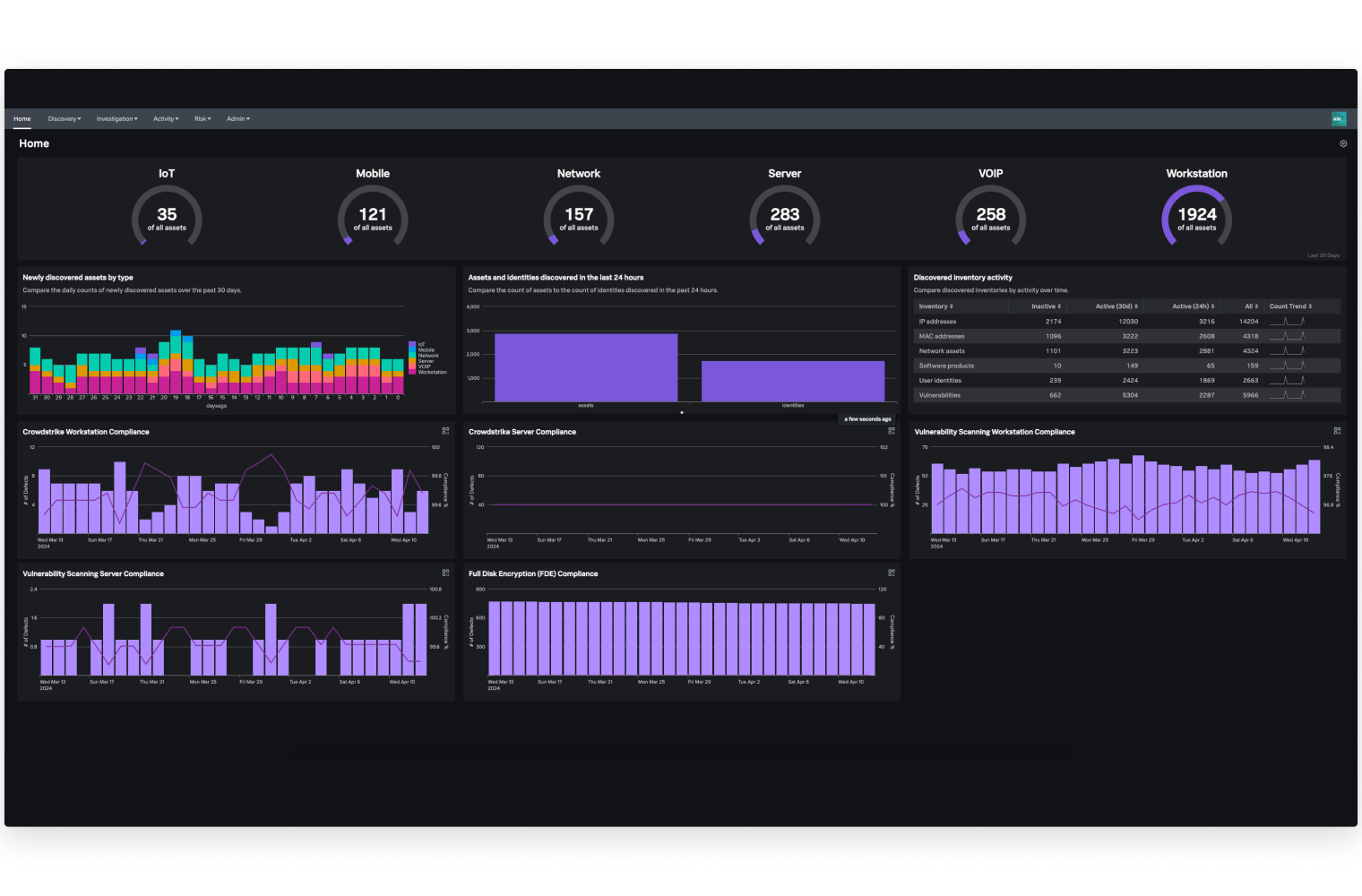
Comprehensive and continuous asset visibility
Splunk Asset and Risk Intelligence provides a unified, continuously updated inventory of assets and identities by correlating data across multiple sources—including network, endpoint, cloud, and scanning tools.
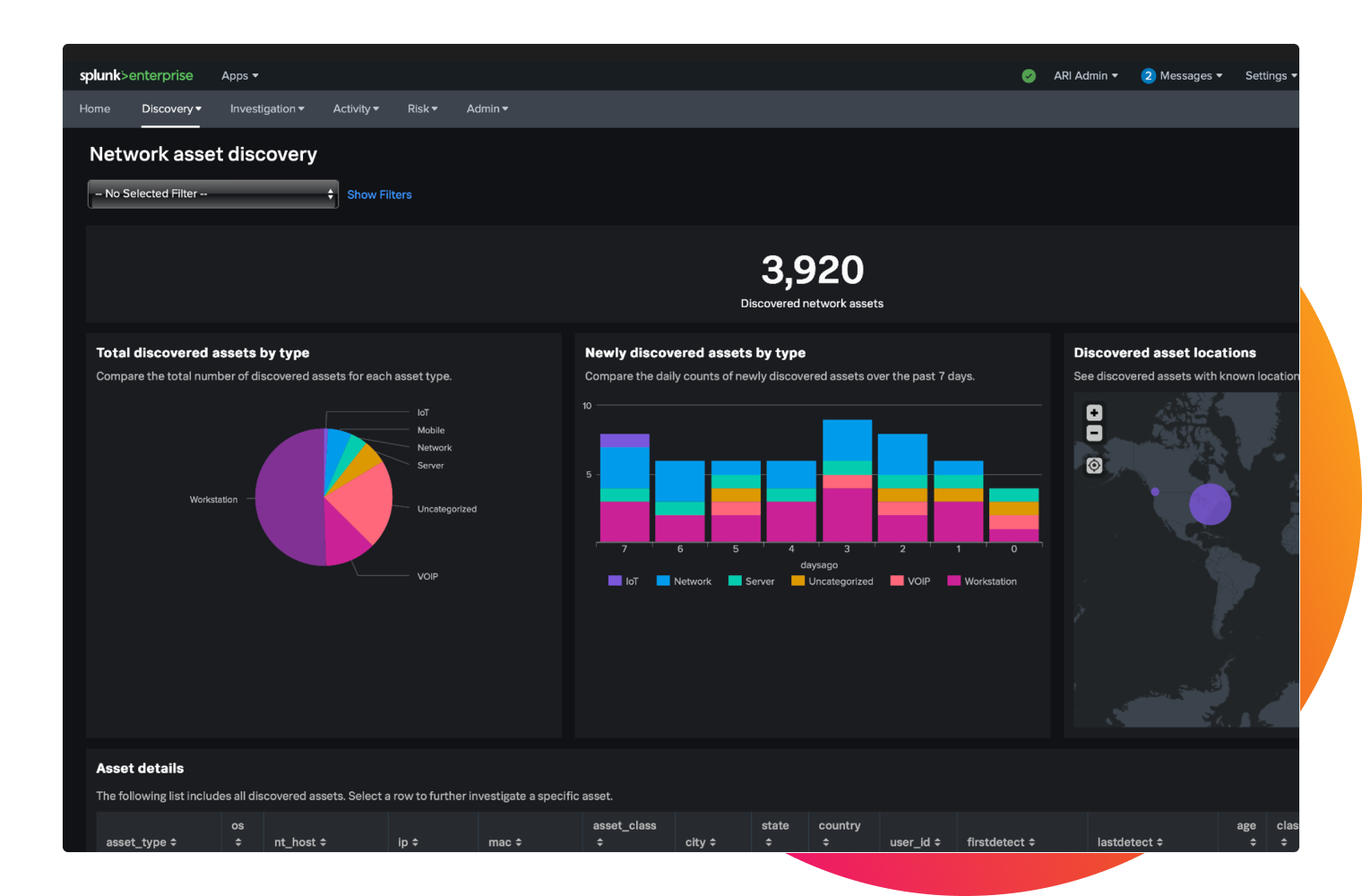

Accelerate security investigations with accurate asset and identity context
The solution provides accurate asset and identity context to focus and shorten investigations so security teams can quickly identify who is associated with what assets and when.
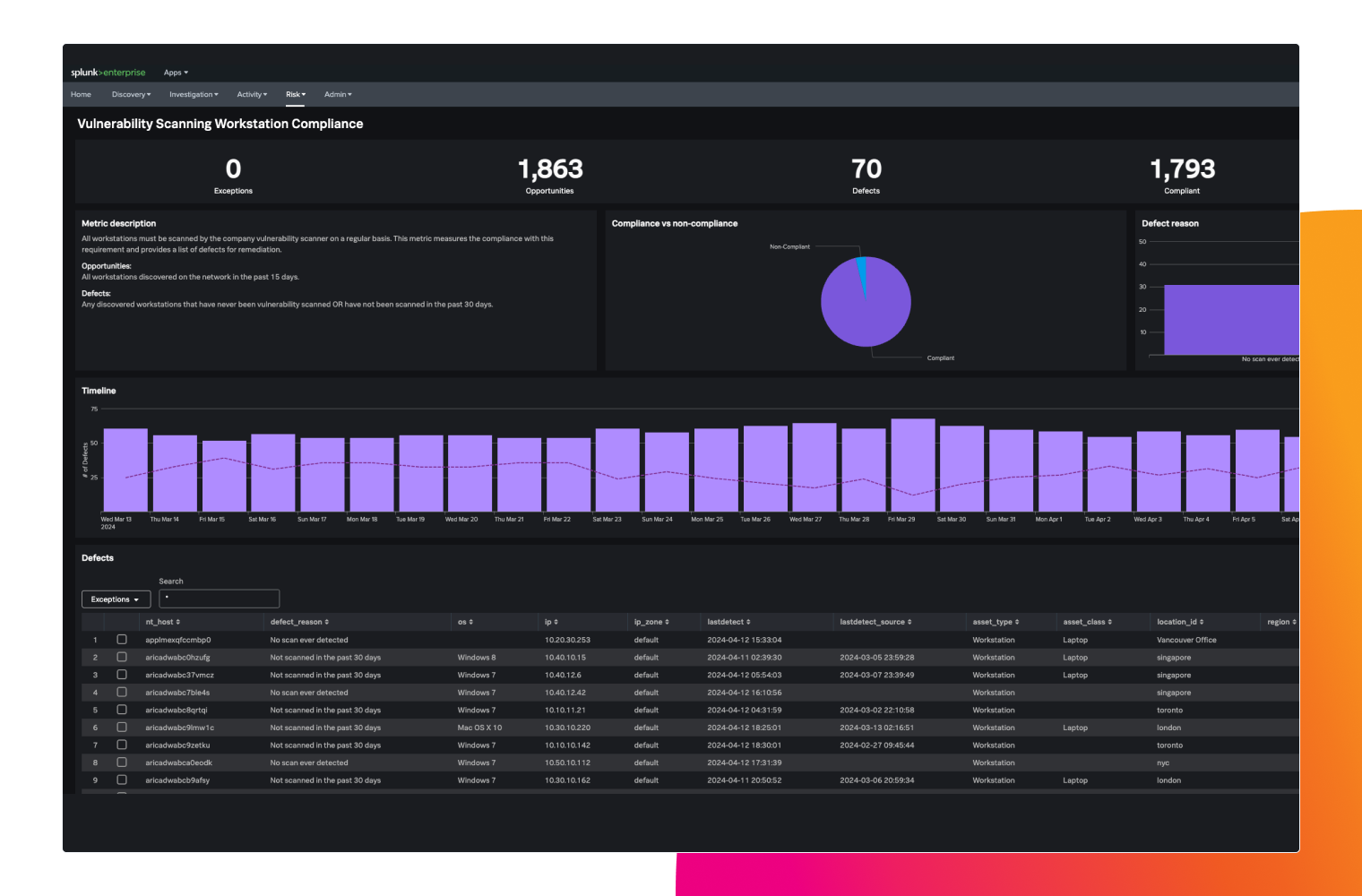
Uncover compliance gaps in security controls
Identify and close gaps in security controls and validate compliance status with out-of-the-box and customizable dashboards and metrics.
Features
Continuous asset discovery and risk intelligence
Accelerate investigations with accurate asset and identity context, identify gaps in compliance, and reduce risk exposure.
Comprehensive, continuously updated asset inventory
Leverage the rich data in the Splunk platform to continuously discover, monitor and build an accurate inventory of assets and identities — including endpoints, servers, users, cloud, OT/IoT, and more.
Streamline and accelerate investigative processes
Reduce the time spent pivoting to other systems to understand the assets involved in the attack and the potential risk to the organization, saving hours of effort and driving more complete and thorough investigations.
Enrich and enhance asset records and associations
Gain more context to assets discovered by correlating data from vulnerability and software scanning tools to inform you about what software and vulnerabilities exist on your systems.
Real-time compliance against security controls
Utilize out of the box or custom compliance metrics such as laptop encryption, vulnerability scanning coverage, application enforcement, malware protection, and more to report on real-time compliance against security controls.
Seamlessly integrate with Splunk Enterprise Security
Continuously update and populate the Splunk Enterprise Security Assets & Identities framework with the latest asset information, and provide comprehensive asset context for notable event enrichment.
Enhance asset visibility across IT and SecOps with bi-directional ServiceNow CMDB integration
Update ServiceNow asset records with what is being actively discovered by Splunk Asset and Risk Intelligence. Identify unmanaged devices that are not in ServiceNow and populate the CMDB to ensure they are managed.
Splunk Attack Analyzer
Automatically detect and analyze the most complex credential phishing and malware threats.
Splunk Enterprise Security
Market-leading SIEM to quickly detect, investigate, and respond to threats.
Splunk SOAR
Supercharge your security operations center with orchestration, automation and response.