Separating the noise from the real threats
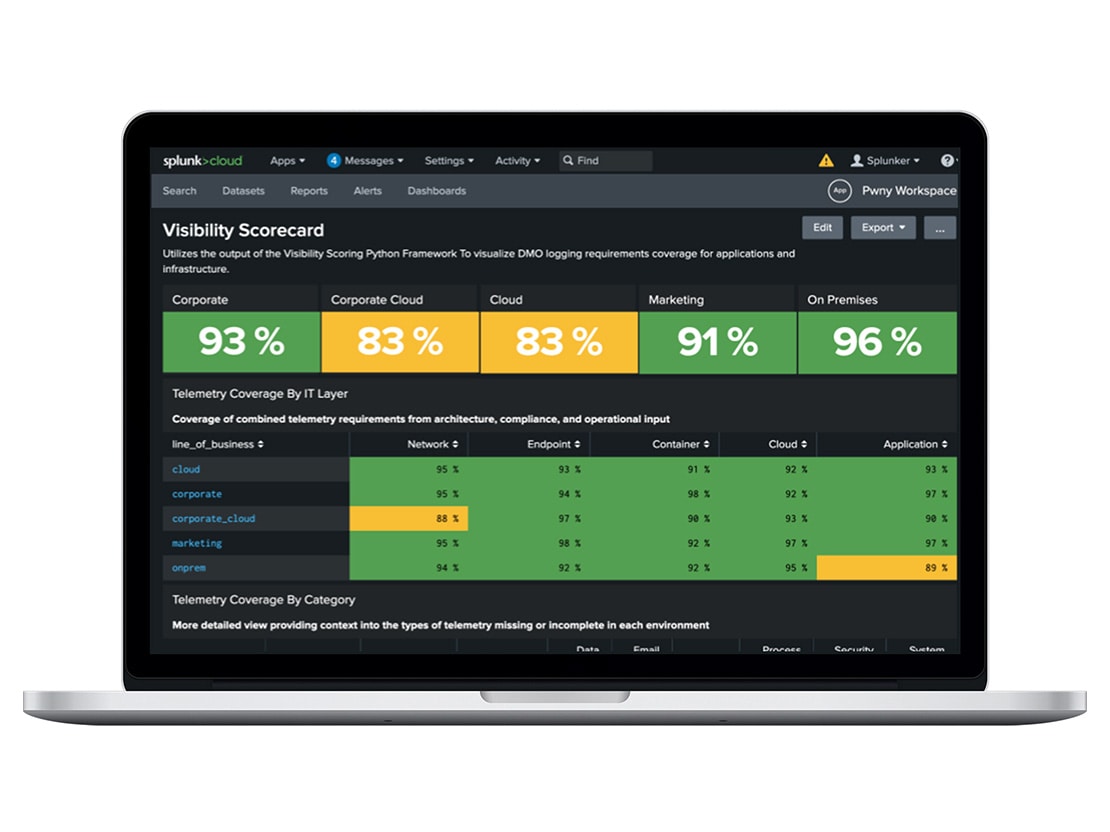
Splunk’s Threat Response team is tasked with being ready to respond to a security event at a moment’s notice — working quickly to ensure the integrity of the company’s security posture. But in an environment where hundreds of alerts are triggered weekly, it’s a challenge to separate the real bad news from the noise.
With Splunk SOAR, our team optimizes threat response by reducing manual operations — while also keeping costs down in the process. With playbooks to run repeated searches and automate enrichment workflows, team members can focus on critical, strategic projects, not time-consuming, repetitive tasks. “Since appending details to the search is all done automatically, Splunk SOAR playbooks save analysts from having to hunt around for additional information or jump to another console,” says Matthew Bellezza, senior manager of monitoring operations at Splunk. “This means we can keep SOC efficiency up while keeping costs down even as the business scales.”
These efficiencies increased by reducing the mean time to resolve an incident by as high as 30% across all use cases — and improved MTTR by as much as 84% on a single use case. “The speed and depth of analysis is hands down best with Splunk, which makes it the clear first choice for security teams,” says detection engineering senior manager Jonathan Heckinger. “That was true back when I was a Splunk customer, and it’s true today for our Splunk SOC to keep customers and Splunkers protected.”