AppSec Today: Application Security Requirements & Guidelines To Know

Modern applications are sophisticated — and complicated! Different third-party software, various hardware components, complex and distributed integrations. Unfortunately, these complications also complicate your security posture: now, there are a lot more exploitable vulnerabilities in the application layer.
That means application security is one of the most critical aspects organizations should focus on to secure their business operations, from cybercrime and cyberattacks.
Ensuring application security is not just about protecting data. It’s about safeguarding your company's reputation, keeping customer trust, and adhering to increasingly stringent regulatory requirements.
In this comprehensive article, we’re covering a lot of territory:
- The concept of application security & its growing significance
- The most pressing application vulnerabilities and threats
- State of AppSec today
- Critical security requirements your application needs to meet
- Actionable AppSec techniques
- Best practices to adopt to achieve robust application security.
What is “AppSec”? Application security defined
Often known as AppSec, application security is the practice of applying best practices, processes, and tools at the application layer to mitigate threats from exploitable vulnerabilities. Instead of waiting until you deploy applications to production, AppSec focuses on building secure mobile, web and cloud applications throughout their development lifecycle, from start to finish.
AppSec is a proactive approach to security that helps prevent threats at the initial stages — rather than a reactive or defensive catch-up approach.
Adequate security procedures must apply from the initial stage of the application development and continue while the application is in production like automated security scanning. AppSec is (and should be) a continuous process that aims to be as defensive as possible against ever-changing cyber threats.
The growing significance of AppSec
There are two truths in business operations today:
- Cyber threats continue to evolve at alarming rates.
- Your organization uses more diverse software and applications than ever before.
Emerging cybercrime techniques can breach the most secure software applications. (As secure as anything can get, that is.) Even a small vulnerability, like a configuration issue, can lead to a huge data breach if not identified at the beginning of the development.
Now, add in the fact that the majority of apps are cloud native. That isn’t helping, according to research: organizations that adopted cloud-native environments are 4x more likely to have increased concerns — not decreased — over their security posture.
Organizations must incorporate security not only at the network level and at the application level, but in all stages of the development process. It helps to reveal vulnerabilities from the beginning and apply the necessary security control before it could become a series threat to the organization.

The state of application security today
The current state of application security reveals why companies have to maintain continuous vigilance and adaptation today. Here are the key forces driving change in application security today:
Inherited vulnerabilities: Experts identified over 35,000 vulnerabilities in 2024 (and that's before December). These vulnerabilities are not all introduced in the coding process. Instead, plenty are inherited from libraries, frameworks, and other components used to build an application.
Applications are only secure as their weakest links, and if they’re built using components with security flaws, they’ll be vulnerable.
Widespread attacks with serious, real-world impact: The Log4Shell vulnerability is a critical example of the incredible impact of widespread attacks on application security. Exploit flaws in widely used libraries allow attackers to execute arbitrary code on affected systems.
Third-party vulnerabilities: Most applications today rely heavily on third-party services for critical functions. While these services enhance functionality, they introduce vulnerabilities. Many attackers today exploit third-party services to gain unauthorized access to applications.
Attacks on every aspect: The OWASP Top 10 demonstrates the diversity of vulnerabilities that impacts AppSec today. It highlights how any aspect of an application can be targeted, including:
- Misconfigured security settings
- Injection flaws
- Cross-site scripting
- Insecure direct object references
This necessitates a comprehensive approach to application security, covering all aspects from input validation to session management and error handling.
All these threats in the modern application security landscape underscore the importance of a multi-faceted approach to application security. IT and security teams must go beyond securing individual applications — instead, they must scrutinize the broader ecosystem of frameworks, libraries, and third-party services to mitigate risk.
Legal & regulatory compliance
Cybercrime is not the only reason driving AppSec. In fact, countless regulations and all sorts of compliance are critical for your business, too. It’s vital to understand which regulations apply to your business based on your location, industry, and the data types you handle to ensure your applications are compliant.
Here are some very common regulations, among many:
General Data Protection Regulation (GDPR). This regulation enacted by the European Union (EU) governs the collection, storage, and use of the personal data of EU citizens. It applies regardless of where the data processing occurs and requires businesses to:
- Protect personal data.
- Implement appropriate security measures to prevent data breaches.
California Consumer Privacy Act. The CCPA gives California residents more control over their data. Businesses must disclose the personal data they collect, what it’s used for, and if they sell it. Consumers have the right to request that their data be deleted.
Health Insurance Portability and Accountability Act. HIPAA sets the regulations for the disclosure and use of Protected Health Information by healthcare providers, health plans, and other entities in the United States. It requires various security measures to protect data, including access controls, data encryption, and regular audits.
Financial regulations. There are numerous regulations governing the financial industry.
- In the US, the Gramm-Leach-Billey Act (GLBA) regulates financial institutions and requires them to explain their information-sharing practices to customers and safeguard private data.
- The Second Payment Services Directive (PSD2) in the EU influences how payment service providers handle secure payments and customer data.
Prominent application security risks to understand
OK, now with the atmosphere set for why you need application security, let’s now take a look at the risks you may be running.
There are plenty of ways to identify risks. The Open Web Application Security Project (OWASP) describes web application software's top vulnerabilities, especially the OWASP Top 10 and the new Top 10 for LLMs and GenAI.
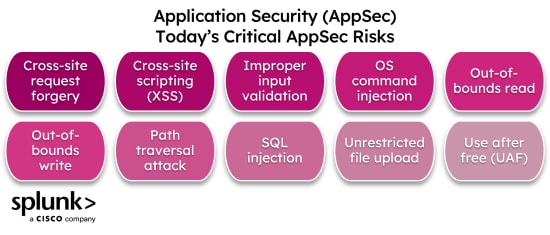
The Common Weakness Enumeration (CWE) lists the top 25 most dangerous software weaknesses, which helps developers identify what vulnerabilities they should focus on. According to the CWE, the following are the most critical application security risks you can find in software today.
- Out-of-bounds write. Writing to a memory that exceeds the buffer boundary. For example, writing to an array past its highest index. This can introduce application crashes, data corruption and malicious code execution.
- Cross-site scripting (XSS). Attackers exploit a web application to inject malicious scripts into a safe website through a client-side script.
- SQL injection. An attack that exploits weaknesses in SQL queries and gains access to application databases. These attacks could allow attackers to execute DB operations in the database, resulting in sensitive data breaches.
- Improper input validation. A vulnerability that occurs with inputs not properly validated. This vulnerability allows attackers to enter potentially dangerous inputs.
- Out-of-bounds read. Applications allow reading before and after the buffer's boundary, causing the application to crash or allowing attackers to read sensitive data in memory.
- OS command injection. Weakness in the web application that enables attackers to execute commands in the operating system. This attack can exploit your data and other hosting infrastructure.
- Use after free (UAF). This happens when the program fails to clear the pointer to the memory location after freeing the space. This dynamic-memory-related vulnerability lets attackers use these dangling pointers to execute arbitrary code.
- Path traversal attack. This allows attackers to access files and directories outside the root folder. It can expose critical files like application source code and configuration files.
- Cross-site request forgery (CSRF). Tricking users into doing unauthorized actions on a website they have access to and are authenticated. For example, tricking users into changing the password, email address, fund transfer, etc. For this, attackers can use social engineering techniques.
- Unrestricted upload of file with dangerous type. This application allows users to upload files with dangerous file types. This vulnerability lets attackers upload or transfer malicious executable files.
Ongoing challenges to AppSec
Beyond these specific techniques, several security challenges or lack of appropriate practices also contribute to security risks. These are common security challenges associated with modern applications.
- Open-source and third-party software vulnerabilities
- Not shifting left with your security approach
- Lack of security awareness and training
- Improper access controls
- No risks assessments
How to ensure AppSec: Common application security requirements & techniques
There are many ways you can secure your applications from common vulnerabilities like the ones we’ve described above. Common AppSec techniques include access control, authorization, validation checks, security testing, and data encryption. Let’s take a look!
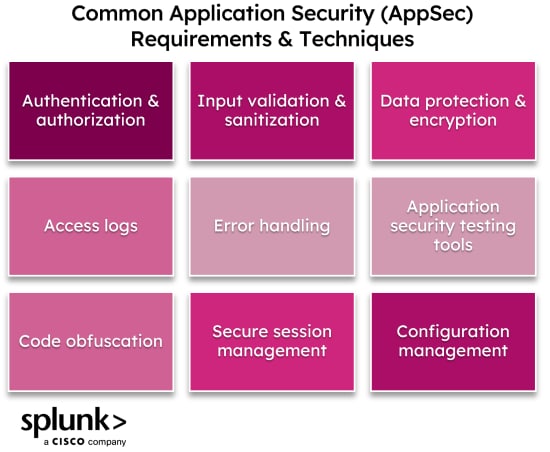
Authentication and authorization
Control access by implementing proper authentication and authorization mechanisms restricting access to applications. As explained in our comparison of authentication and authorization:
- “Authentication is the verification of the identity of an individual, device, or system before granting access to a specific resource or system. Also known as AuthN, this process ensures that the entity that accesses the resource or system is indeed the entity it claims to be.”
- “Authorization means granting permission to access resources or data within a system. AuthZ typically occurs upon the completion of authentication.” A common approach here is enforcing the principle of least privilege — ensuring that only those who need certain sensitive data can access it.
Data protection and encryption
Data protection ensures that sensitive information isn’t accessible to unauthorized systems or individuals. There are two main aspects of data protection:
- Data encryption protects data both at rest and in transit so that only authorized parties can decode it. Encrypt data that flows between the application and the end user. This way, cybercriminals cannot view traffic contents with sensitive data. This also involves encrypting application configurations like database credentials, API shared secrets, system-to-system user credentials, etc.
- Proper data storage and disposal ensures data is securely stored with proper access controls to prevent unauthorized access. Once the data is no longer needed, it needs to be securely deleted and disposed of, so it can’t be recovered and misused.
(Related reading: data lifecycle management.)
Access logs
Maintaining access logs for the application enables organizations to track who accesses the app. This way, it’s easy to identify which IP address occurred in a data breach.
(Learn more about auditing logs.)
Application security testing tools
Different security testing tools allow developers to analyze the code during development and production. These are security testing tools you should incorporate into your application.
- Static Application Security Testing (SAST). Static security testing tools allow developers to quickly identify security vulnerabilities in the code and fix them during development.
- Dynamic Application Security Testing (DAST). These tools can analyze security vulnerabilities in real-time in production environments. DAST tools also enable developers to simulate cyberattacks and reveal detecting runtime errors.
- Interactive Application Security Testing (IAST). This SAST and DAST hybrid provides more accurate security testing results. In this approach, you can analyze the code during any stage of development and in real-time in the production application.
- Run-time Application Security Protection (RASP). These tools allow organizations to run continuous security testing and automate the incident response during security breaches. For example, alerting the security teams, terminating the application to avoid spreading the threat, etc.
When combined, they offer a complete view that will help detect potential vulnerabilities, make the testing process more efficient, and reduce the chance of human error.
(Related reading: software testing 101.)

Code obfuscation techniques
Code obfuscation tools hide the application code so that attackers cannot know the internal functionalities of the application. This technique prevents code tempering and reverses engineering attacks.
Input validation and sanitization
Any data users input into your application needs to be validated and sanitized against every acceptable criterion. Validate user input. This method includes allowing inputs from specific formats and lengths, checking for executables, etc.
This requirement prevents and mitigates attacks such as SQL injection or cross-site scripting (XSS), where an attacker sends malicious data inputs that interfere with the application’s operations.
Secure session management
Your application needs to maintain a secure session for authenticated users. Even with authentication rules in place, poor session management can lead to session hijacking — where attackers take control over the user’s session.
Error handling and logging
How your application handles errors is important information to understand. Detailed error messages can reveal information about the application’s internal workings — and those details can be very useful to any attacker.
Configuration management
An application’s configuration impacts its security. Configuration management should include:
- Confirming that default settings are secure.
- Disabling unnecessary features.
- Regularly updating and patching the application.
Security in the application development lifecycle
Implementing these requirements within the application development lifecycle (ADLC) is crucial. The DevSecOps practice ensures that security considerations are not an afterthought but an integral part of the process from conception to deployment. Here’s how to implement these requirements at each phase of the ADLC.
Phase 1: Planning/requirements analysis. This phase encompasses identifying the security requirements your application must meet. It should include compliance requirements, data security needs, and user privacy. Threat modeling helps identify potential security risks (more on this below).
Phase 2: Design. Develop a security architecture that meets the requirements identified in the planning stage. This architecture should incorporate security controls for identified threats and consider secure design principles like least privilege, defense in depth, and fail-safe defaults.
Phase 3: Implementation and development. Leverage Static Application Security Testing (SAST) to scan the source code for common security problems, like SQL injections or buffer overflows. Focus your code reviews on identifying potential security issues.
Phase 4: Testing. In the testing phase, run security-specific testing. Dynamic Application Security Testing (DAST) identifies vulnerabilities while the application is running. Penetration (or pen) testing can help you determine how well the application withstands an attack by simulating a real-work attack.
Phase 5: Deployment. Conduct a final security review before deployment. After deployment, regularly conduct security audits. Also, patch management is important to ensure that any identified vulnerabilities can be quickly fixed.
Best practices in application security
So far, this article has focused on specific risks and techniques to remedy them. Of course, you can also take a macro approach that helps you make all your development and areas of focus more secure.
Here are common overarching best practices to enable cyber hygiene and resilience across the enterprise.
Integrate security scanning for pipelines
Follow an integrated security approach that triggers security scanning at every code commit or deployment. This makes addressing security vulnerabilities faster. Organizations also must ensure they hire security experts that can realize these CI/CD practices.
(Related reading: vulnerability scanning.)
Use threat modeling
Threat modeling is the process of identifying potential security threats and vulnerabilities that can damage:
- The software application itself
- Relevant defense mechanisms
- Your validation of the security mechanisms against threats
Threat modeling is typically carried out in the design phase of the development process. It helps organizations deeply understand the software architecture, threat agents, potential system damage and security requirements. Threat modeling generally formulates the following artifacts:
- Application diagram
- Attacker profiles and their attacking techniques
- Remediation methods
- Remediation validations techniques
Threat modeling will help your IT take a proactive stance against security breaches and allow for efficiently allocating security resources.
(Related reading: threat hunting.)
Address vulnerabilities in open-source & third-party software
Open-source software, tools, libraries, and modules bring a lot of advantages to software development. However, they can expose your application to a lot of security vulnerabilities. Hence, it is important to keep track of updates from such software and apply security patches as soon as they are released to avoid exposure to cyber threats.
Use security monitoring tools to monitor apps continuously. That software needs to be kept updated to its latest version.
Practice shift-left security
Traditional development (like that in waterfall and certain DevOps environments) considers security only after the development process ends. This scenario often has a few phases:
- Dedicated security teams assess the security of the end product.
- Development teams must wait for the results of the security assessments.
- Dev teams likely have certain work to do to improve and increase security.
- Product deployment is blocked until you appropriately address critical security issues.
The shift-left approach takes a completely different and more efficient approach. It incorporates application security strategies in every development life cycle as well as in every environment from development to production. The result? No delay between addressing security issues and deploying a secure application to production.
Shifting left improves efficiency by detecting potential problems early on when they are less expensive and easier to fix. It also enhances security integration into the code, reduces the likelihood of last-minute hurdles, and prevents major architectural changes late in development.
Provide necessary security training for developers
Your developers play a vital role in application security. The results could be potentially disastrous: so, it’s vital that every developer know what to avoid in coding that could become a security vulnerability.
- Assess developer knowledge to understand the knowledge gap, then provide the necessary security training. Some organizations today have specific mandatory security training courses for every developer to educate on safe coding practices and common security threats like SQL injection or XSS. This information will enable them to write more secure code and reduce the likelihood that they introduce security vulnerabilities.
- Empower your dev teams with expert-led content, like recommended security articles and books, in-person and online security events and the latest research from teams like the Splunk Threat Research Team and SURGe.
Do not ignore: Keep app security front and center
Applications are widely used in any organization—which means they are also a critical consideration of your organization’s security strategy. Application security is not a one-time effort but an ongoing commitment. It involves continuously monitoring, updating, and improving security measures in response to the evolving threat landscape.
See an error or have a suggestion? Please let us know by emailing ssg-blogs@splunk.com.
This posting does not necessarily represent Splunk's position, strategies or opinion.
Related Articles
About Splunk
The Splunk platform removes the barriers between data and action, empowering observability, IT and security teams to ensure their organizations are secure, resilient and innovative.
Founded in 2003, Splunk is a global company — with over 7,500 employees, Splunkers have received over 1,020 patents to date and availability in 21 regions around the world — and offers an open, extensible data platform that supports shared data across any environment so that all teams in an organization can get end-to-end visibility, with context, for every interaction and business process. Build a strong data foundation with Splunk.





