What Is Vulnerability Management?

Every system has vulnerabilities. Do you know where yours are?
These weak spots are prime targets for threat actors. Adapting a vulnerability management process can help.
Vulnerability management is the ongoing practice of managing vulnerabilities in your IT systems. An important pillar of cybersecurity, vulnerability management is a critical part of any organization that's even halfway serious about protecting its assets. So, in this article, let’s take a long look at vulnerability management, including:
- How to manage vulnerabilities
- The benefits and challenges
- Best practices to adopt
Let’s get started with understanding vulnerabilities.
Learn about Using Splunk for Vulnerability Management ›
What are vulnerabilities?
A vulnerability is any weakness or flaw within a system. These weaknesses can make your organization vulnerable to unknown activities, including the big one: threat actors.
These weak spots are opportunities for attackers or unauthorized personnel to take advantage and access your systems in order to:
- Steal sensitive data.
- Damage the system network.
- Deny authorized users access to use the product.
To reduce the threat from these vulnerabilities, your network and system administrators are on the front line, patching software and operating systems, strengthening the weak spots. But a manual approach is no longer sufficient, as we’ll soon see.
(Understand how vulnerabilities, threats and risk all play a part.)

Examples of vulnerabilities
There are many types of vulnerabilities. Here are a few examples of vulnerabilities you might find in the wild:
- Unpatched software
- Unsecured APIs
- Weak credentials
- Programming bugs
- Misconfigurations
- URL redirection to unsecured websites, often via phishing or social engineering
- Uploads of dangerous and unsecured files
- Insider threats
A prime example of a notorious vulnerability is the Log4j zero-day vulnerabilities that occurred in late 2021.
Known vs. unknown vulnerabilities
Vulnerability management addresses the vulnerabilities that you can know. Still, there will always be unknown vulnerabilities: things you cannot know until or unless an incident makes them apparent.
For known vulnerabilities, explore the Common Vulnerabilities & Exploits list, known as the CVE. Maintained by The MITRE Corporation, the CVE is “a publicly available list of frequently occurring information security vulnerabilities and exposures”.
(Sound familiar? You may have heard of MITRE ATT&CK and its companion MITRE D3FEND.)
What is Vulnerability Management?
Vulnerability management is a continuous practice to identify, mitigate, and report on vulnerabilities that pose a risk to your organization. Without this security practice, weaknesses in your system may go unnoticed — until it’s too late.
The goal of vulnerability management is to be proactively in order to reduce the risk of exploitation by cyberattackers and to protect sensitive and critical data and systems.
Vulnerability management involves several tasks, such as:
- Continuously monitoring production environments for vulnerabilities.
- Conducting risk assessments.
- Prioritizing issues.
- Implementing remediation measures like patching and hardening for issue mitigation.
Many software tools are available for organizations to automate those tasks and quickly identify and remediate the highest-impact vulnerabilities. (More on this later.)
With the rise in cloud-native development, you’ll also hear the term application vulnerability management.
The importance of managing vulnerabilities
Enterprise software applications are sophisticated. Any security vulnerability in software components can bring severe consequences to the organization.
That’s why it is critical to effectively manage application vulnerabilities. Additional considerations explain the pressure to mitigate your weak spots:
- The increased usage of different software architectures, cloud environments, and integrations with third-party systems has significantly heightened the risks of security vulnerabilities in software applications.
- Any disruptions to enterprise applications resulting from exploited vulnerabilities can lead to application downtimes.
- The costs related to data breaches, reputation harm, or legal penalties? Substantial.
(Related reading: the cost of downtime & third-party risk management.)
Vulnerability management lifecycle: 6 phases
Let’s get one thing straight: many organizations follow their own vulnerability management frameworks (and recommend them to others). Each has some variation of the stages below, sometimes in a different order, sometimes with fewer or additional phases.
The important thing to know is that managing vulnerabilities is an ongoing practice — not a one-time process — that requires discipline and the understanding that new threats emerge every day: Continuous assessment and discovery are paramount.
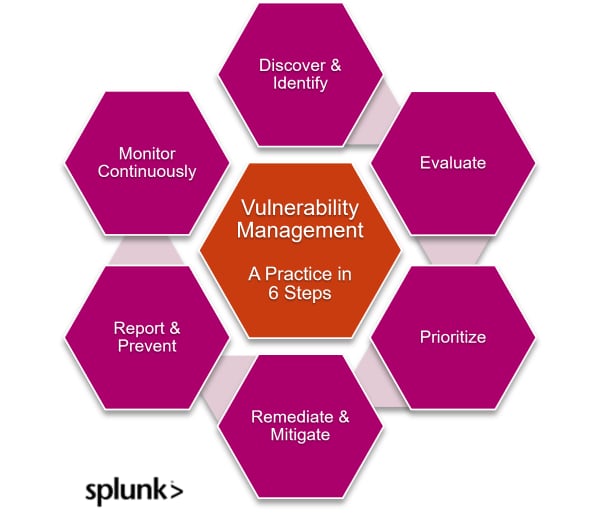
The following is a comprehensive approach that breaks down the management process into digestible yet thorough phases.
Phase 1. Discover & Identify
You can't fix a vulnerability if you don't know it exists. That’s why you’ll start with creating an asset inventory and then identifying vulnerabilities.
You can use a variety of tools for asset and application discovery, including network monitoring and agent-based discovery. To start your asset inventory, think about:
- Physical assets, such as network devices
- Digital assets, such as web applications
- Information assets, such as financial information
Next, to identify vulnerabilities, your team can use vulnerability scanning, operating system (OS) scans, data scans, and endpoint security assessments. You’ll want to scan everything — files, apps, devices, you name it.
A variety of tools, including Splunk, can make this process easier, aiming to identify vulnerabilities, and the most threatening of them, to prevent security breaches. Solutions like this generally rely on technologies including:
- Advanced security analytics
- Machine learning
- Threat intelligence
Identification is the foundation for all vulnerability management, so don’t skimp here.
Phase 2. Evaluate
After identifying existing vulnerabilities in your system, you’ll want to determine their severity — how bad is the threat from each vulnerability, if it were exploited?
Vulnerabilities can be ranked using the Common Vulnerability Scoring System (CVSS), which evaluates each vulnerability based on exploitability, impact, remediation level, and other factors. The CVSS scores vulnerability severities as follow:
- Low (0–3.9)
- Medium (4–6.9)
- High (7–10)
However, this is just a starting point. You and your team must consider the risk as it pertains to your specific organization.
(Don’t confuse vulnerability scoring with incident severity levels: these are two different things,)
Phase 3. Prioritize
Based on the severity levels and potential impact determined in the evaluation phase, make a plan for which you’ll address first.
This process is unique to each organization — a vulnerability that may have a significant negative impact on one business may be small potatoes to another. Some things to think about:
- What’s the likelihood that a vulnerability will be exploited?
- What’s the potential business impact of a particular vulnerability being exploited?
- Could a particular vulnerability lead to serious non-compliance issues?
Important in this phase is to consider what risks you are willing to accept. For example, certain vulnerabilities may be very unlikely to be acted upon. Or, the consequence of an exploited vulnerability may be minimal or even zero.
(Related reading: risk appetite vs. risk tolerance.)
Phase 4. Remediate & Mitigate
Now it’s time to action on your prioritized plans: get rid of the vulnerabilities that pose the biggest risk to your organization. How? Fixes may include:
- Security patches
- Reconfiguration
- Hardware or software replacements
- New processes
Whichever method, the end goal is the same: ensuring that the system is as risk-free as the organization is willing to accept. (It’s impossible to eliminate all risk entirely for eternity.)
Phase 5. Report & Prevent
When the appropriate fixes have been made, document your findings, mitigation strategies, and your updated security plan for future prevention. Outcomes here may include:
- A better, wider understanding of internal systems so that teams can better design software, apps, and network solutions.
- An approach to complying with regulations and requirements that’s easier than before.
Phase 6. Verify & Monitor Continuously
Finally, verify that your fixes were successful. Monitor continuously to prevent future vulnerabilities from slipping through the cracks.
Let’s pause here to talk about continuous monitoring and scanning: these are the only ways to detect vulnerabilities as soon as they emerge. Security teams can monitor network traffic and application logs to identify suspicious activities and respond promptly to security incidents. To identify security weaknesses, these tools can:
- Scan the entire application environment in real time.
- Analyze the application code, configurations, and dependencies.
With the increasing use of containerized applications, these tools can also scan and identify vulnerabilities in containerized applications.
Continuous monitoring assists in identifying misconfigurations — open ports and weak access controls — and addresses them to mitigate the risks of exploitation. This early detection enables proactive measures we’ve already covered: patching, configuration changes, and security controls.
Managing vulnerabilities: Pros & cons
Embracing an ongoing vulnerability management process is an important element of a proactive approach to cybersecurity. To state the obvious: it only takes one vulnerability for bad actors to slither in and wreak havoc.
Benefits of robust vulnerability management
- Improve the organizations’ overall security posture. The regular monitoring and scanning means you can proactively identify and address security weaknesses before attackers can exploit them. You’re equally keeping systems updated and protected and you’re reducing overall risk. That’s a strong security posture.
- Return to normal, quickly. Vulnerability management improves the efficiency of incident response and event management. Put simply: you’ll reduce time spent dealing with incidents and get back to normal fast.
- Save costs. Security breaches are costly. Reputational damages can be even worse. With proper vulnerability management, organizations can avoid such costly damages and legal penalties.
- Keeps customers happy. Customers who know your organization takes security seriously will be more confident in using your services.
- Comply with regulations and standards. Many organizations must meet certain cybersecurity and privacy regulations related to enterprise applications.
(Related reading: GRC governance, risk, compliance.)
Challenges of vulnerability management
Of course, there are many challenges in implementing vulnerability management solutions. Let’s discuss some of them.
Inadequate asset inventory. The biggest challenge organization face is their own poor or incomplete understanding of assets and apps. Organizations that make use of spreadsheets or some other obsolete method to store data often get an inaccurate or incomplete results.
Prioritization & manual workflows. Teams struggle to prioritize which vulnerabilities present the most risk. Manual work to prioritize each one does not suffice.
Hazy, unclear framework for employees. Companies with an unclear organizational structure struggle to manage vulnerabilities: how do they know who is responsible for what?
Vulnerability management best practices
Effective vulnerability management involves implementing and performing several key tasks. The following are the best practices you can follow for effective vulnerability management.
Keep software updated
Enterprise applications rely heavily on third-party libraries and tools. That means you must stay up-to-date and patch your applications as soon as updates are available. These software updates routinely include fixes for security-related issues and known vulnerabilities.
Have an incident response plan
Remediation is a key step in vulnerability management. Hence, organizations must establish a comprehensive incident response plan to address issues related to application vulnerabilities.
Create a well-defined incident response plan that outlines the appropriate actions to take in response to various security incidents. With a well-defined incident response plan, organizations can:
- Minimize the impact of application vulnerabilities and security incidents.
- Mitigate potential exploits by promptly identifying and resolving vulnerabilities, thereby reducing the likelihood of successful attack execution.
Fold security into the earliest stages of development
Incorporating security into the early stages of application development requires integrating vulnerability testing into the CI/CD pipeline. By considering security from the start, known as shifting left, developers can proactively detect and resolve potential vulnerabilities during the development phase.
This shift left approach should also include threat modeling. Modeling threats helps you identify the sections of an application that handle sensitive information, so developers can give those areas extra attention.
Train, educate employees and partners
Appropriate and regular education and training helps familiarize your developer and security teams with the right information, so they can minimize coding vulnerabilities and develop applications with those vulnerabilities in mind. For instance:
- When developers understand how cross-site scripting (XSS) or SQL injection works, they can take measures to address security concerns during the development process.
- Quality assurance (QA) engineers can design and execute tests targeting application vulnerabilities. This helps identify vulnerabilities early in the software development life cycle, allowing for timely remediation.
Leverage threat intelligence
Threat Intelligence provides up-to-date and relevant information about potential risks and helps prioritize vulnerabilities. This enables organizations in two important ways:
- You can proactively apply patches to mitigate threats based on the global threat landscape.
- You can prioritize and address the most critical vulnerabilities first, reducing the overall risk exposure.
Also, Threat Intelligence helps organizations understand the tactics, techniques, and procedures (TTPs) cybercriminals use. By understanding the TTPs, organizations can implement appropriate security measures to safeguard their applications. This knowledge enables proactive defense strategies.
Choose the right vulnerability management solutions
Tools and “solutions” for vulnerability management are plentiful, ranging in price point and features.
The biggest factor is whether a given solution works within your existing systems and processes. The right tool for a small business might not be the right tool for a larger one. Therefore, it’s important to understand your organization's needs before deciding what to use.
Splunk SOAR is a security orchestration, automation, and response (SOAR) tool that comprehensively manages the end-to-end vulnerability management process. Easily navigated within a single platform, Splunk SOAR’s capabilities include:
- Automating vulnerability prioritization
- Generating remediation tickets
- Monitoring the remediation progress
Security teams can effectively perform vulnerability management tasks — and empower your entire SOC — by leveraging Splunk SOAR.
(Try Splunk SOAR for free or take a guided tour.)
Vulnerability management is not a one-time process
Vulnerability management is an important investment that organizations must make to prevent breaches and cyberattacks.
An Expert's Perspective
 To better understand the finer points of vulnerability management, we spoke with Andrew Plato, author of The Founder’s User Manual, an experienced pioneer in cybersecurity and founder of Zenaciti.
To better understand the finer points of vulnerability management, we spoke with Andrew Plato, author of The Founder’s User Manual, an experienced pioneer in cybersecurity and founder of Zenaciti.
In this section, we've included Andrew's responses to our prompts.
What are some of the vulnerability management pitfalls to avoid?
The most significant pitfall to avoid in Vulnerability Management is taking a piecemeal approach to resolutions. It is not uncommon for vulnerability scanning to reveal hundreds, even thousands of vulnerabilities in an environment. Almost all vulnerabilities can be quickly and easily remediated with patching and configuration changes. As such, organizations must take a systemic approach to remediation. Patching and configuration management should be automated such that IT administrators can quickly push updates to all systems.
Second, the tool you use is far less important that the processes you implement. I watched countless companies scan their environments, uncover thousands of vulnerabilities, and then do nothing because they failed to assign anybody to work on the remediation. Buying a vulnerability scanner without assigning resources to manage, monitor, and remediate findings is largely a waste of money.
Simple scans are usually insufficient to uncover problems. Scanning must be authenticated, which is more difficult to set, but provides much more insight into the overall health of the environment.
What are some of the latest trends in vulnerability management?
The most significant trend in vulnerability management is that the technology is slowly being incorporated into other platforms. Microsoft Azure and Office 365 (with the correct licensing) provide integrated vulnerability management. AWS Config and Inspector perform a similar function. Wiz has vulnerability management built into the platform. There is no excuse not to have a vulnerability scanner these days since they are rapidly becoming a commoditized technology.
Lastly, while you can outsource vulnerability scanning and reporting to a managed security provider, it is a whole different ballgame to remediate the findings. Most managed security providers lack the manpower, access, or tools to remediate your environment. Remediation is often a lot more expensive than simple monitoring. Pay attention to this detail when looking for a managed security provider.
See an error or have a suggestion? Please let us know by emailing splunkblogs@cisco.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.





