzles. Sometimes, they are used as exercises for more complex cryptographic challenges. So, while the Caesar Cipher isn’t dead, it’s not used for serious encryption today.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.




