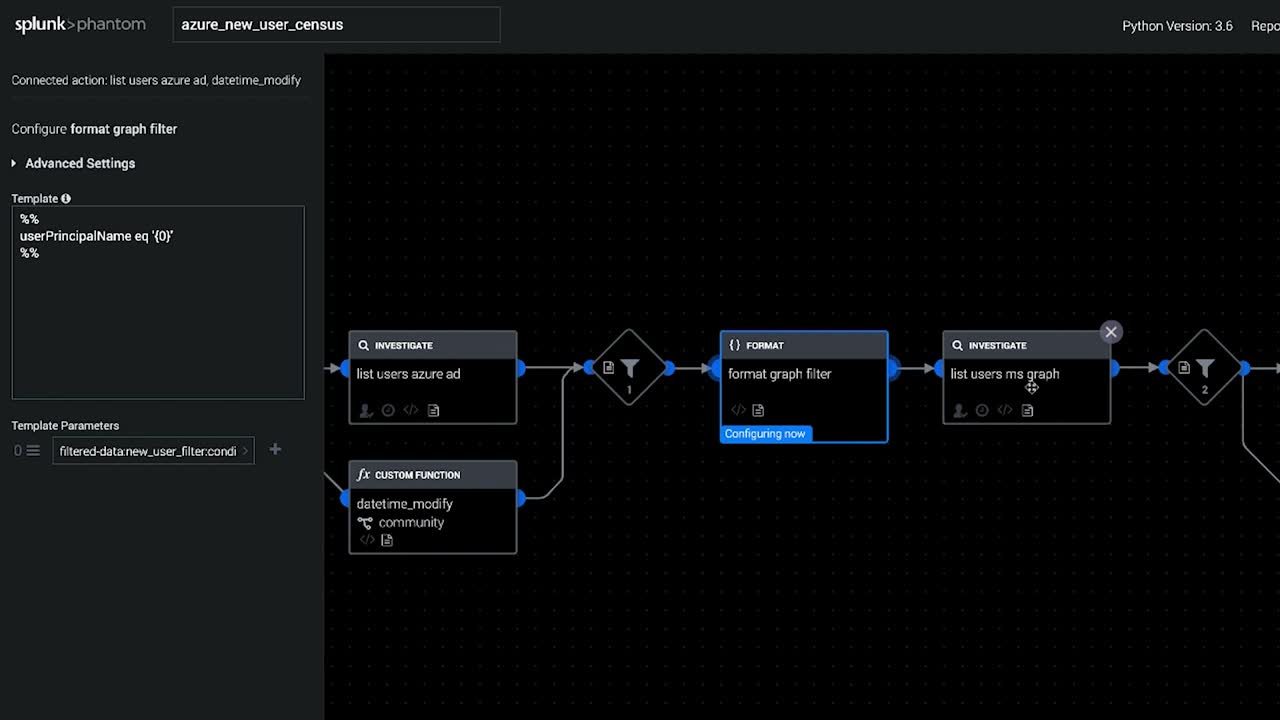
Splunk SOAR Playbooks: Azure New User Census
Hafnium is the latest cyberattack that utilizes a number of post-exploitation tools after gaining access to Exchange servers through a zero-day exploit. One of their persistence methods was creating new user accounts in the domain, giving them the ability to log back into the network using normal authentication rather than use a web shell or continue to re-exploit the vulnerability (which has since been patched). Learn how you can use Splunk Phantom to automate account monitoring to ensure that threat actors are not exploiting vulnerabilities to access sensitive information through authenticated accounts.
If you would like to get the playbook, download the free community edition of Splunk SOAR , and navigate to Playbooks and search for “azure_new_user_census.”
YouTube Tags: security, security orchestration, security automation, SOAR, azure activie directory, active directory, account monitoring, Hafnium, Exchange
If you would like to get the playbook, download the free community edition of Splunk SOAR , and navigate to Playbooks and search for “azure_new_user_census.”
YouTube Tags: security, security orchestration, security automation, SOAR, azure activie directory, active directory, account monitoring, Hafnium, Exchange